Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Yeray Mezquita and Version 2 by Rita Xu.
Blockchain technology is used as a distributed ledger to store and secure data and perform transactions between entities in smart grids. The use of a permissioned blockchain network has multiple benefits as it reduces transaction costs and enables micro-transactions. Moreover, an improvement in security is obtained, eliminating the single point of failure in the control and management of the platform along with creating the possibility to trace back the actions of the participants and a mechanism of identification.
- blockchain
- energy market
- multi-agent system
1. Introduction
The current traditional power grid is designed to transport energy over long distances. This characteristic of the traditional system implies that certain limitations exist, such as the maximum voltage capacity supported by the distribution lines [1]. When this capacity is exceeded, the heat generated by a line can cause it to sag or break, resulting in power supply instabilities such as phase and voltage fluctuations. Because the capacity of a line depends on its length and the transmission voltage, one solution is to create shorter lines and distribute the functionalities of the current power grid in smaller smart networks. These networks are called smart micro-grids, which are a type of discrete energy system that includes appropriated energy sources as well as power loads that provide power to residential, commercial, industrial, and governmental consumers. The main purpose of smart micro-grids is to provide affordable energy to areas independently of the main power supply network while optimizing the transmission of the energy.
In the current context of energy generation, thanks to renewable sources such as solar or wind, and together with the emergence of a new type of actor that consumes and produces energy within the system—the so-called prosumers—micro-grids have the potential to replace the traditional energy transmission system in the near future [2]. However, the rise of smart micro-grids comes with some challenges that must be faced. These challenges range from the vulnerability of platforms to DDOS attacks, to the emergence of intermediaries that do not contribute to energy distribution but end up making it more expensive [3].
In the past, some authors have proposed strategies for energy management on micro-grid platforms. For example, in [4], the excess or shortage of energy could be compensated by exchanging it with the utility grid or other external sources. However, that papentryr did not allow for direct energy exchange between individuals, nor did it allow for the automation and distribution of the platform. Without the use of blockchain technology, democratized energy markets could not be created. A blockchain network acts as a reliable distributed ledger that is governed by the platform and where information of value is stored. The network can be utilized to distribute the control and governance of the smart grid, along with the communication that is carried out within it, thus avoiding the single point of failure and eliminating those intermediaries that do not give any value to the platform. Moreover, blockchain technology (BT) provides a mechanism for protecting the actors against identity theft by signing direct communications between peers [5].
2. Conceptual Foundations of Micro-Grid Platforms and Blockchain Technology
Traditional power grids deliver energy from a few central generators to a large number of consumers. This creates a closed market in which energy prices are dictated in a monopolistic way. Sometimes, to avoid abusive pricing by companies towards consumers, states need to implement regulatory measures, with the European Union [6][7][6,7] being an example in this case. In the face of this monopolistic behavior, the literature has proposed the distribution of the traditional main grid into smaller micro-grids [2]. These micro-grids are comprised of a set of loads and generators. The set of generators can be composed of individual houses with solar panels on the roof. The entry of more entities into the energy market reduces the risk of oligopolies and avoids the intervention of states by imposing the use of regularization measures. This way, the energy market is converted into a more democratic market in which the offer and demand of energy will be the only factors that can regulate the energy price. Micro-grid platforms make use of a great number of Internet of Things (IoT) devices that exchange crucial information between them. The continuous communication between the devices allows for the distribution of the management and control of any IoT platform. This helps with the optimization of the workflow of the system, but not without some drawbacks [8].-
Heavy reliance on exchanged messages. Since each part of the system is controlled by an independent entity, the other entities have to trust the messages received to understand the system’s global state. If a malicious entity could somehow modify the content of those messages, the proper functioning of the entire platform would be compromised.
-
Reliance on the truthfulness of the transmitted data. Entities of the platform have to rely on the fact that the data transmitted have not been tampered with by the sender entity to make an unfair profit. In addition, it is a possibility that databases will be attacked in order to steal, modify, or delete sensitive information about the entities that are taking part in the system’s workflow.
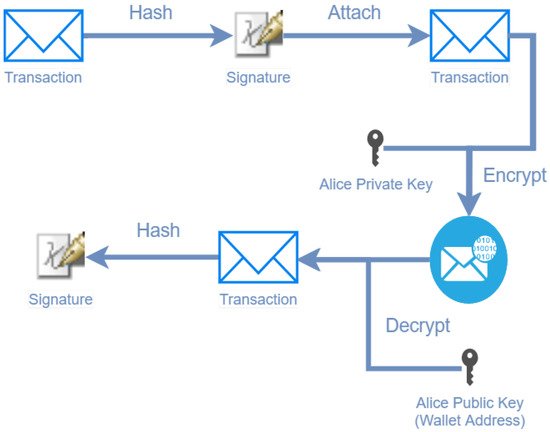
Figure 1. Example of the signature mechanism in a transaction.
2.1. Blockchain Consensus Algorithms
A consensus algorithm describes the mechanism that allows all agents in the system to coordinate in a distributed environment. It constitutes the only source of truth. Thanks to the consensus algorithm employed by the network of nodes, it is possible to keep the information stored and replicated in a consistent state. Among the functions of any consensus algorithm is ensuring that there is only one blockchain in the system, which can be an issue when a part of the network accepts a blockchain while the remaining nodes accept a different one (Fork). The consensus algorithm should enable the convergence of the chains into one as soon as possible. Moreover, it should offer resilience against attempts by malicious actors to take over the network and guarantee that there will not be any consensus failure when nodes try to add new blocks of data to the blockchain. Keeping the data stored in a blockchain makes it more difficult for attackers to take down the services of a system, and the attacker is forced to take down the majority of them to successfully hack the data [8]. There is a great variety of consensus algorithms, including the Proof of Work (PoW), Proof of Stake (PoS), and Practical Byzantine Fault Tolerance (PBFT) (see Table 1), or any of their variants that are the most widespread and have proven their effectiveness in practice [13].Table 1. Comparison between consensus algorithms and their common usage.
| Algorithm | Scalability | Consistency | Decentralization | Usage |
|---|---|---|---|---|
| PoW | No | Yes | Yes | Public blockchains |
| PoS | Yes | No | Yes | Public and permissioned blockchains |
| PBFT | Yes | Yes | No | Permissioned blockchains |
