Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Rabia Riad and Version 3 by Conner Chen.
Most transactions and exchanges are conducted through the Internet thanks to technological tools, running the risk of the falsification and distortion of information. This is due to the massive demand for the virtual world and its easy access to anyone. Image watermarking has emerged as one of the most important areas for protecting content and enhancing durability and resistance to these kinds of attacks.
- image watermarking
- deep learning
- digital images
1. Image Watermarking Background
Digital watermarking is the process of embedding an invisible mark into digital data, such as an image, audio [1][26], a video [2][27], or text [3][28], etc. This mark is a random sequence of bits, a binary logo, or a message, depending on the application. Information is embedded in digital data by making invisible changes to the content of the data. Watermark detection must be robust even if the watermarked documents are attacked [4][29]. A general image watermarking scheme is shown in Figure 14.
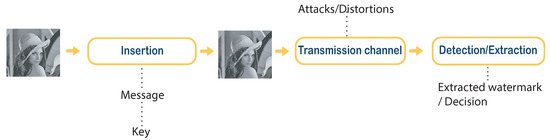
Figure 14.
General scheme of digital watermarking.
There are three major stages to digital watermarking. The insertion phase, the transmission phase (in which attack occurs), and the detection phase (or extraction). During the insertion phase, the mark is inserted into a digital document. After this phase, the original digital document is slightly modified—the modified document is referred to as a watermarked document. In the extraction phase, the mark is extracted from the watermarked document. The extracted mark is then compared with the original mark: if the two marks are identical then the document is authenticated, otherwise, the document is deemed falsified. During the transmission of the watermarked document over a public network, for example, it may be subject to certain attacks, which can alter the document [5][30]. If this alteration is significant enough, it will result in poor decisions.
2. Embedding Phase
In this phase, the original image I0 is combined with the message m, which is a collection of bits encoding the data to be added. This operation’s goal is to create a watermarked image Iw. The watermarked images are perceptually identical to the original images. The message m is encoded using a secret key K to generate a mark W. To maintain the imperceptibility requirement between Iw and I0 [6]I0 [31], the mark is then modulated and/or scaled. There are two ways to insert a mark W into an image I0—additive or substitutional.
2.1. Additive Method
The additive approach consists of adding the watermark to the image’s components using one of the mathematical equations listed below [7][32]:
where α controls the watermark insertion strength to maintain the balance between the imperceptibility and robustness requirements. Watermarks can be added directly to the pixels of the original image or to the frequency components after image transformation, such as discrete wavelet transforms [8][33], discrete Fourier transforms [9][10][34,35], discrete cosine transforms [11][36], etc. Figure 2 5 shows the principle of additive insertion.
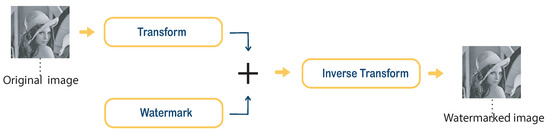
Figure 25.
Embedding by additive method.
2.2. Substitutive Method
In this case, the mark to be inserted is substituted for components of the original image. There are several substitution methods, such as the substitution of the least significant bits (LSB) [12][37], which consists of replacing the least significant bits of the pixels of an image by the bits of the mark. Another technique widely used in image watermarking is quantization by index modulation (QIM), which is proposed in [13][38]. The basic idea behind this technique is to quantize the image using the quantizer that corresponds to the mark to be inserted [14][39]. Thus, each element of the mark is associated with a different quantifier.
3. Detection Phase
3.1. Blind Watermarking
The watermarking technique is qualified to be blind if the hidden information is detected or extracted directly from the watermarked image without requiring the original image [15][40]. Blind watermarking is widely preferred in most applications since the original image is usually not available at the stage of detection/extraction.
3.2. Non-Blind Watermarking
The watermarking technique that requires the original image to extract the mark is called non-blind watermarking [16][41]. It is more robust because the watermark can be easily detected or extracted using both the original image and the watermarked image; however, non-blind watermarking is less popular because it requires the original image.
Figure 3 6 shows the watermark detection/extraction of additive watermarking. The watermark characteristic components are extracted from the watermarked image. The key K is used to generate the reference mark.
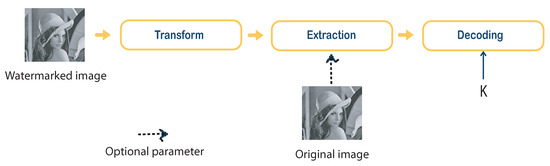
Figure 36.
Detection by additive method.
4. Transmission Phase
The watermarked images are vulnerable to several attacks during the transmission phase, which is the intermediate phase between the embedding and detection/extraction phases [7][32]. Attacks in digital watermarking are defined as the set of operations or modifications that can make the watermark undetectable. There are two major categories of attacks:
4.1. Unintentional Attacks
Any processing or manipulation performed by a non-malicious user is classified as an unintentional attack. The goal of these treatments is to damage the watermark by modifying or hiding some characteristics of the image but not to remove the mark. The following contents will content ourselves to provide the most frequently encountered examples.
-
Compression: Compression attacks are designed to reduce the amount of data encoded in the host document. This process consists of removing the perceptibly less important components while preserving the important components. JPEG and JPEG2000 are considered the most popular image compression algorithms currently in use [17][42].
-
Filtering: Generally, filtering is used for noise reduction. This type of filtering basically has the effect of attenuating the high-frequency components of the image and therefore degrading the brand components inserted in these frequencies.
-
Volumetric transformations: The basic idea behind these transformations is to adjust the brightness value of each pixel in an image using a linear or non-linear function to improve the visual aspect of the image. These transformations include histogram spreading and equalization, Gamma transformation, and so on.
-
Noise: The addition of noise increases the uncertainty or ambiguity of the average information embedded in the image, which can have a masking effect on the watermark and therefore disturb its detection/extraction.
-
Geometric transformations: This kind of transformation does not remove the mark, rather, it makes it undetectable while still remaining in the image. In the majority of watermarking algorithms, the watermark detector requires knowledge of the exact position of the mark in the image. These transformations cause a desynchronization between the mark inserted in the image and the detector [18][43]. There are several geometric transformations, for example, affine geometrical transformations (translation, rotation, and change of scale), and cropping, which consists of removing a part of the image and consequently a part of the mark. There are also local geometric transformations, such as the StirMark attack. This attack consists of a succession of random geometric distortions applied locally to several places in the image [19][44].
4.2. Intentional Attacks
These are specific manipulations meant to intentionally destroy or fake the watermark in order to prevent its extraction/detection. All of the attacks presented above can be used for this purpose.
-
Cryptographic attack: The main goal of this attack is to crack the security codes and algorithms used in watermarking methods in order to remove the inserted watermark information. In this case, the attacker tries to identify the embedded secret key using exhaustive search techniques. This type of attack possesses high computational costs and it is limited, and therefore it is employed less frequently.
-
Protocol attack: The idea behind this attack is to create document ownership ambiguity. Some protocol attacks are based on invertible operations, in which an attacker subtracts their watermark from the watermarked document and claims its ownership. Another type of protocol attack is the copy attack [20][45]. In this case, the goal is to remove the watermark from one container and place it in another target document. In all cases, the attacker can claim for the ownership of both the original and watermarked image.
The second type of attacks is more dangerous. It primarily relates to system security. However, this type of attack is difficult to perceive and thus is omitted in most of the works reviewed. The attack of the first type is considered successful if the watermark is damaged. Accordingly, several counter-techniques have been developed by embedding in the most prominent features of the container. This goes against the concept of improving watermark imperceptibility. Thus, striking a balance between imperceptibility and robustness is a major challenge in creating a watermarking outline.
