Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Antonio Clim and Version 2 by Catherine Yang.
Cities have grown in development and sophistication throughout human history. Smart cities are the current incarnation of this process, with increased complexity and social importance. This complexity has come to involve significant digital components and has thus come to raise the associated cybersecurity concerns. Major security relevant events can cascade into the connected systems making up a smart city, causing significant disruption of function and economic damage.
- smart city
- cybersecurity
- industry 4.0
- industry 5.0
1. Digitalization of Industry 4.0 and Industry 5.0
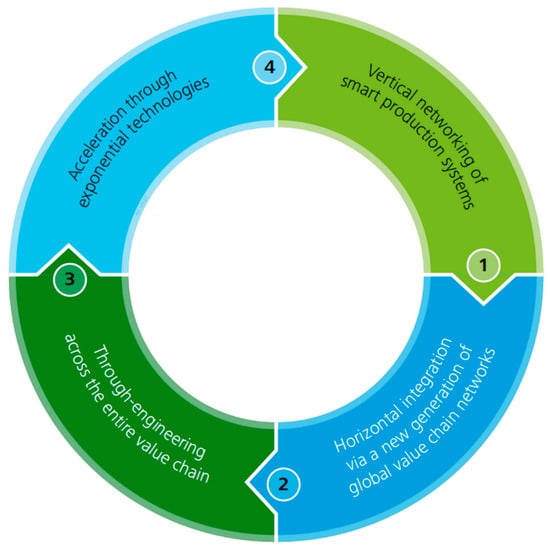
Industry 4.0 is based on autonomous devices and other technologies that have facilitated the production process throughout the value chain. Therefore, this model of a smart factory based on these technological advances includes a section whereby the physical processes of the factory are monitored by systems controlled by computers [1][27]. Such systems have been developed in such a way that they contain a virtual copy of the physical world, producing decentralized decisions based on mechanisms surrounding self-organizations [2][28]. Consequently, this concept will lead to more digitization of the manufacturing industry so that physical objects will be effortlessly integrated into the information technology’s network. Thus, this will enable manufacturing systems to have vertical networking with their relevant business processes within an organization, as well as for the horizontally connected systems to have spatial dispersion value networks which can be regulated in real-time, from the moment an order has been placed up until the outgoing logistics of that particular order. As a result, we have differences across industries and the services offered tend to be less pertinent, since the digital technologies have a connection with the industrial products and services into mixed products, which are considered to be the hybrids, in that they do not only contain goods or services [2][3][28,29]. Therefore, it is worth mentioning how the Internet of Things, as well as the Internet of Services, are deemed the main elements within Industry 4.0 (see Figure 13).
Alternatively, another perspective on Industry 4.0 is with regard to CPPSs, which involve an online network with service machines structured similarly to social networks [5][30]. Therefore, these networks will connect IT with mechanical and electrical components and will communicate with one another through a network. For instance, advancements such as radio frequency identification (RFID) technology have been among the earliest forms of this technology, which has been under use since its inception. In the contemporary setting, smart machines will gradually share information regarding current levels of stock, faults, and issues, as well as changes in orders or demand levels [6][7][8][31,32,33]. Therefore, deadlines and processes are under extensive coordination in order to enhance efficiency, as well as improve capacity application, intime, as well as the quality of production, development, purchasing, and marketing. Therefore, CPPSs will not just network the machines within an industry on a daily basis, they will also develop a smart network surrounding ICT systems, machines, properties, smart products, and stakeholders throughout the life cycle of a product and the value chain [9][10][11][12][34,35,36,37]. Moreover, another significant aspect of Industry 4.0 is the possibility of interacting with other smart infrastructures, such as those associated with smart homes and buildings, smart grid, smart logistics, and smart mobility, as presented in Figure 24.
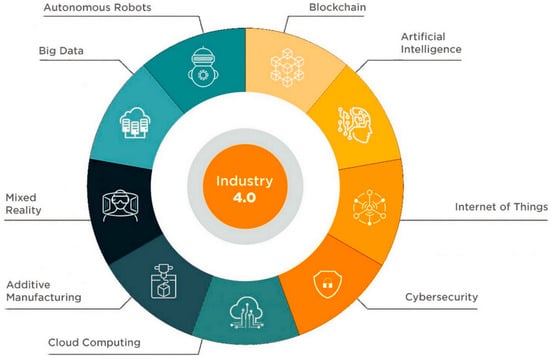
The connection to both business and social networks through the business web as well as the social web will play a mandatory role in the digital transformation of Industry 4.0. Furthermore, these industry-based interfaces and networks will be integrated into the IoT, such as data, people, and services [14][15][39,40]. Therefore, some of these smart industries will depend on various contemporary innovative technological advancements. For example, the application of ICT in the digitization of information and the integration of the system throughout different stages of the development of a product and its appropriate use, such as logistics and supply, is to be made within the company or its limits [16][41]. Second, network communications entail Internet and wireless technologies that allow people, products, and systems to interact, as well as connecting machines in manufacturing industries with relevant suppliers and distributors [6][31]. Third, cyber-physical systems which employ ICT in monitoring, as well as regulating physical systems and processes entail intelligent robots and embedded sensors, since they can be configured to adapt to their immediate product. In other instances, additive manufacturing devices, such as 3D printing devices, are used [17][42]. Moreover, the collection of different quantities of information and their exploitation and evaluation within the factory or by having cloud computing and big data analysis, virtualization, simulation, and modeling within the design of a given product, as well as the development of the manufacturing process, and the immense ICT-based support for the human worker, involve augmented reality, robots and cobots, and other intelligent tools [18][19][43,44]. These tools are represented in Figure 35.

2. Major Vulnerabilities of Digital Technologies in Industries
The nature of cyberattacks directed at contemporary industries is based on targeting of well-known vulnerabilities within digital technologies which are central to Industry 4.0 and Industry 5.0 [21][46]. The first source of vulnerabilities is the continued use of insecure legacy systems that have reduced maintenance. This is common for cities which have been stacking layers of old infrastructure, which depends on old technology and software. Moreover, these systems have not been updated or upgraded in a very long time and they have not evolved into more advanced and secure systems [22][47]. Therefore, having such technologies for industry can give rise to vulnerabilities when it comes to contemporary systems, since they are likely to contain forever-day exploits that are understood to be the loopholes in legacy software products that are no longer supported by their vendors, meaning that the system will never be patched [23][48]. Additionally, even when considering new technologies, it will be hard to determine and roll out the patches on the critical operational systems, which will always need to be on.
Another major vulnerability is the use of weakly tested software, as well as weak data encryption protocols to secure the systems used in these industries. Studies have stated that there are about 30 errors and other exploit bugs in about 1000 lines of code [24][25][49,50], and when it comes to a contemporary heterogeneous system which is being used in industries and smart cities, it has millions of lines of code that have the potential of producing zero-day exploits for various system hacks, malware, and viruses. In addition, studies of industries and smart cities have shown that most of their IT systems were developed without maximum security. Here we refer to the fact that there are no user authentication methods and default or weak passwords are used [26][51]. Furthermore, vendors, stakeholders, and governments within these industries have used their technological systems without conducting in-depth cybersecurity testing and drills, which would have been necessary considering some of the security issues which can arise based on how different systems are operated.
Thirdly, vulnerabilities can produce cascade effects, which can cause cyberattacks, and the factors involve the interrelations between industrial technologies and the system. This creates the grounds to develop various cascade effects through disruptions or failures, hence generating knock-on effects which cause more failure in different significant services, such as utilities. For example, when a telecommunications system is under a cyber-attack, the infrastructure is overloaded, and this may lead to failures of emergency response or traffic management system. Therefore, this makes the issue a significant security risk within an urban operating system, whereby there are various systems that have been interconnected, reflecting a system-of-systems approach in the management of services within the city and its infrastructures. As a result, it will nullify the mitigating impact of using the siloed approach, which is perceived as an entirely individual system, whereby there is a physically independent telecommunication cabling as well as a source of power among other systems [27][28][29][52,53,54]. Therefore, in case there is a successful cyber-attack on the electricity grid in a specific place, there will be sizeable cascading effects because that service supports numerous activities such as distributing power to workplaces, homes, hospitals, and many other infrastructures.
Lastly, human error and intentional malfeasance of dissatisfied personnel within a workplace can be another reason for system vulnerabilities because technical exploits can be immensely assisted by the errors people make. For example, when an employee responds to phishing messages or emails, the insertion of infected external drives into computers and installation of malware and viruses can be some of the ways these actors can play a crucial role towards a cyber-attack [30][31][55,56]. There are other instances whereby the software of a particular infrastructure could be weak in their system designs, in the sense that they can comfortably and secretively be sabotaged with the help of the rogue employees or former employees (see Figure 46). Therefore, it is worth noting that the aforementioned vulnerabilities can be worsened by various factors, considering that at times it is unclear who is mandated to maintain the security across the complex infrastructure and system. Moreover, vulnerabilities also appear when there are many stakeholders and other institutions which have worked together in the development of designs, supplying software and hardware, as well as in the operation and use of different components.
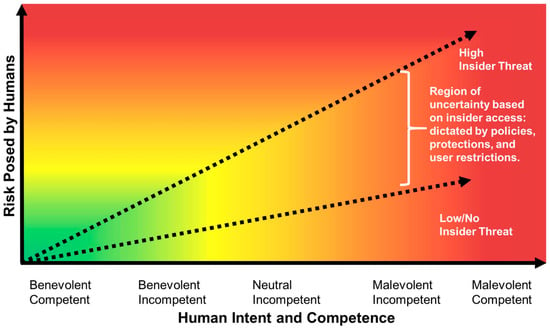
Figure 46. Representation of cyber security risks posed by humans considering the benign or malicious intent and the level of computational competence [32].
Representation of cyber security risks posed by humans considering the benign or malicious intent and the level of computational competence [57].
3. Cybersecurity Risks in Industry 4.0 and 5.0
The technological advancements that constitute the basis for Industry 4.0 have raised various issues concerning their security and overall safety, therefore stating that these developments in the technological paradigm are a direct indication of opportunities and challenges [33][58]. According to the study conducted for the Associated Chambers of Commerce of India (ASSOCHAM) [34][59], Industry 4.0 and Industry 5.0 will prioritize talent over money as a form of investment because the use of elements such as IoT, Artificial Intelligence, blockchain, and other emerging technologies is growing exponentially. These elements can be used to improve governance, consulting, and general digitalization of the major industries [35][60]. The adoption and implementation of these technologies will improve various operational capacities, talent acquisition, and the delivery of applications in various organizations and sectors. Therefore, the process of integrating a concept within an industry is actually about opening up the IT infrastructure of that industry, thus making it more vulnerable to errors and susceptible to cyber-attacks.
Moreover, it is worth noting that cyber intruders will not stop at anything, considering that as the industry advances, they will also refine their techniques for breaching systems [36][61]. As a result, such cyber-attacks targeting penetration into the control systems of various organizations will become a threat to the facilities’ production. In case of such attacks, industry computers are usually controlled from a remote location, and in turn, the intruders can have access or spy on their targeted objective [37][38][62,63]. Such attacks have been made possible by malware that exploits firewalls or security holes, and oftentimes, network monitoring software cannot detect such intrusions.
Considering that these technological opportunities are also in tandem with their associated cybersecurity risks, it would be necessary for industries to have a complete understanding of the impact of adopting these technologies on their security [39][40][41][64,65,66]. For such industries to capitalize on the fourth and fifth industrial revolutions, they will need to have the necessary contingencies and measures in place that will ensure that their cybersecurity is in tandem with Industry 4.0 and Industry 5.0 [42][43][67,68]. Therefore, factors such as integrated data protection frameworks, as well as sector-specific security baselines will help industries find sustainable advantages from their contemporary technological revolution. It is worth noting that the government, as well as other institutions, are also faced with challenges in their cybersecurity, as they are required to have their platforms resilient to threats so that they can facilitate the adoption of ever-changing and disrupting technology [31][44][56,69]. In addition, conventional information security practices could offer the required strategies, but this would not offer sufficient protection for industries considering how technology has been evolving over the years.
Regarding the promise of the impact of cybersecurity plans on organizations, some of the appropriate frameworks that industries can focus on as well as commit to should have some common attributes. For example, the framework should be able to develop capabilities that can detect threats and respond to them adequately and proactively, as well as be able to make use of artificial intelligence in identifying patterns so that IT systems can be monitored through smart technology [45][46][47][48][70,71,72,73]. Such frameworks should also offer an integrated approach towards cybersecurity, whereby there will be a holistic strategy towards the landscape of a threat instead of implementing security technologies in silos. Lastly, it is essential for the framework to create a well-built connection with its respective institutions throughout its sectors and those of the government for the purposes of sharing research, intelligence, information, and capacity development. As these technologies are developing and scaling up, it is essential to involve human resources, training, and education [49][50][51][74,75,76] as the cornerstones of industrial progress, because upon the successful adoption of these technologies, there will be demand for new skills and expertise.