Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Sajid Shah and Version 3 by Beatrix Zheng.
Encryption is a significant technique to secure data. Steganography and cryptography are two widely used techniques used to secure data. The steganographic technique is used to conceal the confidential information within data, whereas cryptography obfuscates the secret data to make it unreadable. The basic aim of the steganographic technique is to protect the copyrights, authorization, and ownership of the digital media transmitted over a network. A good stego-image should have high embedding capacity, robustness, imperceptibility, security, and less computational complexity.
- RDH (Reversible Data Hiding)
- LSB (least significant bit)
- histogram shifting
- RC4 encryption
1. Introduction
Steganography has numerous applications in various fields including covert communication, image copyright protection (authentication using watermarking), image captions, extra information such as image integrity (fraud detection), subtitles to videos, smart browsers, automatic copyright of the content, copy control in DVD by media, and broadcasting movies [1][2]. In medical imaging, patient’s details are concealed within medical images, thus providing a secure scheme, and lowering the cost of transmission. Steganography has vast applications in defense organizations and intelligence agencies for the safe movement of confidential records. In finance, it is used in smart ID cards where personal identifiable information is embedded in the picture itself for the copyright and security of cards. It is also used in online voting systems to provide secure voting and robustness against a variety of fraudulent behaviors [2][3].
The term “cover image” describes the medium in which secret information is embedded [3][1]. Modern image data hiding uses two basic principles for concealing data, namely the embedding and extraction algorithms. The essential components of the embedding algorithm are a cover image, secret data, and a secret key. Stego-image is obtained by concealing the secret data into the cover image using the embedding algorithm. The stego-image is then used as an input object to extract the secret data [1][2]. Multiple formats are used in image data hiding as a cover image, such as PNG, GIF, TIF, JPEG or Bitmap [2][3]. Image steganography uses image processing techniques for embedding.
The embedding process in data hiding uses a few basic schemes, as shown in Figure 1, and it plays an important role in any stego-image. The commonly used techniques in steganography are based on the spatial domain [4], in which the secret data is directly embedded into the cover image. The other technique used is the transform domain [5], in which the cover image is first converted to another form, such as signals, and then the secret data is embedded. Thirdly, the adaptive scheme [6] specifically works by utilizing the statistical characteristics of an image before the secret information is concealed into a spatial or transform domain. This approach effectively conceals the alteration in an image [7][8][9][7,8,9].
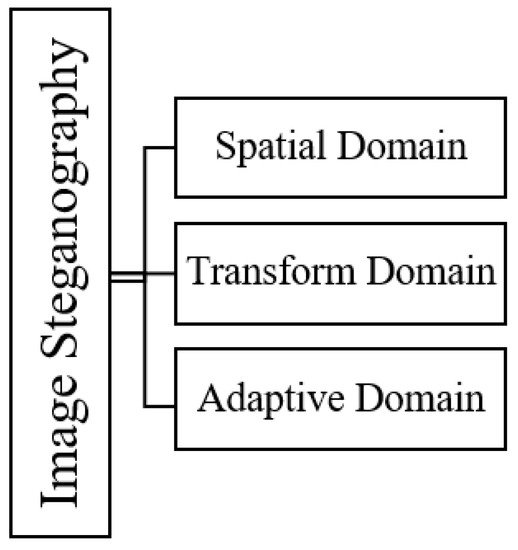
Figure 1.
Categorization of Image Steganography.
The format of the secret data can be either plain or raw, compressed, encrypted, or a combination of both, that can be hidden or concealed within the cover medium [10]. Various cryptographic operations in steganographic schemes have been proposed for the protection of secret data concealed in digital images before transmitting them over a network [11][12][11,12]. For example, modulus operations, AES, map-based scramble techniques, XOR, RC4, RSA, etc. These cryptographic methods are combined with digital image processing data hiding techniques [9][13][14][15][16][17][18][19][20][9,13,14,15,16,17,18,19,20]. However, among various methods of cryptography used, RC4 has many advantages, such as higher computational speed, resilience to cryptographic attacks, and providing stability to histogram values [13][14][15][13,14,15]. Steganography based on RDH scheme is generalized into three methods, namely the compression method, histogram shifting and expansion-based methods [21][22][23][21,22,23]. The proposed scheme uses histogram shifting for concealing secret data bits into the cover image.
A combination of bit-plane slicing, linear prediction and RC4 cryptographic algorithm is used in the proposed scheme to provide high embedding capacity and integrity (security) to the steganographic image by enhancing the visual quality. Primarily, the cover image is divided into 8 bit-planes and a new image is reconstructed using the BPs (bit-planes). The linear prediction is applied over the reconstructed bit-plane image blocks to provide an nBPs residual image, and finally, the histogram shifting is applied to the image to conceal the secret information into the bit-planes residual image (nBPs). Specifically, the histogram of the nBPs residual image is scanned and the peak point (highest value) in the histogram is chosen for embedding. Then the encrypted secret data bits are embedded by shifting the histogram towards the zero point. These procedures make a peak point more concentrated for embedding, thus resulting in good embedding capacity, and the occurrence of the zero values of a histogram is enhanced.
2. Implementation of RDH Schemes Using Image Steganography.
The Reversible Data Hiding (RDH) scheme is initially proposed by M.U.Celik et al. [24] in 2002, which has attracted many researchers due to its vast applications. After extracting the secret data, the cover image is recovered without loss of information. Therefore, this technique is suitable for use in medical and military setups where even a slight image distortion is not tolerable. Ni et al. [9] proposed a novel scheme based on histogram shifting utilizing the RDH scheme. RDH largely operates on four major schemes, including difference expansion, compressive sensing, histogram shifting, and pixel-based methods. The simple illustration of the RDH method is shown in Figure 2. The “Cameraman” image and its histogram are used as an illustration to elucidate the given scheme characteristics [9]. The three steps involved during the embedding process of the scheme are as follows:
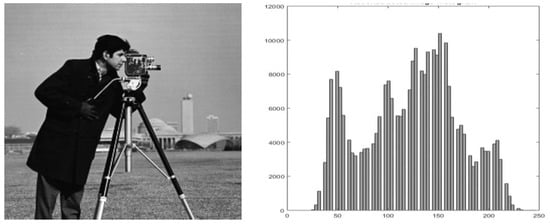
Figure 2.
Cameraman and its histogram.
- Step 1
-
First, the peak values and zero values are searched.
- Step 2
-
Next, the entire image is scanned in sequential order, such as row-wise and column-wise. The values in the histogram are incremented by “1”, shifting towards the right near the zero point.
- Step 3
-
Finally, hiding the secret data in the peak points of the histogram.
The peak points of the histogram, having the highest pixel values, are first searched. If the algorithm encounters “1”, the peak point will be incremented by “1”, and the histogram is shifted towards the right. If the algorithm encounters “0” as secret data, the peak point will remain unchanged. Finally, the stego-image is obtained by applying the embedding process and the stego-image can be transmitted on the internet by applying the RDH basic scheme.
However, the embedding capacity was restricted due to an inadequate number of peak point pixels. Nowadays, the research in RDH has become quite significant and several schemes are proposed. These schemes are divided into two major categories: spatial and transform domain of image steganography.
2.1. Spatial Domain RDH
Zhang et al. [21] proposed a novel technique of RDH in encrypted images. Rashmi et al. [25] used the RDH scheme. They first encrypted the secret text with the AES encryption which is a symmetric key cryptography and embedded the key along with the cipher text. Then the resultant cipher bits are inserted into the cover image using a simple LSB replacement method. The use of encryption has improved security. RDH solely has restricted embedding capacity due to its reversible nature [4]. Lui et al. [26] proposed RDH based histogram shifting. First, the cover image is used to extract nBPs (n number of bit planes) and separated them into BPTI (Bit plane truncation image) to convert them into blocks. The secret data is concealed by using the peak points of each block of the reconstructed bit-planes histogram. Tsai et al. [27] used histogram shifting with predictive coding based on RDH to improve embedding capacity. The authors modified the classic histogram shifting, they applied predictive linear coding on the cover image. This is carried out by finding the difference of basic pixels with all the other pixels of the image. The secret data was concealed into the difference histogram obtained through linear prediction. Kuo et al. [28] proposed the RDH technique using blocks of an image for histogram shifting. In this scheme, the non-overlapping selected cover image is transformed into four blocks. The histogram of each block is taken and shifted, and secret data bits are concealed into a histogram of blocks. The data extraction was used as the inverse for gathering information from the embedding procedure. The embedding capacity was eventually increased but this scheme exploited the cover image. This did not provide enough security to the cover image as the secret data was not encrypted. Xiaoyuan et al. [29] proposed a scheme using bit-planes and encryption. Wengui Su et al. [30] used RDH based on pixel value ordering. In this scheme, the authors divided the cover image into two different regions, and then further divided those two regions into non-overlapping blocks, which are classified using local complexity. The secret data is embedded in these overlapping blocks. Patel et al. [31] proposed an LSB based scheme which used dynamic key cryptography by utilizing random key generation to provide security to stego-image. Xiao et al. [32] used RDH based on bit-plane operation with adaptive embedding. In the proposed method, the authors decomposed the cover image into bit-planes. The bit-plane block difference histogram is taken to add the secret data adaptively using the data hider.
2.2. Transform Domain RDH
Ming li et al. [33] have introduced a compressive sensing based RDH technique that used a small number of coefficients. The cover image is converted into several bit-planes to conceal secret. This conversion is also known as patch-level. It only used the reconstructed image of three-biplanes to hide data. The cover image was directly exploited to hide secret data. Iwendi et al. [34] proposed a scheme which uses Key-Split-Watermark based on blind zero watermarking technique for software code protection. The source code is encrypted using a key. The key and the original watermarked code are registered with the Certification Authority (CA) so that, when the code is altered the key would not match with the CA.
2.3. Miscellaneous RDH Schemes
Srivastava et al. [35] proposed a scheme to secure the medical internet of things for sanitizing the explicit /sensitive terms in unstructured medical datasets. They used three steps for data processing that are, dictionaries, regular expression and re-cognition-tagger for the privacy protection of the patients’ data using HIPAA (Health Insurance Portability and Accountability Act) privacy rules. N. Subramanian et al. [36] proposed a scheme based on deep learning methods that includes Convolutional Neural Network-based method, traditional method, and General Adversarial Network-based method to explore image steganography [37]. Z. Qu. et al. [38] proposed a scheme based on quantum image steganography in which they have used exploiting modification direction (EMD) and one secret bit is concealed using EMD into the corresponding carrier pixel-groups using ary-notational system. Chiung-Chen et al. [39] proposed schemes which showed the use of multiple scanning techniques. Fadhil et al. [40] proposed a scheme that uses RC4 encryption and histogram shifting method for medical image processing. Zhengjun et al. [41] used parameters in gyrator and chaotic map for the encryption of double images. Chen et al. [42] analyzed the automation of machine learning to acquire information about the citations and topics published. Wenqiang et al. [43] showed how fix time can be used to protect images and also analyzed the behavior of the system. Zhengjun et al. [44] uses the fractional Fourier transformation for image encryption. It used iterative procedure to transform unit for concealing images.
