You're using an outdated browser. Please upgrade to a modern browser for the best experience.
Please note this is a comparison between Version 2 by Conner Chen and Version 1 by WENHUA ZHANG.
Blockchain technology provides a data structure with inherent security properties that include cryptography, decentralization, and consensus, which ensure trust in transactions. It covers widely applicable usages, such as in intelligent manufacturing, finance, the Internet of things (IoT), medicine and health, and many different areas, especially in medical health data security and privacy protection areas. Its natural attributes, such as contracts and consensus mechanisms, have leading-edge advantages in protecting data confidentiality, integrity, and availability.
- blockchain
- security
- privacy
1. Introduction
As the distributed ledger that documents bitcoin transactions, blockchain was initially introduced in 2008, and then the genesis block mined by Nakamoto in 2009 verified the concept of blockchain [1]. The framework concept included the E-cash system based on a peer-to-peer (P2P) network, encryption, timestamp, and blockchain technology [2]. It is a successful application where peers can share values using transactions without the need for a central authority to safeguard consumer privacy and avoid identity fraud [3].
Blockchain technology has been implemented in numerous fields as part of the infrastructure of some businesses that require transparency, integrity, and dependability [4] since its inception, from the initial cryptocurrency to the current blockchain-based application for industry 5.0 [5,6,7][5][6][7]. However, with the massive application of blockchain technology and the continuous development of new technologies, blockchain technology’s challenges and threats are constantly escalating. In Ethereum, a smart contract is a piece of code deployed to the network so everyone can access it [8]. The implementation of blockchain technology in the healthcare sector may encompass all aspects of hospital systems, such as process, supervision, statistics, finance, auditing, and archival materials, as well as provide valuable technical assistance for re-establishing the structure of hospital informatization and workflow. Technological improvements in blockchain from 1.0 to 5.0 [9,10,11,12,13][9][10][11][12][13] make it more suitable and stable for industrial applications and business requirements:
- Blockchain 1.0: the programmable currency represented by bitcoin led the new digital payment system. The decentralized, key-based digital currency transaction model makes it the origin of blockchain technology.
| Advantages | Limitations |
|---|
- Blockchain 2.0:
- based on the programmable society, blockchain-based applications are widely used in social fields such as finance, P2P transactions, information creditable registration, ownership and copyright confirmation, and intelligent management.
| Smaller networks pose the same concern. |
Blockchain technology is applied in the health sector to address security threats, as homomeric encryption is a hot method to secure EHR privacy and security. The comparison of the implementation of blockchain technology and HE is shown in Table 2.
Table 2.
The comparison of the implementation of blockchain technology and homomorphic encryption.
| Ref. | Application Domain | Implemented Algorithm | Summary |
|---|
- Blockchain 3.0:
- it makes blockchain more widely applied to decentralized applications (DApps), and through decentralization, non-tampering, and trusted sharing, improves operational efficiency and the trust level of the society.
- Blockchain 4.0:
- an extension of the last generation to make the DApps more feasible for real-time business scenarios that apply in Industrial Revolution (IR) 4.0, which regulates within the network through the consensus protocol [14,15][14][15].
- Blockchain 5.0: this generation is considered an upcoming generation of blockchain because it reduces the traditional blockchain limitations [16] and the virtual connections for increased processing speed and security [17].
Blockchain 1.0, 2.0, 3.0, 4.0, and 5.0 are not progressive evolutions but are in different application stages. From 1.0 to 5.0, they are all parallel scopes of development playing their due roles in various fields. Figure 1 depicts the scope of technical improvement in blockchain, while Figure 2 shows the comparison between traditional and blockchain transparency networks.
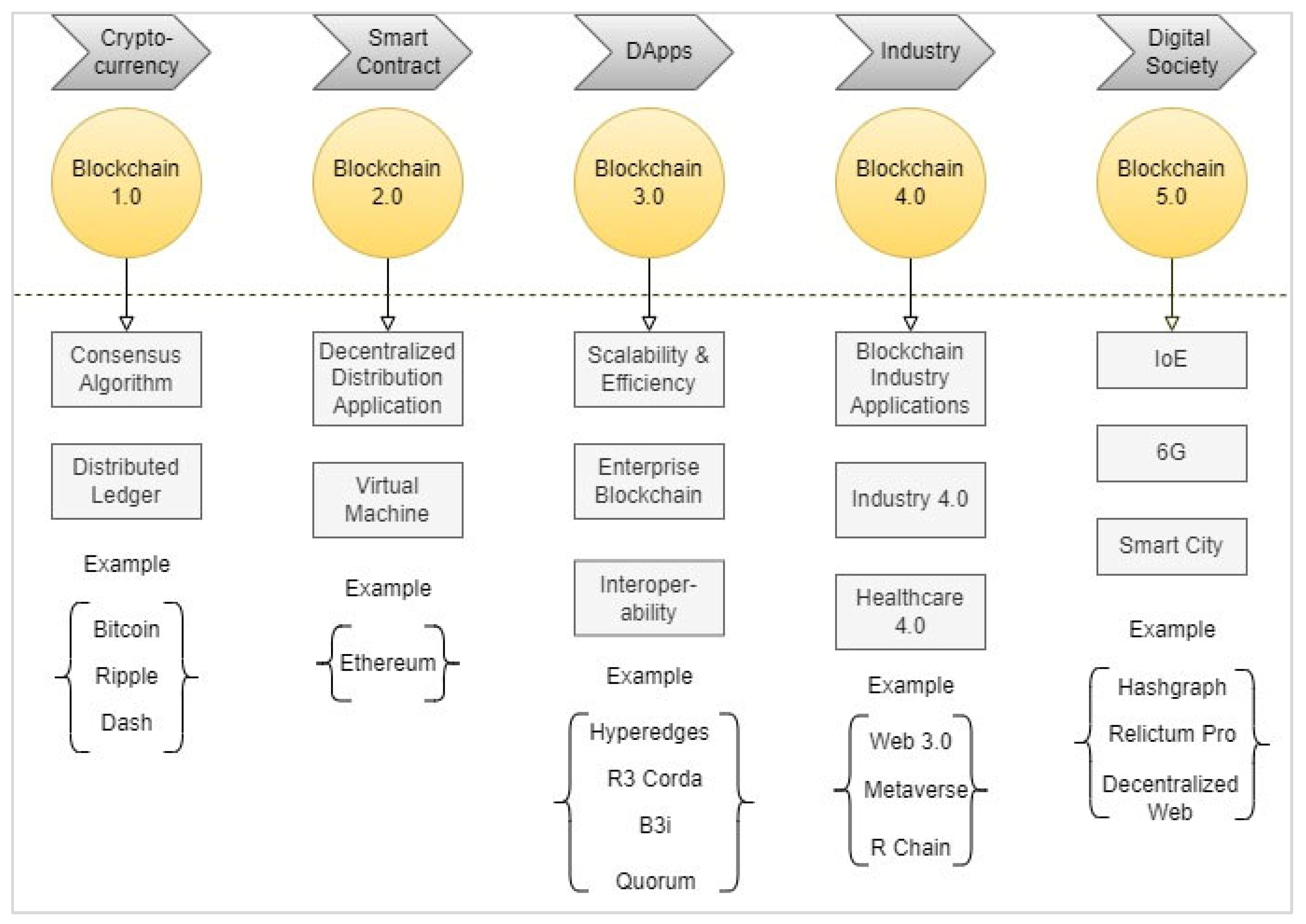
Figure 1.
The scope of technical improvement in blockchain.
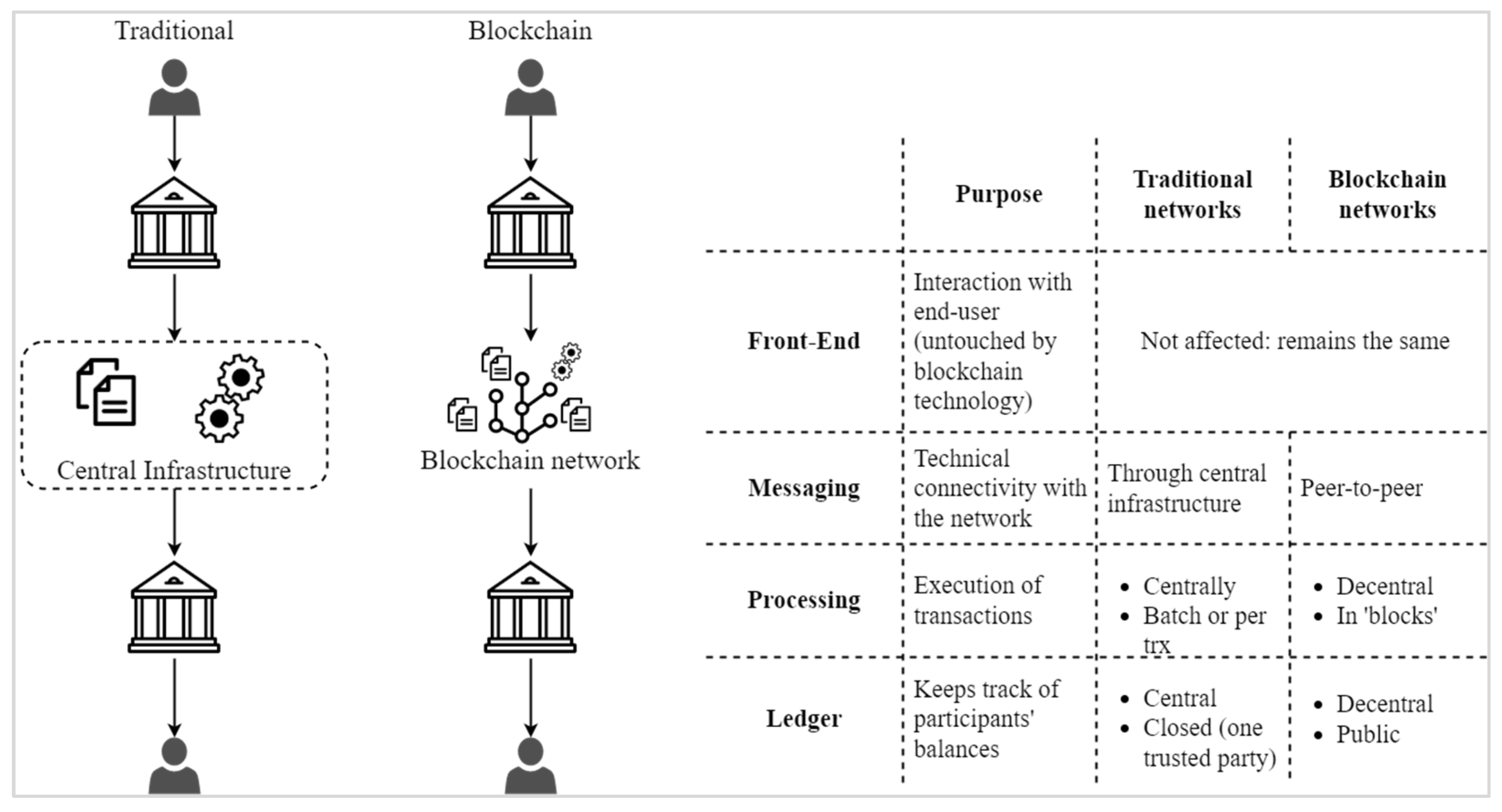
Figure 2.
The transparency network comparison between traditional and blockchain.
Since the release of blockchain 2.0, the technology has been decoupled from currency transactions, and its potential for other financial and inter-organizational interactions has been investigated, referring to applications beyond currency transactions. With increased digitalization, blockchain 3.0 gives additionally distributed storage capacity and scalability without reducing security and aids in the integration of data from various sources without compromising privacy. Transparency is provided without disclosing ownership, interoperability is ensured without introducing unnecessary complexity, and a source of authentication is established. Blockchain technology’s flexibility and multifaceted capabilities provide enormous possibilities for healthcare innovation, integration, and sustainability.
2. The Concept and Features of Blockchain
Firstly, from a technical perspective, blockchain is not a new technology but consists of a series of existing technologies:
- Peer-to-peer network immutable distributed ledger: ensures that the single node ledger is structurally immutable through the data structure of blockchain.
- Security technology such as encryption: cryptography and hash algorithms guarantee the security and privacy of transactions.
- Consensus algorithms: a pure mathematical mechanism for collective verification of blockchain to establish a trusting relationship between all parties and uses technology to ensure that the consensus results.
- Sharing and openness: the system is open to all participants, who have the right to know and equally enjoy blockchain information.
- The consensus: through the voting of particular nodes to complete the verification and confirm transactions in a fraction of the time. If several nodes can reach a consensus without the related interests for a transaction, it considers the network’s consensus.
| Reduce cost and increase efficiency. | |||||
| [ | Cost-effectiveness has yet to be proven. | ||||
| 29] | Healthcare medical claims in blockchain | Paillier encryption scheme | The insurance company sends the request to the hospital to verify the integrity of the patient’s EHR. | Secure, accessible, and real-time. | Insecure with data leaking issue. |
| [30] | Network transactions database. | Regulatory issues and technical challenges. | |||
| Property digital copyright Protection |
- Fair competition:
- the operations of all nodes are calculated by algorithms, and algorithms determine the accounting rights.
- Smart contract: A new concept of the contract was introduced by Nick Szabo in 1994, who called this new contract “smart” because it includes a set of agreements by which contract participants can enforce these commitments. Smart contracts guarantee trusted business deals without third-party involvement, and the main purpose of smart contracts is to provide a security method and reduce transaction costs with other contracts. Therefore, smart contracts ensure that all the transactions between the nodes are credible and reliable
- [18].
Secondly, in principle view, blockchain is a distributed-shared ledger technology, which establishes a decentralized, machine-trusted, and collectively distributed shared ledger system and uses a perfect mathematical solution to develop a mechanism for the trust and consensus of all parties involved.
Blockchain features:
- Authenticity and integrity: each record is recorded truthfully and completely under supervision.
- Safe and reliable:
- data encryption and cryptography mechanisms prevent the data from being tampered with and forged; the complex checksum sharing mechanism ensures integrity, availability, and confidentiality. Multiple attackers are detected through an encryption standard (digital signature) in which every node has its key, and the packet transmission is performed when the key is in a valid state
- [
- 19].
3. Limitations and Challenges of Blockchain Security
Health information is collected with a variety of medical data sources and complicated data forms. Data sharing allows EHR interaction across multiple healthcare platforms, but it also compromises patient privacy. Blockchain technology has several technical obstacles affecting its large-scale and widespread in the healthcare sector [20,21,22,23,24][20][21][22][23][24]:
-
Limited transaction performance and scalability: blockchain’s limited transaction processing capacity and the slow time for transactions to form blocks.
The expansion solutions are as follows:
- Sharding: the idea of sharding is to divide the overall state of the blockchain into different blocks and process them in parallel.
- Off-chain: high throughput of transactions can be achieved by moving the computation and verification process to a separate protocol off-chain; blockchain is used as an agreement layer to manage the sum of a sequence of transactions.
- DAGs (directed acyclic graph): a graph organization consisting of vertices and edges (vertices are purposes within the graph, and edges are methods from one point to a different graph). A DAG guarantees that there are not any cycles that allow acquiring the grouping of nodes along with the topological sequence.
-
Limited privacy protection: blockchain can be tamper-proof and decentralized, but precisely because the user’s ledger is transparent to participating organizations, that is, any organization can access the same data. Unmasked users’ private data on the chain will amplify the risk of user privacy leakage. Currently, in public chain systems such as Bitcoin, all transaction information is public (including transaction amounts). This means it does not meet some regulatory privacy requirements, such as General Data Protection Regulation (GDPR) [25]. There is a need for the following related security technologies to make further breakthroughs:
- Homomorphic encryption: HE encrypts the transaction data and protects it with the public key. The transactions are ciphertext operations, and the final ledger is encrypted and stored. The obtained ledger records cannot be decrypted even if the node was compromised. The process of HE is shown in Figure 3.
- Zero-knowledge proof: ZKP verification can be made without any useful information provided by the verifier and without revealing the proven message to the verifier during the proof process.
| Large prime number (LPN) algorithm | |||
| Blockchain-based auction to protect the property’s digital copyright in an effective and practical way. | |||
| [31] | Genomics, Health, National security, Education | HE, Fully homomorphic encryption (FHE) | The paper presents a list of potential applications for HE in various domains to determine the importance of data privacy and security. |
| Better security against “pushing”. |
- Trusted execution environment:
- the security zone of the principal processor that ensures the code and information loaded inside are secured classification and respectability.
- Storage constraints:
- the blockchain database is stored indefinitely that only can be added but cannot be changed. Consequently, data storage adds a major expense for the circulated network, and each full node must store ever-increasing data endlessly. Thus, storage is an immense obstacle for any real-world application based on a blockchain.
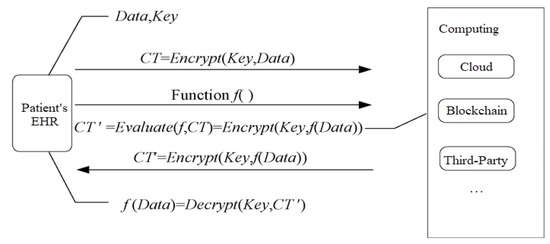
Figure 3.
The progress of homomeric encryption.
At present, the storage solutions of the public chains are as follows:
- Swarm: an Ethereum P2P sharing protocol that allows users to store application code and data in the swarm nodes under the main chain, and then users can access the blockchain to exchange the data.
- The Storj network: files and data are sharded, encrypted, and distributed to multiple nodes so that each node can only store a small part of the data.
| Risk for potential compromise of data set. | |||
| [ | |||
| 32] | Biomedical sensitive data sharing in the public cloud | El Gamal, Discrete Logarithms | The proposed solution brings a new simple model to minimize the risk of sharing medical data in the public cloud, the limitation of this model is that it needs to run online. |
| Easy communication in the more extensive network. | |||
| [33] | Personal health data collection and storage | BGV scheme, Leveled homomorphic using modulus switching (RLWE) | The author proposed a system that applied HE to secure personal health data collection, storage, and transmission in the cloud. |
| [ |
- The IPFS:
- an optional peer-to-peer hypermedia protocol that provides a high-throughput block storage model based on content-addressable hyperlinks. Essentially, it allows files to be stored permanently and distributed while providing historical versions of files, thus removing duplicate files.
- Decent:
- a distributed content-sharing platform that allows users to upload and digitally monetize the sharing of their work (videos, music, e-books, EHR, etc.) without relying on a centralized third party for sharing.
- Alliance chain: the data can be archived in the alliance chain. Blockchain operating system only retains recent data, preserving historical data through archiving.
Table 1.
The advantages and limitations of blockchain technology.
| 34 | |||
| ] | |||
| Healthcare medicine side effect query system | |||
| Smart and Vercauteren, SIMD Style FHE | |||
| A time-efficient privacy-preserving query system model and implementation in a real-world medicine side effect query system. Higher communication cost with or without threads, but still practical. | |||
| [35] | Medical data collection | Fan and Vercauteren, Lattice based leveled homomorphic (RLWE) | HE applied in clinical research to help patients and doctors accelerate learning from real-world |
References
- Hasan, M.K.; Akhtaruzzaman, M.; Kabir, S.R.; Gadekallu, T.R.; Islam, S.; Magalingam, P.; Hassan, R.; Alazab, M.; Alazab, M.A. Evolution of Industry and Blockchain Era: Monitoring Price Hike and Corruption using BIoT for Smart Government and Industry 4.0. IEEE Trans. Ind. Inform. 2022, 18, 9153–9161.
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260.
- Hassen, A.; Abdulhussein, A.A.; Darwish, S.M.; Othman, Z.; Tiun, S.; Lotfy, Y. Towards a secure signature scheme based on multimodal biometric technology: Application for IOT Blockchain network. Symmetry 2020, 12, 1699.
- Jafar, U.; Aziz, M.A.; Shukur, Z.; Hussain, H.A. A Systematic Literature Review and Meta-Analysis on Scalable Blockchain-Based Electronic Voting Systems. Sensors 2022, 22, 7585.
- Khan, S.N.; Loukil, F.; Ghedira-Guegan, C.; Benkhelifa, E. Bani-HaniBlockchain smart contracts: Applications, challenges, and future trends. Peer Peer Netw. Appl. 2021, 14, 2901–2925.
- Bodkhe, U.; Tanwar, S.; Parekh, K.; Khanpara, P.; Tyagi, S.; Kumar, N.; Alazab, M. Blockchain for industry 4.0: A comprehensive review. IEEE Access 2020, 8, 79764–79800.
- Rupa, C.; Midhunchakkaravarthy, D.; Hasan, M.K.; Alhumyani, H.; Saeed, R.A. Industry 5.0: Ethereum blockchain technology based DApp smart contract. Math. Biosci. Eng. 2021, 18, 7010–7027.
- Jafar, U.; Ab Aziz, M.J.; Shukur, Z. Blockchain for Electronic Voting System—Review and Open Research Challenges. Sensors 2021, 21, 5874.
- Khan, G.; Zahid, A.; Hussain, M.; Farooq, M.; Riaz, U.; Alam, T.M. A journey of web and blockchain towards the Industry 4.0: An overview. In Proceedings of the 2019 International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 1–2 November 2019; IEEE: New York, NY, USA, 2019; pp. 1–7.
- Mukherjee, P.; Pradhan, C. Blockchain 1.0 to blockchain 4.0—The evolutionary transformation of blockchain technology. In Blockchain Technology: Applications and Challenges; Springer: Cham, Switzerland, 2021; pp. 29–49.
- Aggarwal, S.; Kumar, N.; Alhussein, M.; Muhammad, G. Blockchain-based UAV path planning for healthcare 4.0: Current challenges and the way ahead. IEEE Network 2021, 35, 20–29.
- Choi, T.-M.; Siqin, T. Blockchain in logistics and production from Blockchain 1.0 to Blockchain 5.0: An intra-inter-organizational framework. Transp. Res. Part E Logist. Transp. Rev. 2022, 160, 102653.
- Kazmi, S.H.A.; Masood, A.; Nisar, K. Design and analysis of multi efficiency motors based high endurance multi rotor with central thrust. In Proceedings of the 2021 IEEE 15th International Conference on Application of Information and Communication Technologies (AICT), Baku, Azerbaijan, 13–15 October 2021; IEEE: New York, NY, USA, 2021; pp. 1–4.
- Moke, K.C.; Low, T.J.; Khan, D. IoT Blockchain Data Veracity with Data Loss Tolerance. Appl. Sci. 2021, 11, 9978.
- Jameel, F.; Javaid, U.; Khan, W.; Aman, M.; Pervaiz, H.; Jäntti, R. Reinforcement Learning in Blockchain-Enabled IIoT Networks: A Survey of Recent Advances and Open Challenges. Sustainability 2020, 12, 5161.
- Hoxha, L. Hashgraph the Future of Decentralized Technology and the End of Blockchain. Eur. J. Eng. Form. Sci. 2018, 2, 86–89.
- Tanwar, S. Blockchain Revolution from 1.0 to 5.0: Technological Perspective. In Blockchain Technology; Springer: Singapore, 2022; pp. 43–61.
- Kairaldeen, A.R.; Abdullah, N.F.; Abu-Samah, A.; Nordin, R. Data Integrity Time Optimization of a Blockchain IoT Smart Home Network Using Different Consensus and Hash Algorithms. Wirel. Commun. Mob. Comput. 2021, 2021, 4401809.
- Talukdar, I.; Hassan, R.; Hossen, S.; Ahmad, K.; Qamar, F.; Ahmed, A.S. Performance Improvements of AODV by Black Hole Attack Detection Using IDS and Digital Signature. Wirel. Commun. Mob. Comput. 2021, 2021, 6693316.
- Barman, N.; Deepak, G.; Martini, M.G. Blockchain for video streaming: Opportunities, challenges, and open issues. Computer 2020, 53, 45–56.
- Qureshi, A.; Jiménez, D.M. Blockchain-Based Multimedia Content Protection: Review and Open Challenges. Appl. Sci. 2020, 11, 1.
- Halpin, H.; Piekarska, M. Introduction to security and privacy on the blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; IEEE: New York, NY, USA, 2017; pp. 1–3.
- Shevkar, R. Performance-Based Analysis of Blockchain Scalability Metric. Tehnički glasnik 2021, 15, 133–142.
- Lange, T. Post-quantum Cryptography. Nature 2017, 549, 188–194.
- Shafiq, M.M. Framework for Social Media Regulations in Pakistan. J. Mass Commun. Dep. Dep. Mass Commun. Karachi U. 2022, 26.
- Sarmah, S.S. Understanding blockchain technology. Comput. Sci. Eng. 2018, 8, 23–29.
- Golosova, J.; Romanovs, A. The advantages and disadvantages of the blockchain technology. In Proceedings of the 2018 IEEE 6th Workshop on Advances in Information, Electronic and Electrical Engineering (AIEEE), Vilnius, Lithuania, 8–10 November 2018; IEEE: New York, NY, USA, 2018; pp. 1–6.
- Mechkaroska, D.; Dimitrova, V.; Popovska-Mitrovikj, A. Analysis of the possibilities for improvement of blockchain technology. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR), Belgrade, Serbia, 20–21 November 2018; IEEE: New York, NY, USA, 2018; pp. 1–4.
- Xu, W.; Wu, L.; Yan, Y. Privacy-preserving scheme of electronic health records based on blockchain and homomorphic encryption. J. Comput. Res. Dev. 2018, 55, 2233–2243.
- Sun, W.; Fang, H.; Zheng, S.; Qian, Q. Blockchain and homomorphic encryption for digital copyright protection. In Proceedings of the 2020 IEEE Intl Conference on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Exeter, UK, 17–19 December 2020; IEEE: New York, NY, USA, 2020; pp. 754–761.
- Archer, D.; Chen, L.; Cheon, J.H.; Gilad-Bachrach, R.; Hallman, R.A.; Huang, Z.; Jiang, X.; Kumaresan, R.; Malin, B.A.; Sofia, H.; et al. Applications of homomorphic encryption. In Crypto Standardization Workshop, Microsoft Research; Sn: Redmond, WA, USA, 2017; Volume 14.
- Raisaro, J.L.; Klann, J.G.; Wagholikar, K.B.; Estiri, H.; Hubaux, J.-P.; Murphy, S.N. Feasibility of Homomorphic Encryption for Sharing I2B2 Aggregate-Level Data in the Cloud. AMIA Jt. Summits Transl. Sci. Proc. 2018, 2017, 176–185.
- Bocu, R.; Costache, C. A homomorphic encryption-based system for securely managing personal health metrics data. IBM J. Res. Dev. 2018, 62, 1:1–1:10.
- Jiang, Y.; Noguchi, T.; Kanno, N.; Yasumura, Y.; Suzuki, T.; Ishimaki, Y.; Yamana, H. A privacy-preserving query system using fully homomorphic encryption with real-world implementation for medicine-side effect search. In Proceedings of the 21st International Conference on Information Integration and Web-based Applications & Services, Munich, Germany, 2–4 December 2019; pp. 63–72.
- Paddock, S.; Abedtash, H.; Zummo, J.; Thomas, S. Proof-of-concept study: Homomorphically encrypted data can support real-time learning in personalized cancer medicine. BMC Med. Inform. Decis. Mak. 2019, 19, 1–10.
More
