The Interm net of Things (IoT) refers to a system of interrelated, internet-connected objects that are able to collect and transfer data over a wireless network without human intervention. The term IoT has been considered as an expanding technique applied in various applications and functions, from smart environments and houses to personal healthcare and others [1]. It is described as a smart concept for the internet relating everything to the Internet and data organization and information exchange [2]. The key features required for employing a large-scale IoT are low-cost sensors, highspeed and error-tolerant data communications, smart computations, and numerous applications.
- 6G
- spectrum management
- 5G
- Carrier Aggregation (CA)
- Cognitive Radio (CR)
- small cell
- high-spectrum access
- mmWave
- M-MIMO
1. Introduction
Large-scale IoT intelligent systems have become more efficient and effective by using the properties of “symmetry” and “asymmetry”. This can help in a range of IoT applications, for example, in water quality analytics, bee colony status monitoring, accurate agriculture, data communication balancing, smart traffic management, spatiotemporal predicting, and intelligent engineering. Several studies are currently working on IoT technologies to sustain their necessity in platforms developing technology [3]. Although there are diverse definitions and explanations for understanding IoT, it has a subsequent edge associated with the assimilation of the physical world with the virtual one of the internet [4].
The paradigm of IoT is simplified as any-time, any-place, and any-one connected [5]. The implementation of this technology makes things and people closer and everyday life easier [6]. The purpose of IoT is to ensure a connection between devices, where each provides information and data. These devices are generally personal objects that are frequently carried, including smartphones, vehicles, healthcare devices, and office connected devices [7]. Moreover, Radio-Frequency Identification (RFID) is considered to be one of the first applications that saw the light and has played a crucial role in numerous technologies, such as sensors, smart objects, and actuators [8]. However, Machine-to-Machine communication (M2M) [9] and Vehicle-to-Vehicle communication (V2V) [10] represent the actual applications showing the significant advantages of IoT [11][12].
2. IoT Applications
Figure 1 represents a complete taxonomy of IoT in the significant fields of application. The principal areas of application are focused on health care, the environment, smart cities, commercial, industrial, and infrastructural fields [13][14].
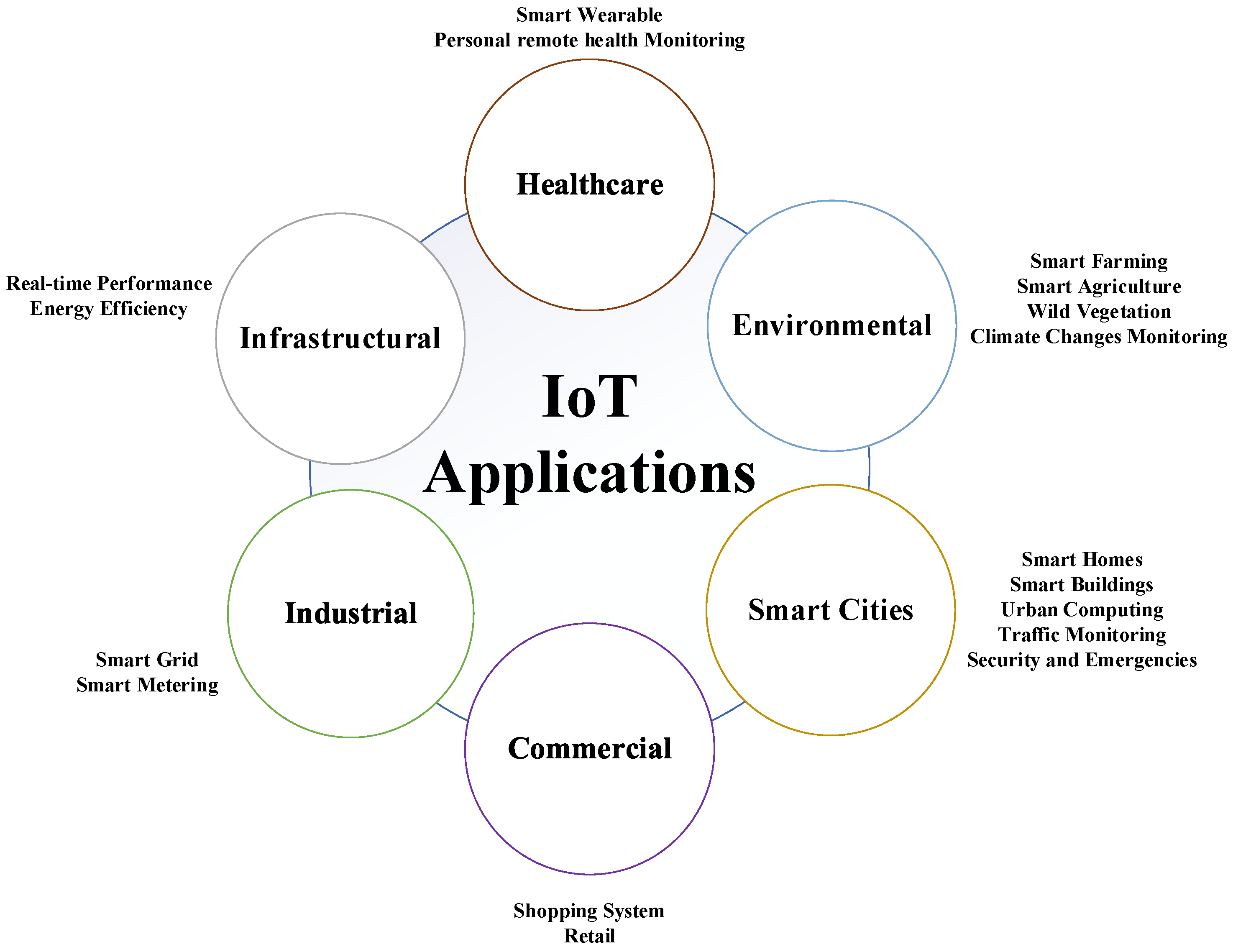
The applications and use of IoT in the different domains are what drive and explain the development of this new trend, leading to the acceptance of IoT by the new world [15]. The study of IoT applications improves the understanding and enhancement of IoT technology, and thus, the design of new systems for newly developed cases [16]. The concept of IoT can be summarized as generating daily information from an object and transferring it to another one. Therefore, enabling communication between objects makes the range of IoT applications extensive, variable, and unlimited [17][18] (Tables 1-6).
Table 1. IoT healthcare applications.
| Reference | Focus Area | Application | Protocol | Device |
|---|---|---|---|---|
| [19] | Disease management system to improve reliability | A guide for IoT healthcare service providers | - | Independent hand-held device and smartphones |
| [20] | Healthcare monitoring for chronic diseases like depression and diabetes | Battery energy efficiency approach using a machine learning technique | - | Wearable devices |
| [21] | Healthcare monitoring system which uses low-cost sensors and ensures a lower energy consumption | New architecture and paradigm of monitoring | XMPP | Smartphone |
| [22] | Mobile medical home monitoring system to improve the rapidity of factor measurements and ensure a low energy consumption | A new paradigm for mobile medical home monitoring | - | Wearable device |
| [23] | Adaptive security management based on metrics to enhance security | Adaptive security management standard | - | Boy sensors |
| [24] | Synthesis method for e-health to ensure high availability | A new structure for e-health | In connection with the patient’s body | |
| [25] | IEEE 802.15.4 transceiver with a low error rate and a higher probability | Framework | IEEE 802.15.4 | Wearable device |
| [26] | An efficient protocol to counter PUEA attacks | Algorithm and structure protocol | Multi-tier device-based authentication protocol | - |
| [27] | Biotelemetry application to ensure lower costs and energy consumption | Implementation and algorithm | - | Wearable antennas |
| [28] | Energy-efficient routing protocol to ensure a lower energy consumption | The path routing protocol in WSN | - | |
| [29] | Super-resolution algorithm for healthcare images with slower response time and cost | - | Multi-kernel SVR learning-based image super-resolution | |
| [30] | Healthcare monitoring system with lower delay rate and time response | A new algorithm for healthcare monitoring system | NB-IoT | - |
| [31] | Human factor evaluation in information exchange in the healthcare environment | It promotes data exchange among healthcare staff and healthcare providers | - | EPR system in hospital emergency department |
| [32] | Healthcare managing system developed through MySignals following LoRa wireless network | Collecting human body data | LoRa | Biosensors attached to the body |
| [33] | Focusing on chronic conditions beyond the office visit | Iraqi health information system | - | Wearable sensors |
Table 2. IoT environmental applications.
| Reference | Focus Area | Application | Protocol | Device |
|---|---|---|---|---|
| [34] | Monitor and control many environmental factors of henhouses in chicken farms | Henhouse system | MAC Protocol | Smart devices |
| [35] | IoT ecological monitoring system | A prototype for wild vegetation environment monitoring | - | Wireless sensor network |
| [36] | The revival of a rural hydrological/water monitoring system | Link located in Tasik Chini | LoRaWAN TCP/IP |
Cellular BS and PC |
| [37] | Design and modeling of a sensible home automation system | Smart home | RFID | Smart home system |
| [38] | A model for smart disaster management using ICT | Smart cities | - | - |
| [39] | Identify critical challenges in ozone mitigation | Department of Environment Malaysia | - | - |
| [40] | Development of a Greenhouse Gases monitoring system | Remote area | - | NetDuino 3 WIFI |
Table 3. IoT smart city applications.
| Reference | Focus Area | Application | Protocol | Device | ||
|---|---|---|---|---|---|---|
| [41] | Semantic-aware mobile crowd-sensing | Service composition in smart city | Cellular | Smartphone and laptop | ||
| [42] | Digital forensics |
| ||||
| [43] | Location finding along with the updated location configuration features |
| LoRa | Sensor device inside an ‘umbrella tube’ | ||
| [44] | Big Data processing | Smart home | Bluetooth low energy (BLE) | MapReduce | ||
| [45] | Analyze and predict the performance of applications used in scalable platforms | Smart home | LoRa | Remote device and server | ||
| [46] | Context-aware service composition | Smart home | wEASEL | Smartphone | ||
| [47] | Cloud computing service composition | Vehicular monitoring | OIDM2M | |||
| [48] | QoS service composition | Smart home | Bayesian networks | Smart devices | ||
| [49] | Manage heterogeneous data streams | Weather systems | ITS | |||
| [50][51] | Traffic management and dynamic resource caching management | Street parking system | CoAP | WSN Devices | ||
| [52] | Real-time low power routing protocol | Smart city | RPL | |||
| [53] | Fog-based architecture to manage IoT applications | 3G/4G Cellular WiFi ZigBee |
Table 4. IoT commercial applications.
| Reference | Focus Area | Application | Protocol | Device |
|---|---|---|---|---|
| [54] | QoS-aware service composition | Ecosystem | SoA | Smart devices |
| [55] | Semantic-aware service composition | Smart homes Smart devices |
6LoWPAN CoAP |
Smart objects |
| [56] | QoS-aware multi-objective service composition | Composite service Optimization service |
- | - |
| [57] | QoS-aware service composition | Optimization service | IP | - |
| [58] | QoS-aware multi-agent composition | Web services | XMPP | - |
| [59] | Service accuracy | IoT Mashup application | RTM and FM | IoT sensors |
| [60][61] | Finance data flow system | Financial and banking sector | NFC | - |
| [62] | Etherum BC | Smart grid | BC | - |
Table 5. IoT industrial applications.
| Reference | Focus Area | Application | Protocol | Device |
|---|---|---|---|---|
| [63] | QoS-aware scheduling for service-oriented IoT devices | Scheduling if IoT | WSN | Mobile devices |
| [64] | Automatic learning of energy profiles and enhancing platform strategy | IoT Fog application | - | - |
| [65] | Content-based cross-layer scheduling | Industrial plant | IEEE 802.15.4-2015 TSCH MAC | - |
| [66] | Nonbeacon-enabled personal area network | Industrial monitoring and automation | IEEE 802.15.4-2015 | - |
| [67] | Ultra-low-power robust cell | Electronics industry | - | TFET SRAM |
| [68] | Concept of prognostics and systems health management (PHM) | Medical industry | - | Smart object appliance |
| [69] | The idea of Industrial IoT (IIoT) focusing on Low-Power Wide-Area Networks (LPWANs) | The indoor industrial monitoring system | LoRaWAN SF 7 LoRaWAN Fair Mod. IEEE 802.15.4 |
Industrial sensors |
| [70] | Industrial Blockchain Tokenizer (IBT) technology | Industrial robot security | Ad-hoc Haye | Sensors |
Table 6. IoT infrastructural applications.
| Reference | Focus Area | Application | Protocol | Device | ||
|---|---|---|---|---|---|---|
| [71] | SDN allocation method and IoT/fog | Very low and predictable latency applications | Openflow | Smart devices | ||
| [72] | Energy-efficient resource management |
| TCP/IP 5G |
Smart devices | ||
| [73] | Resource-efficient edge computing |
| Cellular | Intelligent IoT device | ||
| [74] | Compressed sensing based on reakness for IoT applications |
| - | - | ||
| [75] | Energy-efficient saving rectifier circuits |
| Bluetooth/WLAN | - | ||
| [76] | Low complexity parity checking | Wireless sensor networks | - |
| ||
| [77] | QoS-independent and dynamic management | M2M | Cellular 3G and 4G | PC and smartphone | ||
| [78] | Software update management | Pervasive IoT applications | CoAP | - | ||
| [79] | Hazard-oriented analysis and implementation | Hazard-centric IoT application | - | - | ||
| [80] | Mobile broadband resource allocation in Fog networks | Mobile broadband | Cellular | Smartphones | ||
| [81] | WSDN management system |
| IEEE.802.15.4 IEEE 802.11 |
- |
3. IoT Challenges
Table 7 summarizes the research challenges and opportunities for IoT applications.
Table 7. IoT application challenges and opportunities.
|
IoT Application |
Challenges |
Opportunities |
|
Healthcare applications |
· User’s privacy and data leakage [82] · Standardization challenges [83] · Scalability [84] · Availability [85] |
· Intelligent systems [156] · Wide consumer market demand · IoT-based applications with higher intrinsic value, but longer expected payback on investment [84] |
|
Environmental applications |
· Authentication and authorization [83] · Manage interdependencies between objects [83] · Cost and modularity [86] · Different granularity levels [84] |
· Intelligent systems [83] · Energy sustainability [83] |
|
Smart city applications |
· Authentication and authorization architecture challenges [83] · Technical challenges [83] · Mobility challenges [87] · Interoperability [88] · Big data analytics [88] |
· Safety [89] · Mobility-as-a-service [89] · Traffic management and parking [89] · Smart grid [90] |
|
Commercial applications |
· Privacy and security challenges [83] · Encryptions vs. efficiency [88] · Cost efficiency [91] · Weakness in implementation methods [91] |
· Exponential business growth [82] · Internetworking [82] |
|
Industrial applications |
· Authentication and authorization [82] · Hardware challenges [83] · Efficiency and product loss [82] · SW/HW and data attacks [82] · Lack of willingness to share information [83] |
· Smart factories [82] · Smart grids [82] · Intelligent coal mine [83] · Energy sustainability [83] · Smart factories [83] |
|
Infrastructural applications |
· Standardization challenges [83] · Trust management [91] |
· Energy efficiency [92] · Real-time performance [92] |
4. IoT and Next Generation Protocol
The IPv6 suite primary protocol is neighbor discovery protocol (NDP), and is considered a replacement for the address resolution protocol (ARP) function in IPv4 [93]. The IPv6 protocol considers an extremely auspicious protocol for complicated and dispersed network applications in the era of IoT and Industry 4.0. However, its industrial implementation is slowly increasing in smart manufacturing methods [94]. As the number of devices in the network grows, the received data becomes complex and complicated, which requires more efficient approaches to be collected, sorted, and processed to achieve higher QoS values [95]. This has led researchers and developers to focus on designing various smart network protocols with self-organizing, self-management, and self-configure features, which can able full 3GPP standards and establish an uninterrupted network [96].
Moreover, the IoT6, which is the research project of the future IoT, is progressing positively, yet the unification of IPv6 and IoT is struggling with some challenges. The aim is to exploit the potential of IPv6 and related standards to overcome current shortcomings and fragmentation of the IoT [97]. Currently, the prime issue is the need to integrate the IPv6 and corresponding protocol with IoT, which can help to offer various applications such as automation, smart homes, and smart cities. However, due to wish to design an efficient protocol, some of the significant issues, such as the integration, complexity, scalability, security, reliability, flexibility, and homogeneity, need to be investigated for more IoT applications.
5. Conclusions
Various challenges have been summarized: Such as data privacy and scalability for the healthcare applications, authorization and cost issues for environmental applications, mobility and architecture challenges for smart city applications, cost and implementation difficulties for commercial applications, hardware and production problems for industrial applications, and standardization and trust issues for infrastructural applications. It has stated that various IoT applications still need to be exploited, such as blockchain technology, in order to maintain transaction information, enhance the existing structure performance, or develop next-generation systems. This can help to achieve extra safety, automatic business management, distributed platforms, offline-to-online information authentication, and so on. Moreover, the security and privacy characteristics of IoT are the key factors that can lead to its ability to be developed into a universally implemented technology in the future. However, the self-organizing and accessible nature of IoT makes it susceptible to numerous insider and outsider attackers. This may compromise the users’ security and privacy, enabling access to a user’s private data, financial damage, and eavesdropping. Therefore, more advanced optimized algorithms and protocols are required to secure data privacy. It can be concluded that by designing an energy- and cost-efficient intelligent network with potential business growth for IoT systems, the next generation of development technology can be produced.
References
- Mohd Zaki, I.; Rosilah, H. The Implementation of Internet of Things using Test Bed in the UKMnet Environment. Asia Pac. J. Inf. Technol. Multimed. 2019, 8, 1–17.
- Hassan, R.; Nori, S.S.; Othman, N.E. The improvement of the protection for 6LoWPAN in IoT through non-causal hash function scheme. In Proceedings of the 2018 15th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), Chiang Rai, Thailand, 18–21 July 2018; pp. 600–603.
- Whitmore, A.; Agarwal, A.; Da Xu, L. The Internet of Things—A survey of topics and trends. Inf. Syst. Front. 2015, 17, 261–274.
- Ali, Z.M.; Arshad, M.A.B.M.; Bakar, M.A. POLIoT: Internet Of Things Framework In Managing Network Threats At Metro Polytechnic Tasek Gelugor. In Proceedings of the 2018 Cyber Resilience Conference (CRC), Putrajaya, Malaysia, 13–15 November 2018; pp. 1–4.
- Jain, P.; Adrangi, F.; Venkatachalam, M. Cellular IoT Network Architecture. Google Patents US 10,623,942 B2, 14 April 2020.
- Korade, S.; Kotak, V.; Durafe, A. A review paper on internet of things (IoT) and its applications. Int. Res. J. Eng. Technol. 2019, 6, 1623–1630.
- Wu, F.; Wu, T.; Yuce, M.R. An internet-of-things (IoT) network system for connected safety and health monitoring applications. Sensors 2019, 19, 21.
- Pungus, S.R.; Yahaya, J.; Deraman, A.; Bakar, N.H.B. A data modeling conceptual framework for ubiquitous computing based on context awareness. Int. J. Electr. Comput. Eng. 2019, 9, 5495–5501.
- Alsharif, M.H.; Nordin, R.; Abdullah, N.F.; Kelechi, A.H. How to make key 5G wireless technologies environmental friendly: A review. Trans. Emerg. Telecommun. Technol. 2018, 29, e3254.
- Zhang, H.; Lu, X. Vehicle communication network in intelligent transportation system based on internet of things. Comput. Commun. 2020, 160, 799–806.
- Udoh, I.S.; Kotonya, G. Developing IoT applications: Challenges and frameworks. IET Cyber Phys. Syst. Theory Appl. 2018, 3, 65–72.
- Afzal, B.; Umair, M.; Shah, G.A.; Ahmed, E. Enabling IoT platforms for social IoT applications: Vision, feature mapping, and challenges. Future Gener. Comput. Syst. 2019, 92, 718–731.
- Souri, A.; Asghari, P.; Rezaei, R. Software as a service based CRM providers in the cloud computing: Challenges and technical issues. J. Serv. Sci. Res. 2017, 9, 219–237.
- Souri, A.; Rahmani, A.M.; Jafari Navimipour, N. Formal verification approaches in the web service composition: A comprehensive analysis of the current challenges for future research. Int. J. Commun. Syst. 2018, 31, e3808.
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet Things J. 2019, 7, 16–32.
- Tun, S.Y.Y.; Madanian, S.; Mirza, F. Internet of things (IoT) applications for elderly care: A reflective review. Aging Clin. Exp. Res. 2020.
- Redhu, S.; Maheshwari, M.; Yeotikar, K.; Hegde, R.M. Joint Data Latency and Packet Loss Optimization for Relay-Node Selection in Time-Varying IoT Networks. In Proceedings of the 24th Annual International Conference on Mobile Computing and Networking, New Delhi, India, 29 October–2 November 2018; pp. 711–713.
- De Almeida, I.B.F.; Mendes, L.L.; Rodrigues, J.J.; da Cruz, M.A. 5G waveforms for IoT applications. IEEE Commun. Surv. Tutor. 2019, 21, 2554–2567.
- Kim, S.; Kim, S. User preference for an IoT healthcare application for lifestyle disease management. Telecommun. Policy 2018, 42, 304–314.
- Fafoutis, X.; Clare, L.; Grabham, N.; Beeby, S.; Stark, B.; Piechocki, R.; Craddock, I. Energy neutral activity monitoring: Wearables powered by smart inductive charging surfaces. In Proceedings of the 2016 13th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), London, UK, 27–30 June 2006; pp. 1–9.
- Jimenez, F.; Torres, R. Building an IoT-aware healthcare monitoring system. In Proceedings of the 2015 34th International Conference of the Chilean Computer Science Society (SCCC), Santiago, Chile, 9–13 November 2015; pp. 1–4.
- Ding, Y.; Gang, S.; Hong, J. The design of home monitoring system by remote mobile medical. In Proceedings of the 2015 7th International Conference on Information Technology in Medicine and Education (ITME), Huangshan, China, 13–15 November 2015; pp. 278–281.
- Atlam, H.F.; Wills, G.B. IoT security, privacy, safety and ethics. In Digital Twin Technologies and Smart Cities; Springer: Cham, Switzerland, 2020; pp. 123–149.
- Baloch, Z.; Shaikh, F.K.; Unar, M.A. A context-aware data fusion approach for health-IoT. Int. J. Inf. Technol. 2018, 10, 241–245.
- Subrahmanyam, V.; Zubair, M.A.; Kumar, A.; Rajalakshmi, P. A low power minimal error IEEE 802.15. 4 Transceiver for heart monitoring in IoT applications. Wirel. Pers. Commun. 2018, 100, 611–629.
- Lin, S.C.; Wen, C.Y.; Sethares, W.A. Two-tier device-based authentication protocol against PUEA attacks for IoT applications. IEEE Trans. Signal Inf. Process. Over Netw. 2017, 4, 33–47.
- Damis, H.A.; Khalid, N.; Mirzavand, R.; Chung, H.J.; Mousavi, P. Investigation of epidermal loop antennas for biotelemetry IoT applications. IEEE Access 2018, 6, 15806–15815.
- Elappila, M.; Chinara, S.; Parhi, D.R. Survivable path routing in WSN for IoT applications. Pervasive Mob. Comput. 2018, 43, 49–63.
- Jebadurai, J.; Peter, J.D. Super-resolution of retinal images using multi-kernel SVR for IoT healthcare applications. Future Gener. Comput. Syst. 2018, 83, 338–346.
- Malik, H.; Alam, M.M.; Le Moullec, Y.; Kuusik, A. NarrowBand-IoT performance analysis for healthcare applications. Procedia Comput. Sci. 2018, 130, 1077–1083.
- Hamdan, R. Human factors for IoT services utilization for health information exchange. J. Theor. Appl. Inf. Technol. 2018, 96, 2095–2105.
- Shahidul Islam, M.; Islam, M.T.; Almutairi, A.F.; Beng, G.K.; Misran, N.; Amin, N. Monitoring of the human body signal through the Internet of Things (IoT) based LoRa wireless network system. Appl. Sci. 2019, 9, 1884.
- Dauwed, M.A.; Yahaya, J.; Mansor, Z.; Hamdan, A.R. Determinants of internet of things services utilization in health information exchange. J. Eng. Appl. Sci. 2018, 13, 10490–10501.
- Li, H.; Wang, H.; Yin, W.; Li, Y.; Qian, Y.; Hu, F. Development of a remote monitoring system for henhouse environment based on IoT technology. Future Internet 2015, 7, 329–341.
- Kim, N.S.; Lee, K.; Ryu, J.H. Study on IoT based wild vegetation community ecological monitoring system. In Proceedings of the 2015 Seventh International Conference on Ubiquitous and Future Networks, Sapporo, Japan, 7–10 July 2015; pp. 311–316.
- Nordin, R.; Mohamad, H.; Behjati, M.; Kelechi, A.H.; Ramli, N.; Ishizu, K.; Kojima, F.; Ismail, M.; Idris, M. The world-first deployment of narrowband IoT for rural hydrological monitoring in UNESCO biosphere environment. In Proceedings of the 2017 IEEE 4th International Conference on Smart Instrumentation, Measurement and Application (ICSIMA), Putrajaya, Malaysia, 28–30 November 2017; pp. 1–5.
- Yuen, M.C.; Chu, S.Y.; Hong Chu, W.; Shuen Cheng, H.; Lam Ng, H.; Pang Yuen, S. A low-cost IoT smart home system. Int. J. Eng. Technol. 2018, 7, 3143–3147.
- Sukmaningsih, D.W.; Suparta, W.; Trisetyarso, A.; Abbas, B.S.; Kang, C.H. Proposing Smart Disaster Management in Urban Area. In Proceedings of the Asian Conference on Intelligent Information and Database Systems, Yogyakarta, Indonesia, 8–11 April 2019; pp. 3–16.
- Ahamad, F.; Latif, M.; Yusoff, M.; Khan, M.; Juneng, L. So near yet so different: Surface ozone at three sites in Malaysia. EES 2019, 228, 012024.
- Suparta, W.; Alhasa, K.M.; Singh, M.S.J. Preliminary Development of Greenhouse Gases System Data Logger Using Microcontroller Netduino. Adv. Sci. Lett. 2017, 23, 1398–1402.
- Montori, F.; Bedogni, L.; Bononi, L. A collaborative internet of things architecture for smart cities and environmental monitoring. IEEE Internet Things J. 2017, 5, 592–605.
- Zia, T.; Liu, P.; Han, W. Application-specific digital forensics investigative model in internet of things (iot). In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; pp. 1–7.
- Lin, Y.B.; Lin, Y.W.; Hsiao, C.Y.; Wang, S.Y. Location-based IoT applications on campus: The IoTtalk approach. Pervasive Mob. Comput. 2017, 40, 660–673.
- Zeng, X.; Garg, S.K.; Strazdins, P.; Jayaraman, P.P.; Georgakopoulos, D.; Ranjan, R. IOTSim: A simulator for analysing IoT applications. J. Syst. Archit. 2017, 72, 93–107.
- Chen, S.; Liu, B.; Chen, X.; Zhang, Y.; Huang, G. Framework for adaptive computation offloading in iot applications. In Proceedings of the 9th Asia-Pacific Symposium on Internetware, Shanghai, China, 23 September 2017; pp. 1–6.
- Urbieta, A.; González-Beltrán, A.; Mokhtar, S.B.; Hossain, M.A.; Capra, L. Adaptive and context-aware service composition for IoT-based smart cities. Future Gener. Comput. Syst. 2017, 76, 262–274.
- Seo, D.; Jeon, Y.B.; Lee, S.H.; Lee, K.H. Cloud computing for ubiquitous computing on M2M and IoT environment mobile application. Clust. Comput. 2016, 19, 1001–1013.
- Lee, C.; Wang, C.; Kim, E.; Helal, S. Blueprint flow: A declarative service composition framework for cloud applications. IEEE Access 2017, 5, 17634–17643.
- Akbar, A.; Kousiouris, G.; Pervaiz, H.; Sancho, J.; Ta-Shma, P.; Carrez, F.; Moessner, K. Real-time probabilistic data fusion for large-scale IoT applications. IEEE Access 2018, 6, 10015–10027.
- Sun, X.; Ansari, N. Traffic load balancing among brokers at the IoT application layer. IEEE Trans. Netw. Serv. Manag. 2017, 15, 489–502.
- Sun, X.; Ansari, N. Dynamic resource caching in the IoT application layer for smart cities. IEEE Internet Things J. 2017, 5, 606–613.
- Krishna, G.G.; Krishna, G.; Bhalaji, N. Analysis of routing protocol for low-power and lossy networks in IoT real time applications. Procedia Comput. Sci. 2016, 87, 270–274.
- Naranjo, P.G.V.; Pooranian, Z.; Shojafar, M.; Conti, M.; Buyya, R. FOCAN: A Fog-supported smart city network architecture for management of applications in the Internet of Everything environments. J. Parallel Distrib. Comput. 2019, 132, 274–283.
- Alodib, M. QoS-Aware approach to monitor violations of SLAs in the IoT. J. Innov. Digit. Ecosyst. 2016, 3, 197–207.
- Han, S.N.; Crespi, N. Semantic service provisioning for smart objects: Integrating IoT applications into the web. Future Gener. Comput. Syst. 2017, 76, 180–197.
- Huo, Y.; Qiu, P.; Zhai, J.; Fan, D.; Peng, H. Multi-objective service composition model based on cost-effective optimization. Appl. Intell. 2018, 48, 651–669.
- Huo, L.; Wang, Z. Service composition instantiation based on cross-modified artificial Bee Colony algorithm. China Commun. 2016, 13, 233–244.
- Temglit, N.; Chibani, A.; Djouani, K.; Nacer, M.A. A distributed agent-based approach for optimal QoS selection in web of object choreography. IEEE Syst. J. 2017, 12, 1655–1666.
- Cao, B.; Liu, J.; Wen, Y.; Li, H.; Xiao, Q.; Chen, J. QoS-aware service recommendation based on relational topic model and factorization machines for IoT Mashup applications. J. Parallel Distrib. Comput. 2019, 132, 177–189.
- Cuomo, S.; Di Somma, V.; Sica, F. An application of the one-factor HullWhite model in an IoT financial scenario. Sustain. Cities Soc. 2018, 38, 18–20.
- Hull, J.; White, A. Numerical procedures for implementing term structure models I: Single-factor models. J. Deriv. 1994, 2, 7–16.
- Pustišek, M.; Kos, A. Approaches to front-end IoT application development for the ethereum blockchain. Procedia Comput. Sci. 2018, 129, 410–419.
- Li, L.; Li, S.; Zhao, S. QoS-aware scheduling of services-oriented internet of things. IEEE Trans. Ind. Inform. 2014, 10, 1497–1505.
- Venticinque, S.; Amato, A. A methodology for deployment of IoT application in fog. J. Ambient Intell. Humaniz. Comput. 2019, 10, 1955–1976.
- Jin, Y.; Raza, U.; Aijaz, A.; Sooriyabandara, M.; Gormus, S. Content centric cross-layer scheduling for industrial IoT applications using 6TiSCH. IEEE Access 2017, 6, 234–244.
- Kiran, M.S.; Rajalakshmi, P. Performance analysis of CSMA/CA and PCA for time critical industrial IoT applications. IEEE Trans. Ind. Inform. 2018, 14, 2281–2293.
- Ahmad, S.; Alam, N.; Hasan, M. Robust TFET SRAM cell for ultra-low power IoT applications. AEU Int. J. Electron. Commun. 2018, 89, 70–76.
- Kwon, D.; Hodkiewicz, M.R.; Fan, J.; Shibutani, T.; Pecht, M.G. IoT-based prognostics and systems health management for industrial applications. IEEE Access 2016, 4, 3659–3670.
- Luvisotto, M.; Tramarin, F.; Vangelista, L.; Vitturi, S. On the use of LoRaWAN for indoor industrial IoT applications. Wirel. Commun. Mob. Comput. 2018, 2018, 1–11.
- Mazzei, D.; Baldi, G.; Fantoni, G.; Montelisciani, G.; Pitasi, A.; Ricci, L.; Rizzello, L. A Blockchain Tokenizer for Industrial IOT trustless applications. Future Gener. Comput. Syst. 2020, 105, 432–445.
- Diro, A.A.; Reda, H.T.; Chilamkurti, N. Differential flow space allocation scheme in SDN based fog computing for IoT applications. J. Ambient Intell. Humaniz. Comput. 2018, 1–11.
- Naranjo, P.G.V.; Baccarelli, E.; Scarpiniti, M. Design and energy-efficient resource management of virtualized networked Fog architectures for the real-time support of IoT applications. J. Supercomput. 2018, 74, 2470–2507.
- Chen, X.; Shi, Q.; Yang, L.; Xu, J. ThriftyEdge: Resource-efficient edge computing for intelligent IoT applications. IEEE Netw. 2018, 32, 61–65.
- Mangia, M.; Pareschi, F.; Varma, R.; Rovatti, R.; Kovačević, J.; Setti, G. Rakeness-based compressed sensing of multiple-graph signals for IoT applications. IEEE Trans. Circuits Syst. II Express Briefs 2018, 65, 682–686.
- Taghadosi, M.; Albasha, L.; Quadir, N.A.; Rahama, Y.A.; Qaddoumi, N. High efficiency energy harvesters in 65nm CMOS process for autonomous IoT sensor applications. IEEE Access 2017, 6, 2397–2409.
- Alabady, S.A.; Salleh, M.F.M.; Al-Turjman, F. LCPC error correction code for IoT applications. Sustain. Cities Soc. 2018, 42, 663–673.
- Ouedraogo, C.A.; Medjiah, S.; Chassot, C.; Drira, K. Enhancing middleware-based IoT applications through run-time pluggable Qos management mechanisms. application to a oneM2M compliant IoT middleware. Procedia Comput. Sci. 2018, 130, 619–627.
- Kolomvatsos, K. An intelligent, uncertainty driven management scheme for software updates in pervasive IoT applications. Future Gener. Comput. Syst. 2018, 83, 116–131.
- Limonad, L.; Fournier, F.; Haber, D.; Mashkif, N. “Shields”: A Model for Hazard-Oriented Analysis and Implementation of IoT Applications. In Proceedings of the 2018 IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018; pp. 96–103.
- Abedin, S.F.; Alam, M.G.R.; Kazmi, S.A.; Tran, N.H.; Niyato, D.; Hong, C.S. Resource allocation for ultra-reliable and enhanced mobile broadband IoT applications in fog network. IEEE Trans. Commun. 2018, 67, 489–502.
- Bera, S.; Misra, S.; Roy, S.K.; Obaidat, M.S. Soft-WSN: Software-defined WSN management system for IoT applications. IEEE Syst. J. 2016, 12, 2074–2081.
- Sengupta, J.; Ruj, S.; Bit, S.D. A Comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481.
- Chen, S.; Xu, H.; Liu, D.; Hu, B.; Wang, H. A vision of IoT: Applications, challenges, and opportunities with china perspective. IEEE Internet Things J. 2014, 1, 349–359.
- Thibaud, M.; Chi, H.; Zhou, W.; Piramuthu, S. Internet of Things (IoT) in high-risk Environment, Health and Safety (EHS) industries: A comprehensive review. Decis. Support Syst. 2018, 108, 79–95.
- Salman, T.; Jain, R. A survey of protocols and standards for internet of things. Adv. Comput. Commun. 2017, 1.
- Granell, C.; Havlik, D.; Schade, S.; Sabeur, Z.; Delaney, C.; Pielorz, J.; Usländer, T.; Mazzetti, P.; Schleidt, K.; Kobernus, M. Future Internet technologies for environmental applications. Environ. Model. Softw. 2016, 78, 1–15.
- Islam, S.; Khalifa, O.O.; Hashim, A.H.A.; Hasan, M.K.; Razzaque, M.A.; Pandey, B. Design and Evaluation of a Multihoming‑Based Mobility Management Scheme to Support Inter Technology Handoff in PNEMO. Wirel. Pers. Commun. 2020, 114, 1133–1153.
- Mehmood, Y.; Ahmad, F.; Yaqoob, I.; Adnane, A.; Imran, M.; Guizani, S. Internet-of-things-based smart cities: Recent advances and challenges. IEEE Commun. Mag. 2017, 55, 16–24.
- Nambiar, R.; Shroff, R.; Handy, S. Smart cities: Challenges and opportunities. In Proceedings of the 2018 10th International Conference on Communication Systems & Networks (COMSNETS), Banaglore, India, 3–7 January 2018; pp. 243–250.
- Hasan, M.K.; Ahmed, M.M.; Hashim, A.H.A.; Razzaque, A.; Islam, S.; Pandey, B. A Novel Artificial Intelligence Based Timing Synchronization Scheme for Smart Grid Applications. Wirel. Pers. Commun. 2020, 114, 1067–1084.
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294.
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734.
- Obba, P.; Okakwu, I.K. Performance Evaluation of IPv6 and IPv4 for Future Technologies. In Proceedings of the Advances in Information and Communication: Proceedings of the 2020 Future of Information and Communication Conference (FICC), San Francisco, CA, USA, 5–6 March 2020; p. 15.
- Feldner, B.; Herber, P. A qualitative evaluation of IPv6 for the Industrial Internet of Things. Procedia Comput. Sci. 2018, 134, 377–384.
- Sinche, S.; Raposo, D.; Armando, N.; Rodrigues, A.; Boavida, F.; Pereira, V.; Silva, J.S. A Survey of IoT Management Protocols and Frameworks. IEEE Commun. Surv. Tutor. 2019, 22, 1168–1190.
- Cao, J.; Ma, M.; Li, H.; Ma, R.; Sun, Y.; Yu, P.; Xiong, L. A Survey on Security Aspects for 3GPP 5G Networks. IEEE Commun. Surv. Tutor. 2019, 22, 170–195.
- Ahmadi, H.; Arji, G.; Shahmoradi, L.; Safdari, R.; Nilashi, M.; Alizadeh, M. The application of internet of things in healthcare: A systematic literature review and classification. Univers. Access Inf. Soc. 2019, 18, 837–869.
