Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 2 by Rita Xu and Version 1 by Fahad Ahmad.
Cloud Computing (CC) provides a combination of technologies that allows the user to use the most resources in the least amount of time and with the least amount of money. CC semantics play a critical role in ranking heterogeneous data by using the properties of different cloud services and then achieving the optimal cloud service. Regardless of the efforts made to enable simple access to this CC innovation, in the presence of various organizations delivering comparative services at varying cost and execution levels, it is far more difficult to identify the ideal cloud service based on the user’s requirements.
- cloud services
- ranking
- machine learning
1. Introduction
Cloud Computing (CC) is a form of internet-based computing in which shared, configurable resources are made accessible to computers and other devices as a service. With the increasing popularity of CC, the development of high-quality cloud applications has become a crucial area of research. CC is an architectural style that provides cloud users with on-demand or pay-per-use access to a shared pool of services and computational resources [1,2][1][2]. Consumers and businesses can save money on capital expenditures and operating expenses owing to CC. It offers users a network-based environment that enables the sharing of computations and services independent of location [3].
With the increasing popularity of service-computing technologies, cloud services have emerged as essential resources that are commonly employed in the context of software systems. Using a pay-as-you-go concept, customers can select services that are stored in cloud data centers [4]. When selecting a service, users usually prioritize their own unique functional needs. With the increasing scope of services offered by cloud data centers, there may be multiple potential services that meet the customer’s requirements. Due to the fact that these candidate services may all match the functional requirements, the user may be required to evaluate them from a non-functional perspective (considering characteristics such as availability, security, reliability, and cost, etc.) before making a choice. Among all the non-functional indicators of cloud services, reliability is arguably the most important and should thus be the primary factor when selecting services [5,6,7][5][6][7].
CC is a business model that enables convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with little management effort or interaction from service providers [8]. Through virtualization, CC can support a huge customer base with varying computation needs on the same physical infrastructure. Contrary to prior paradigms, such as clusters and grid computing, CC is service-oriented; it offers virtualized resources on demand as quantifiable and billable utilities [9,10][9][10]. Consider one’s experience with email as an example of CC. The email client, whether it be Yahoo!, Gmail, or Hotmail, manages the hardware and software required to operate one’s personal email account. Emails are not stored on someone’s physical computer; they are accessed via an internet connection, which means they are accessible from any location [11,12][11][12].
Figure 1 illustrates how, in a CC environment, various accessories such as mobile phones, personal computers/laptops, and servers are used to share information via frame relays, routers, and switches [13,14][13][14]. Any subscriber with an internet connection can access the public cloud, as shown in Figure 2. In the simplest terms, public cloud services are those that are made available to clients via the internet by a third-party service provider. The moniker ‘public’ does not always imply that it is free, even if it is possible to utilize it for free or at a low cost. A public cloud does not imply that a user’s data is publicly accessible; public cloud companies often provide means for their users to manage access to their own data [15].
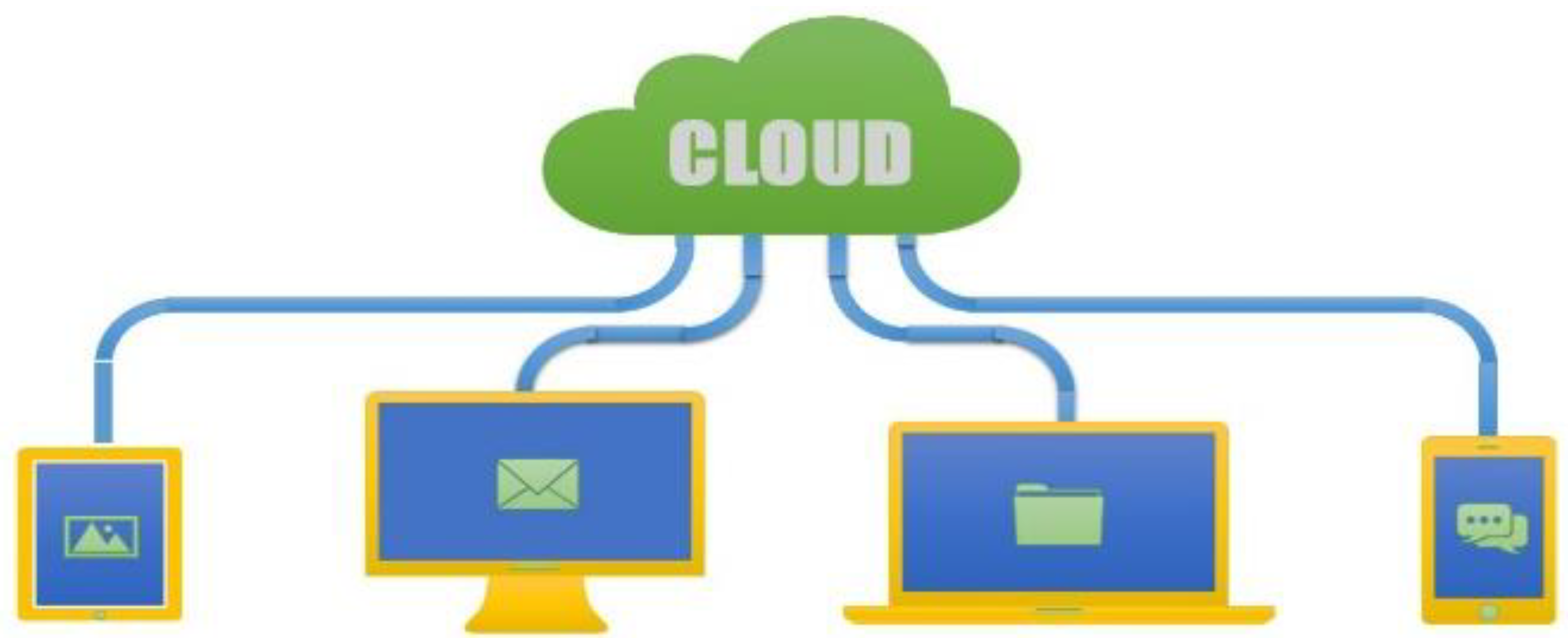
Figure 1. Cloud based computing and communication.
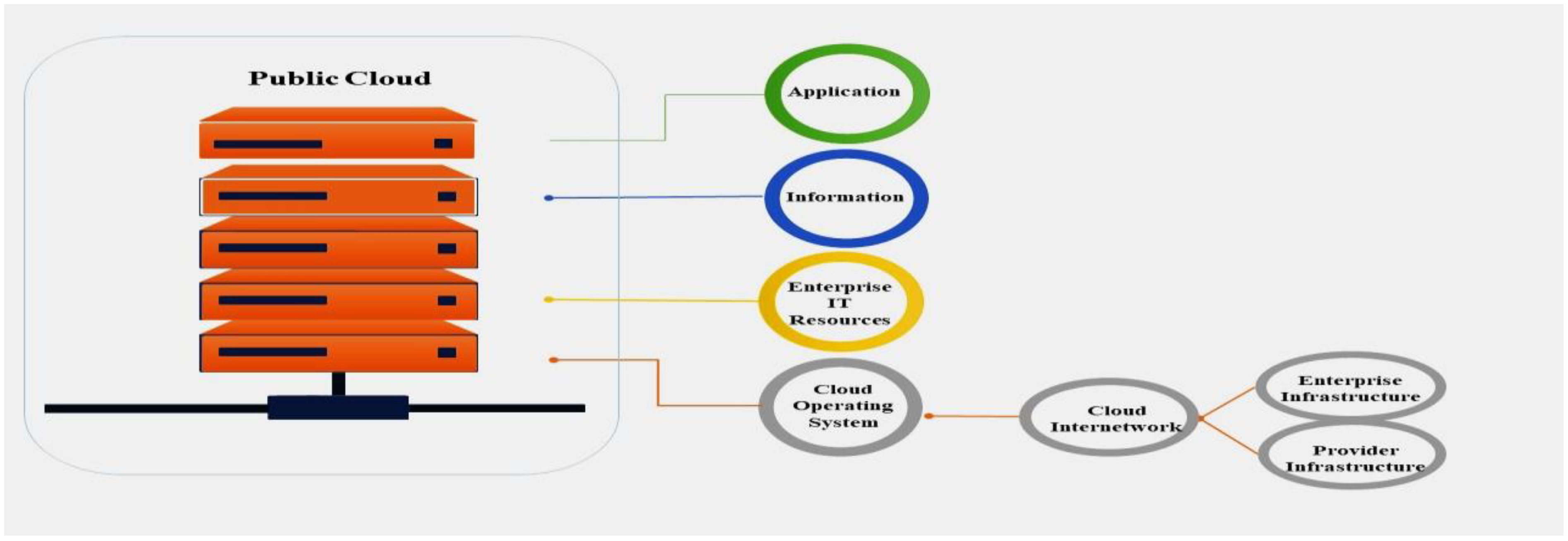
Figure 2. Public cloud computing.
Figure 3 depicts a private cloud that is created for a specific group or organization and restricts access to that group or organization. A private CC environment shares many characteristics with a public CC environment, including adaptability and a service-oriented architecture. The difference between a private cloud and a public cloud is that, with a private-cloud-based service, data and processes are maintained within the organization, without the network capacity, security risks, and regulatory requirements that are associated with public cloud services [16].
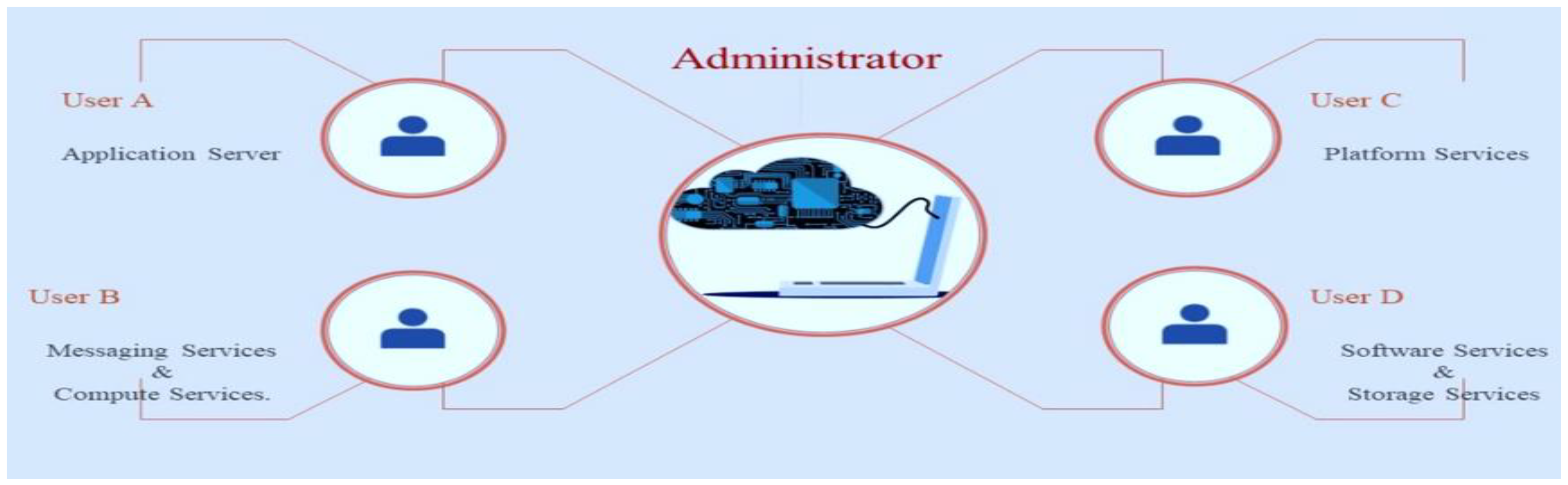
Figure 3. Private cloud computing.
As depicted in Figure 4, a community cloud is a cloud that is shared by two or more enterprises with comparable cloud requirements. A set of organizations with common interests, such as specialized security requirements or a shared mission, will manage and use a community cloud [17].
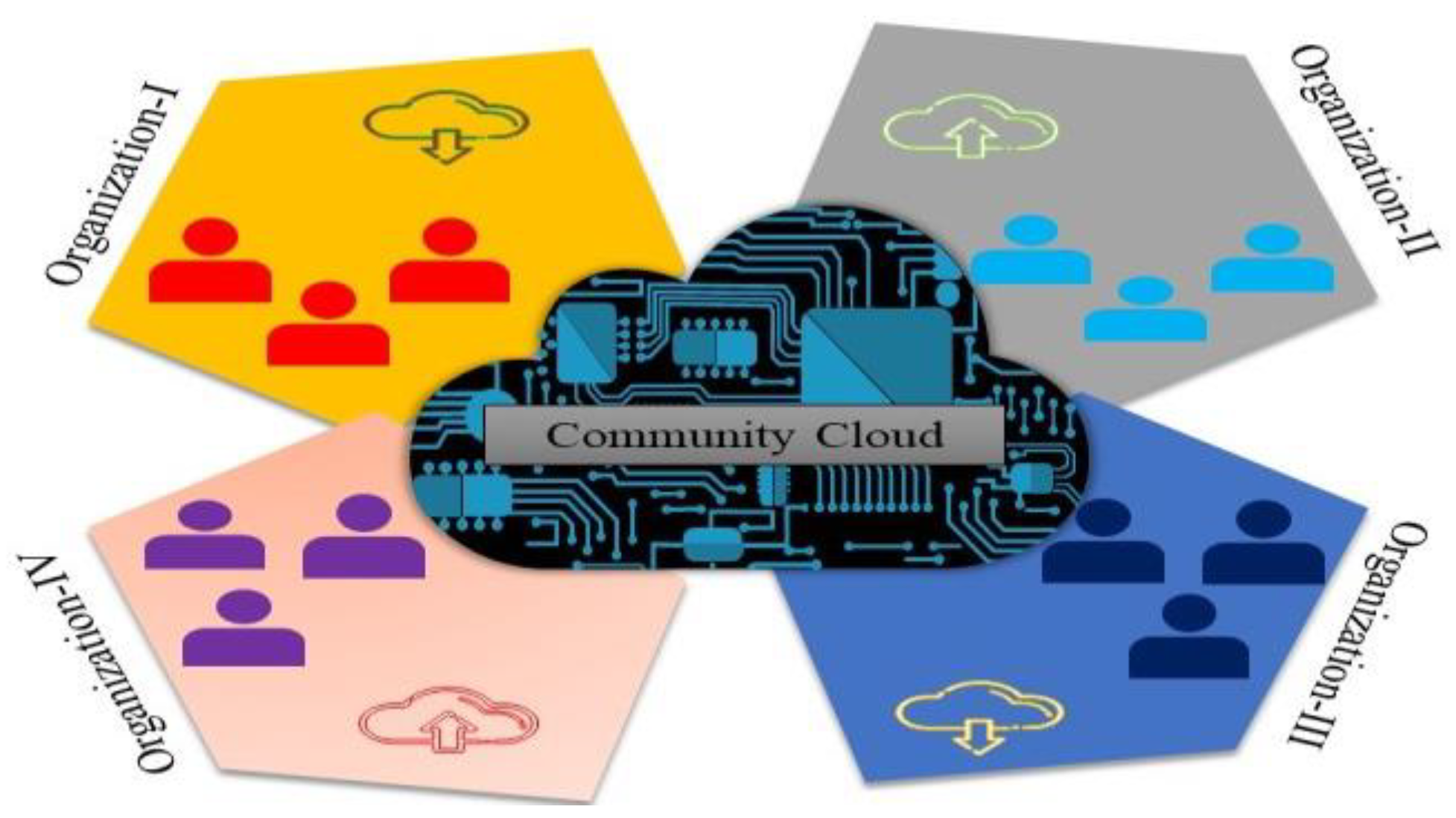
Figure 4. Community cloud computing.
PaaS, IaaS, and SaaS are the three service types that comprise the CC concept. PaaS is a model in which a third-party provider provides hardware and software tools to customers via the internet. These tools are typically necessary during the application development process. PaaS offers an application’s execution environment, such as the Google App Engine, with point-and-click capabilities that allow non-developers to create their own web applications [18,19][18][19]. Second, in IaaS, online services that provide high-level Application Programing Interfaces (APIs) are used to access numerous low-level aspects of the underlying network infrastructure, such as physical computer resources, location, data partitioning, scaling, security, and backup. Thirdly, SaaS enables consumers to access cloud service providers’ applications via a web browser that runs on cloud infrastructure. As a result, end users are not required to download, install, configure, and operate software applications on their personal computing terminals [20,21,22][20][21][22].
Providing rankings involves assigning a value to each option and then arranging them according to that value, with the lowest value representing the best choice. The rank increases as the value decreases. Rankings of cloud services have been gaining popularity over time. However, ranking is subtly different, due to the naming convention and existing cloud infrastructure [23,24][23][24]. When there are numerous service providers, selecting a single CC service can be challenging. It is essential to select the optimal ranking methodology and to evaluate all qualitative aspects of the services [25].
In Artificial Intelligence (AI), the creation of a precise prediction model requires the collection of input characteristics that influence cloud-service rankings. However, a significant portion of the required data is inaccessible or incomplete, due to data source retrieval or significant data loss. Therefore, a model with a high degree of accuracy must be created using a limited number of input parameters [26,27][26][27]. Various methodologies, including deterministic and probabilistic approaches, have been utilized to estimate the global ranking of cloud services. Few studies have employed LR for estimating cloud service rankings, with multiple LR being the most common technique. This model lacks the ability to comprehend the nonlinearity and complexity of the system’s configuration. To determine the ranking of cloud services, it is preferable to use cutting-edge ML algorithms, which are far more effective and require much less computing time and fewer resources [28,29][28][29].
The Machine Learning (ML) tool Waikato Environment for Knowledge Analysis (WEKA) includes an abundance of learning and mining tools. WEKA also makes it easy to test and modify individual learning algorithms to determine which combination of parameters produces the best results [30]. Sequential Minimal Optimization (SMO) is a novel training method for Support Vector Machines (SVM) that divides large problems into as many minor Quadratic Programming (QP) optimization problems as possible [31]. These minor QP issues are resolved analytically, eliminating the requirement for a time-consuming numerical QP optimization in the inner loop. The memory requirements of SMO are proportional to the size of the training set, allowing it to process extremely large training sets, because matrix computation is avoided. SMO scales between linear and quadratic in the training set size for various test problems, whereas the typical SVM technique scales between linear and cubic. SMO can be over a thousand times faster than the typical SVM technique on sparse datasets [32]. For preprocessing, another study utilized wavelet analysis (specifically, the Haar wavelet). It then employed a Support Vector Machine (SVM) via Sequential Minimum Optimization (SMOreg) with Poly kernel function on the updated Quality of Web Service (QWS) dataset to predict cloud-service rankings and model building [33].
2. Cloud Services Based on End-Users’ Feedback
Several pieces of research on CC and ML algorithms highlight their applications in a variety of fields; these have proven to be an invaluable source of guidance for the presented approach of cloud-service ranking. According to the study, CC is an internet-centric software model that represents a shift from traditional single-tenant software development to a flexible, multi-tenant, multi-platform, multi-network, global program. This could be as straightforward as a web-based email service or as complex as a globally-distributed load-balanced content-delivery platform. Moreover, the PaaS, SaaS, and IaaS techniques all aim to solve the same scaling issues [34]. Data centers are typically comprised of a large number of interconnected servers that are clustered in densely populated areas where the risk of a catastrophic event is reduced [35]. According to another study, there are only three types of cloud services: SaaS, PaaS, and IaaS, and enormous scalability is required to fit into any of these categories [36]. According to another study, the cloud concept now encompasses what is possible when using web-scale infrastructure on demand, including: managed services, application services, grid computing, software as a service, platform as a service, and anything as a service [37]. Another study developed a cloud business ontology to aid businesses in locating and selecting suitable cloud services. The development of a paradigm that connects a unified business service and cloud ontology enables enterprises to query for the appropriate cloud service. A unified ontology facilitated the cataloging of desired cloud services and the establishment of a connection between business functions and accessible cloud services. This framework could also be utilized as a service repository [38]. In the presented study, the authors propose a ranking-based collaborative filtering strategy for rating movies. Another research group proposed a ranking-oriented strategy for rating books in digital libraries. That study, unlike previous efforts, provided a comprehensive examination of how to accurately rank cloud services, a novel and urgently required research challenge [39]. In a separate study, an agent- and ontology-based technique for discovering optimal cloud services was proposed. Due to the fact that the proposed method is executed before matching the query with the retrieved services, the online search slowed down the process of discovery [40]. A research group presented a prototype for an intelligent cloud-service-discovery system that combines ontology and the mobile agent. Crawlers with knowledge of the structure, location, schema, and other aspects of the cloud data center were anticipated to have direct access. The test has a high degree of precision but a low degree of recall [41]. In another study, researchers created a cloud crawler engine that crawls through various cloud data centers using cloud ontology. The properties of cloud services are documented, and a dataset is established to contain cloud service descriptions. The evaluation indicated, however, that some cloud service information in the dataset, such as name and URL, was not related to semantic meaning [42]. According to the authors, one of the primary objectives of service selection was to provide a fair analogy between the available services so that users could compare and select the services that best meet their needs based on the functional and technical requirements that the services must fulfill. Examples of functional specifications include completed tasks, pricing policies, and services’ domains [43]. Operating system catalogues, single and multiple operating systems support, and cloud services model are all included in the technical specifications [44]. A study explained that Multiple-Attribute Decision Making (MADM) solutions could be applied to ranking predictions and service selections due to their frequent reliance on numerous QoS factors. Resultantly, numerous management and operation science decision models can be applied to the discovery of trusted services [45]. Another study described that, before presenting a comprehensive best-service decision, the Analytic Hierarchy Process (AHP) relied on a survey form to allow various experts to assign weights to QoS criteria for services. AHP, on the other hand, is still susceptible to subjective factors and difficult to automate [46]. The research described that the Preference Ranking Organization Method for Enrichment of Evaluations (PROMETHEE) technique calculated the weight associated with each attribute using the AHP or the Analytical Network Process (ANP), and then ranked the services based on the weights and preferences of the services related to each attribute. PROMETHEE, on the other hand, demanded a number of pairwise comparisons between services and incorporated subjective weights [47]. Similarly, TOPSIS (Technique for Order Preference by Similarity to an Ideal Solution) has sparked a lot of interest in MADM, since it employed entropy to describe the weight of objective QoS features while also taking consumers’ subjective trust preferences into account. Due to its lower uncertainty, PROMETHEE has been found to be superior to AHP and TOPSIS in experiments [48]. Authors described that numerous decision-making techniques conventionally rank cloud service trust preferences. Even if they could predict the creditability of a service, they only employed static criteria or formulas to calculate the trust rate. However, it is sometimes impossible to adequately characterize the extremely complex nonlinear relationship between a service’s reliability and its strengths using simple mathematical models [49]. In addition, the majority of decision-making models struggle to adapt to these dynamic and shifting conditions. AI has been highlighted as a viable solution for subjective, complex, and dynamic problems [50]. Several AI models, such as the Bayes Network, Classification and Regression Trees (CART), and SVM, have poor predictive capabilities, because the link between QoS attributes and trustworthiness in real-world applications is often complex [51]. The improved SVM-r model has more benchmark features that may enhance prediction outcomes [52]. A research group identified that Artificial Neural Networks (ANNs), can effectively represent complex non-linear relationships and thus have the ability to more accurately predict the reliability of cloud services [51,53][51][53]. Over the years, advancements in the ANN model have been achieved to deliver a solid prediction method. Recurrent design has substantially improved the effectiveness of neural predictors by only using influential factors as input data. The self-adaptive neuro-fuzzy weighted extreme-learning machine was investigated in order to improve prediction performance [54,55,56][54][55][56].References
- Ouyang, C.; Adams, M.; Hofstede, A.H.T.; Yu, Y. Design and Realisation of Scalable Business Process Management Systems for Deployment in the Cloud. ACM Trans. Manag. Inf. Syst. 2021, 12, 36.
- Nadeem, S.; Rizwan, M.; Ahmad, F.; Manzoor, J. Securing cognitive radio vehicular ad hoc network with fog node based distributed blockchain cloud architecture. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 288–295.
- Hameed, U.; Naseem, S.; Ahamd, F.; Alyas, T.; Khan, W.-A. Intrusion detection and prevention in cloud computing using genetic algorithm. Int. J. Sci. Eng. Res. 2014, 5, 1271–1275.
- Rawas, S. Energy, network, and application-aware virtual machine placement model in SDN-enabled large scale cloud data centers. Multimed. Tools Appl. 2021, 80, 15541–15562.
- Mao, C.; Lin, R.; Towey, D.; Wang, W.; Chen, J.; He, Q. Trustworthiness prediction of cloud services based on selective neural network ensemble learning. Expert Syst. Appl. 2021, 168, 114390.
- Hassan, T.; Ahmed, F. Transaction and Identity Authentication Security Model for E-Banking: Confluence of Quantum Cryptography and AI. In Proceedings of the International Conference on Intelligent Technologies and Applications, Bahawalpur, Pakistan, 23–25 October 2018; pp. 338–347.
- Hasan, T.; Ahmad, F.; Rizwan, M.; Alshammari, N.; Alanazi, S.A.; Hussain, I.; Naseem, S. Edge Caching in Fog-Based Sensor Networks through Deep Learning-Associated Quantum Computing Framework. Comput. Intell. Neurosci. 2022, 2022, 6138434.
- Aslam, B.; Abid, R.; Rizwan, M.; Ahmad, F.; Sattar, M.U. Heterogeneity Model for Wireless Mobile Cloud Computing & its Future Challenges. In Proceedings of the 2019 International Conference on Electrical, Communication, and Computer Engineering (ICECCE), Swat, Pakistan, 24–25 July 2019; pp. 1–7.
- Firouzi, F.; Farahani, B.; Marinšek, A. The convergence and interplay of edge, fog, and cloud in the AI-driven Internet of Things (IoT). Inf. Syst. J. 2021, 107, 101840.
- Rizwan, M.; Shabbir, A.; Shabbir, M.; Ahmad, F.; Sattar, M.U. A Clustering based Hybrid Mobility in WPAN. In Proceedings of the 2019 International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 1–2 November 2019; pp. 1–7.
- Soh, J.; Copeland, M.; Puca, A.; Harris, M. Overview of Azure Infrastructure as a Service (IaaS) Services. In Microsoft Azure; Springer: Berlin/Heidelberg, Germany, 2020; pp. 21–41.
- Cheema, A.; Tariq, M.; Hafiz, A.; Khan, M.M.; Ahmad, F.; Anwar, M. Prevention Techniques against Distributed Denial of Service Attacks in Heterogeneous Networks: A Systematic Review. Secur. Commun. Netw. 2022, 2022, 8379532.
- Silverstein, J.C.; Foster, I.T. Computer architectures for health care and biomedicine. In Biomedical Informatics; Springer: Berlin/Heidelberg, Germany, 2014; pp. 149–184.
- IONESCU, A. Security of Computer Networks Implemented in Universities and Business Environment. Hyperion Int. J. Econophys. New Econ. 2014, 7, 305–326.
- Risco, S.; Moltó, G.; Naranjo, D.M.; Blanquer, I. Serverless Workflows for Containerised Applications in the Cloud Continuum. J. Grid Comput. 2021, 19, 30.
- Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and privacy in IoT-cloud-based e-health systems—A comprehensive review. Symmetry 2020, 12, 1191.
- Helo, P.; Hao, Y.; Toshev, R.; Boldosova, V. Cloud manufacturing ecosystem analysis and design. Robot. Comput.-Integr. Manuf. 2021, 67, 102050.
- Saraswat, M.; Tripathi, R. Cloud Computing: Analysis of Top 5 CSPs in SaaS, PaaS and IaaS Platforms. In Proceedings of the 2020 9th International Conference System Modeling and Advancement in Research Trends (SMART), Moradabad, India, 4–5 December 2020; pp. 300–305.
- Hassan, T.; Khan, W.A.; Ahmad, F.; Rizwan, M.; Rehman, R. Edge Caching Framework in Fog Based Radio Access Networks Through AI in Quantum Regime. In Proceedings of the International Conference on Intelligent Technologies and Applications, Bahawalpur, Pakistan, 6–8 November 2019; pp. 711–722.
- Bokhari, M.U.; Makki, Q.; Tamandani, Y.K. A survey on cloud computing. In Big Data Analytics; Springer: Berlin/Heidelberg, Germany, 2018; pp. 149–164.
- Shabbir, M.; Ahmad, F.; Shabbir, A.; Alanazi, S.A. Cognitively managed multi-level authentication for security using Fuzzy Logic based Quantum Key Distribution. J. King. Saud. Univ.—Comput. Inf. Sci. 2022, 34, 1468–1485.
- Khan, W.A.; Ahmad, F.; Alanazi, S.A.; Hasan, T.; Naseem, S.; Nisar, K.S. Trust identification through cognitive correlates with emphasizing attention in cloud robotics. Egypt. Inform. J. 2022, 23, 259–269.
- Zhang, C.; Li, Z.; Li, T.; Han, Y.; Wei, C.; Cheng, Y.; Peng, Y. P-CSREC: A new approach for personalized cloud service recommendation. IEEE Access 2018, 6, 35946–35956.
- Rizwan, M. Cloud Computing Serving as a Solution to the IoT Generated Data. Bahria Univ. J. Inf. Commun. Technol. 2018, 11, 1–6.
- Carney, W.T. A Case Study of the United States Air Force Adoption of Cloud Computing. Ph.D. Thesis, Robert Morris University, Moon Twp, PA, USA, 2019.
- Alanazi, S.A.; Alruwaili, M.; Ahmad, F.; Alaerjan, A.; Alshammari, N. Estimation of Organizational Competitiveness by a Hybrid of One-Dimensional Convolutional Neural Networks and Self-Organizing Maps Using Physiological Signals for Emotional Analysis of Employees. Sensors 2021, 21, 3760.
- Mehmood, M.; Alshammari, N.; Alanazi, S.A.; Ahmad, F. Systematic Framework to Predict Early-Stage Liver Carcinoma Using Hybrid of Feature Selection Techniques and Regression Techniques. Complexity 2022, 2022, 7816200.
- Shahzadi, S.; Ahmad, F.; Basharat, A.; Alruwaili, M.; Alanazi, S.; Humayun, M.; Rizwan, M.; Naseem, S. Machine Learning Empowered Security Management and Quality of Service Provision in SDN-NFV Environment. Comput. Mater. Contin. 2021, 66, 2723–2749.
- Ahmad, F.; Almuayqil, S.N.; Mamoona, H.; Shahid, N.; Wasim Ahmad, K.; Kashaf, J. Prediction of COVID-19 cases using machine learning for effective public health management. Comput. Mater. Contin. 2021, 66, 2265–2282.
- Tsiakmaki, M.; Kostopoulos, G.; Kotsiantis, S.; Ragos, O. Implementing AutoML in educational data mining for prediction tasks. Appl. Sci. 2020, 10, 90.
- Tavara, S. Parallel computing of support vector machines: A survey. ACM Comput. Surv. 2019, 51, 123.
- Lei, B.; Ren, Y.; Wang, N.; Huo, L.; Song, G. Design of a new low-cost unmanned aerial vehicle and vision-based concrete crack inspection method. Struct. Health Monit. 2020, 19, 1871–1883.
- Rajesh, K.N.; Dhuli, R. Classification of ECG heartbeats using nonlinear decomposition methods and support vector machine. Comput. Biol. Med. 2017, 87, 271–284.
- Kayes, A.; Kalaria, R.; Sarker, I.H.; Islam, M.; Watters, P.A.; Ng, A.; Hammoudeh, M.; Badsha, S.; Kumara, I. A survey of context-aware access control mechanisms for cloud and fog networks: Taxonomy and open research issues. Sensors 2020, 20, 2464.
- Jiang, C.; Fan, T.; Gao, H.; Shi, W.; Liu, L.; Cerin, C.; Wan, J. Energy aware edge computing: A survey. Comput. Commun. 2020, 151, 556–580.
- Al-Sayed, M.M.; Hassan, H.A.; Omara, F.A. Towards evaluation of cloud ontologies. J. Parallel Distrib. Comput. 2019, 126, 82–106.
- Talebian, H.; Gani, A.; Sookhak, M.; Abdelatif, A.A.; Yousafzai, A.; Vasilakos, A.V.; Yu, F.R. Optimizing virtual machine placement in IaaS data centers: Taxonomy, review and open issues. Clust. Comput. 2020, 23, 837–878.
- Liu, C.; Su, Z.; Xu, X.; Lu, Y. Service-oriented industrial internet of things gateway for cloud manufacturing. Robot. Comput. -Integr. Manuf. 2022, 73, 102217.
- Wang, G.; He, X.; Ishuga, C.I. HAR-SI: A novel hybrid article recommendation approach integrating with social information in scientific social network. Knowl. Based Syst. 2018, 148, 85–99.
- Zhang, W.E.; Sheng, Q.Z. Managing Data from Knowledge Bases: Querying and Extraction; Springer: Berlin/Heidelberg, Germany, 2018.
- Anisha, C.; Saranya, K. An Intense Study on Intelligent Service Provisioning for Multi-Cloud Based on Machine Learning Techniques. In Operationalizing Multi-Cloud Environments; Springer: Berlin/Heidelberg, Germany, 2022; pp. 177–200.
- Sahingoz, O.K.; Buber, E.; Demir, O.; Diri, B. Machine learning based phishing detection from URLs. Expert Syst. Appl. 2019, 117, 345–357.
- Mohammed, F.; Ali, A.M.; Al-Ghamdi, A.S.A.-M.; Alsolami, F.; Shamsuddin, S.M.; Eassa, F.E. Cloud computing services: Taxonomy of discovery approaches and extraction solutions. Symmetry 2020, 12, 1354.
- Shabbir, A.; Shabbir, M.; Rizwan, M.; Ahmad, F. Ensuring the Confidentiality of Nuclear Information at Cloud Using Modular Encryption Standard. Secur. Commun. Netw. 2019, 2019, 2509898.
- Hosseinzadeh, M.; Hama, H.K.; Ghafour, M.Y.; Masdari, M.; Ahmed, O.H.; Khezri, H. Service selection using multi-criteria decision making: A comprehensive overview. J. Netw. Syst. Manag. 2020, 28, 1639–1693.
- Ouadah, A.; Hadjali, A.; Nader, F.; Benouaret, K. SEFAP: An efficient approach for ranking skyline web services. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 709–725.
- Deepa, N.; Prabadevi, B.; Srivastava, G. Integrated Ranking Algorithm for Efficient Decision Making. Int. J. Inf. Technol. Decis. Mak. 2021, 20, 597–618.
- Obayiuwana, E.; Falowo, O.E. Network selection in heterogeneous wireless networks using multi-criteria decision-making algorithms: A review. Wirel. Netw. 2017, 23, 2617–2649.
- Gireesha, O.; Somu, N.; Krithivasan, K.; VS, S.S. IIVIFS-WASPAS: An integrated Multi-Criteria Decision-Making perspective for cloud service provider selection. Future Gener. Comput. Syst. 2020, 103, 91–110.
- Mehmood, M.; Alshammari, N.; Alanazi, S.A.; Basharat, A.; Ahmad, F.; Sajjad, M.; Junaid, K. Improved Colorization and Classification of Intracranial Tumor Expanse in MRI Images via Hybrid Scheme of Pix2Pix-cGANs and NASNet-Large. J. King. Saud. Univ.-Comput. Inf. Sci. 2022; in press.
- Wang, J.; Jing, X.; Yan, Z.; Fu, Y.; Pedrycz, W.; Yang, L.T. A survey on trust evaluation based on machine learning. ACM Comput. Surv. 2020, 53, 107.
- Chattu, V.K. A review of artificial intelligence, Big Data, and blockchain technology applications in medicine and global health. Big Data Cogn. Comput. 2021, 5, 41.
- Mehmood, M.; Ayub, E.; Ahmad, F.; Alruwaili, M.; Alrowaili, Z.A.; Alanazi, S.; Humayun, M.; Rizwan, M.; Naseem, S.; Alyas, T. Machine learning enabled early detection of breast cancer by structural analysis of mammograms. Comput. Mater. Contin. 2021, 67, 641–657.
- Rahman, A.; Saleem, N.; Shabbir, A.; Shabbir, M.; Rizwan, M.; Naseem, S.; Ahmad, F. ANFIS based hybrid approach identifying correlation between decision making and online social networks. EAI Endorsed Trans. Scal. Inf. Syst. 2021, 8, e4.
- Yanes, N.; Bououd, I.; Alanazi, S.A.; Ahmad, F. Fuzzy Logic Based Prospects Identification System for Foreign Language Learning Through Serious Games. IEEE Access 2021, 9, 63173–63187.
- Shahzadi, S.; Khaliq, B.; Rizwan, M.; Ahmad, F. Security of cloud computing using adaptive neural Fuzzy inference system. Secur. Commun. Netw. 2020, 2020, 5352108.
More
