Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 2 by Beatrix Zheng and Version 1 by Araceli Queiruga-Dios.
In the past few years, “smart” objects and products have given rise to significant progress in industry production and its security. Advances in digitization that have occurred in the industry, combined with internet technologies and future-oriented technologies in the field of so-called “smart” objects (machines and products), have led to a new and fundamental paradigm shift in industrial production and in their security.
- cryptography
- security model
- malware spreading
- lightweight cryptography
- medical wearables
1. Introduction
The purpose of using cyber-structures (including detection, computing, and communication hardware/software) is the monitoring and control of our physical world. Ciber-physical systems are the consequence of the integration of embedded systems, such are sensors and control systems [1]. In general, health care devices and wearable health-monitoring systems (WHMS), in particular, are emerging as one of the critical areas in Industry 4.0, specifically portable or wearable technological devices, which are the most attractive applications in the IoT area [2,3][2][3]. Medical devices for human use are articles with medical purposes such as diagnosis, investigation, monitoring, prevention, or treatment of a disease, or control of physiological or pathological processes. These devices are regulated by the Medical Devices Regulation [4].
Many wearable systems were developed for physiological monitoring. Some of these devices are a wristband to monitor and alert patients at high cardiac-respiratory risks [5]. A different wearable (BodyGuard) was developed to monitor several parameters in space and on the ground, which had the ability to continuously record the reading of electrocardiogram (ECG), heart rate, room or body temperature, and other variables [6]. The Georgia Tech Wearable MotherboardTM characterized by a wearable motherboard allowed to measure numerous vital parameters and could be incorporated into clothing, and soldiers could wear it easily and comfortably [7,8][7][8].
The so-called MagIC (Maglietta Interattiva Computerizzata) is a fabric-based wearable system that took measures of cardiorespiratory signals in individuals with heart problems. This system was used on subjects in daily situations and collected results showed good quality data during most of the time. This allowed arrhythmia events identification in individuals using this wearable [9].
Since then, several health monitoring systems have been developed for patients homecare [10,11][10][11]. Recent developments have improved medical devices with an emphasis on characteristics of biosensors and materials such are stretchability (e.g., artificial limbs [12]), ultrathin and conformality (e.g., skin and implantable electronic products [13]), and biocompatibility and biodegradability (e.g., silicon sensors for the brain [14]).
There are several possible classifications of health monitoring systems. In this paper, the following three categories will be considered [15]:
-
Remote health monitoring systems (RHMS) are devices situated far from the system receiving the collected data.
-
Mobile health monitoring systems (MHMS) are mobile devices such as mobile phones, computers, pocket laptops, etc., that monitor health parameters.
-
Portable health monitoring systems or wearables include WHMS, RHMS and/or MHMS. These devices can be carried by patients in such a way that the sensors are integrated into clothing or accessory. These are called wearables. Thus, these give rise to smart fabrics, smart-textiles, or e-textiles.
Mainly motivated by rising health care expenditures and because of the recent technological advances in microsensors, health monitoring systems can reduce hospitalization time, and the excessive workloads on healthcare personnel, consultation time, waiting lists, etc. An example of this case is people with diabetes, who are prone to some form of nerve damage or injury throughout their lives, especially if they suffer diabetes over a long time. The diabetic disease is considered an important health problem, due to its frequency and its enormous economic and social impact [16]. Diabetics affects the quality of life of people suffering this disease, because it causes ulcers on patients’ feet. Moreover, peripheral neuropathy and vascular insufficiency are the most common chronic complications of this disease. These healthy problems in diabetic patients made some research teams work in wearables to measure different variables in these patients’ feet, such as the temperature [17,18][17][18].
A wearable medical device to measure the temperature of the foot consists, fundamentally, of a series of sensors that continuously (in a given period of time) measure the temperature at different regions of interest (ROI) of the foot that have been previously selected. A sock with sensors located in specific ROI is a wearable capable of sending data to an external device and create an alarm in case of ulceration development. Furthermore, it is made up of conductive tissues that carry these measurements to a base station or sink. A health surveillance wireless sensor network designed to deliver personalized healthcare is also called a body area network (BAN) [19].
Figure 1 shows a representation of the connections of a wearable that takes measures of foot temperature, the architecture of a conventional wearable network and the main elements: the wearable itself, a base station/gateway, cloud servers, users, and their control tools. The wearable includes elements of the network that are responsible of creation, detection and (pre-)checking of basic information. On the other hand, routing protocols in a WHMS are established in four tiers: the first one is within the device, where sensors collect the data and send them to the controller through a thermal-aware routing protocol, such are ATAR [20] or WETRP [21]. Then, the controller processes the received information and send it to the gateway. Finally, collected data are transmitted to the user mobile phone by Bluetooth Low Energy (BLE), Wi-Fi or Radiofrequency (RF), and from here to his/her computer or the corresponding health-center through Internet [22,23][22][23].
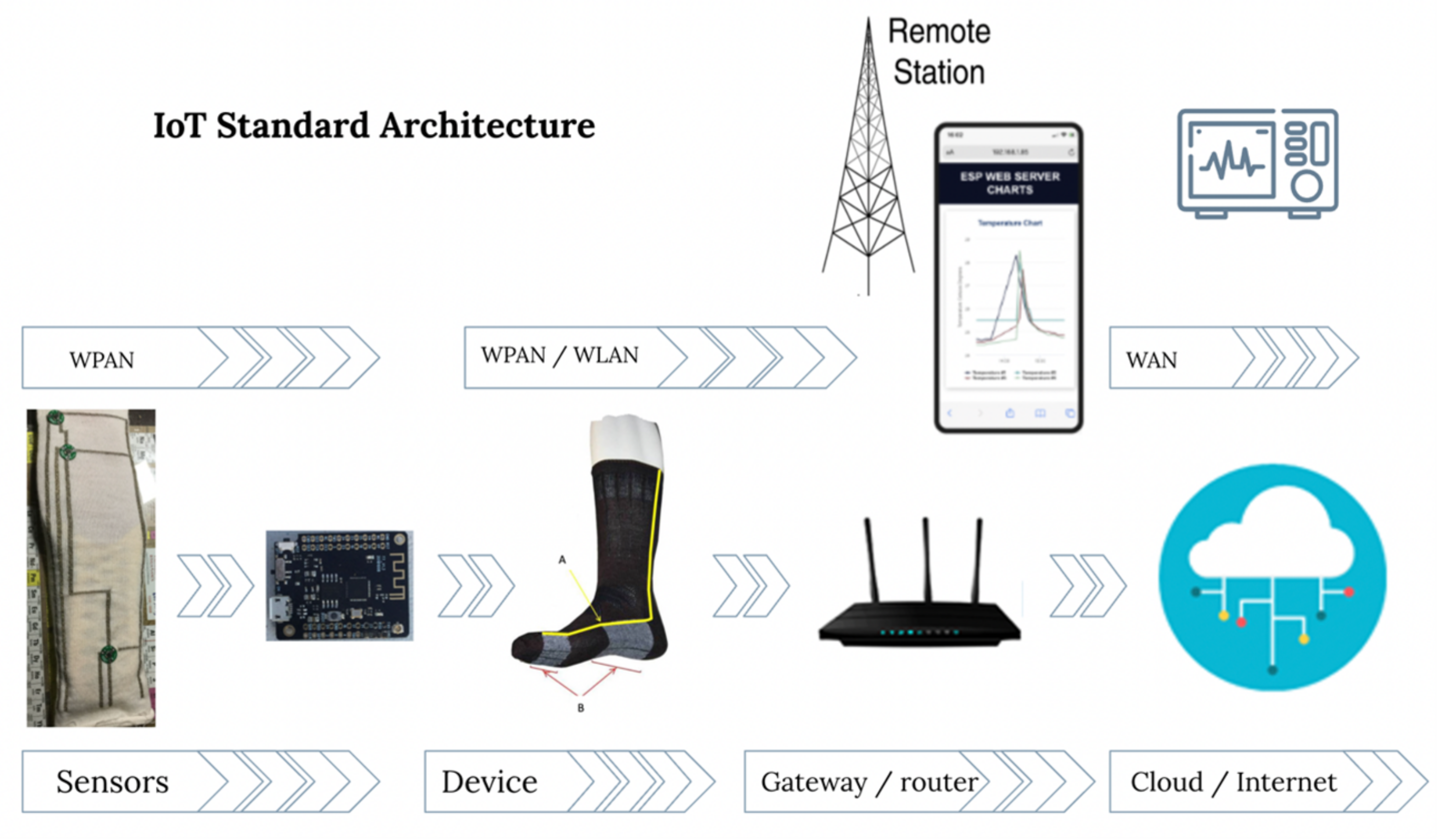
Figure 1.
Overview of the architecture of an IoT-based health device to measure the foot’s temperature.
The security needs for IoT-based healthcare solutions are similar to those considered in common communication scenarios: integrity (patient information cannot be altered or changed by unauthorized personnel), availability (data must be available to authorized persons upon request), confidentiality (sensitive information cannot be used by unauthorized individuals, entities or processes) and non-repudiation (individuals cannot deny an action they have carried out) [24,25][24][25].
The main limitation of medical applications is their constrained resources. This drawback makes several cryptographic protocols not appropriate for these devices with small size and memory, that require low computation power, short time battery, short memory, and low bandwidth. Lightweight cryptography (LWC) reduces computation time and complexity and assure security [26,27,28][26][27][28].
2. Current Insights
With the massive use of wearable health–monitoring systems, security challenges are increasing rapidly. Cybercriminals use malware as their main weapon to carry out security attacks, causing significant damage and loss to IoT users. The main objectives of cybercrimes against WHMS are firmware vulnerabilities, communication protocols and applications and sensors to get users’ sensitive information or to damage devices.
The analysis of the vulnerabilities of a device has the purpose of mitigating or reducing the risks to which the system is exposed, with the purpose to protect the information that is stored in the servers or transmitted through different routing protocols to the network. For this reason, cybersecurity studies for different environments are becoming more and more frequent, as is the case of medical devices, made up of microsensors whose purpose is to monitor different physical phenomenon. In this restudyearch, the physical phenomena is the temperature that is measured in diabetic foot.
In this restudyearch, the spread of malware in a medical network is simulated using an agent-based model to improve the cybersecurity mechanisms that can be applied to this type of network. One of the advantages of ABM is that it considers individual characteristics, which is particularly useful in the case of wearable health-monitoring systems because a failure in a component could cause serious health problems. This is not the case of global models, that include general characteristics of the network. Malware spreading depends on the environment; the spread is different in the military, industrial or medical sectors, Internet, Wi-Fi, BLE, or thermal-aware routing protocols, etc. Some studies suggest implementing security tools such as Honeypots for wireless sensor networks, which allow real-time data collection of a malicious attack in a controlled environment.
Three different environments were considered for this simulation. In the first one, 10 individuals wear a device made of six sensors, three per foot (considering a medical device to take foot temperature measures). In this case, the simulation showed that the malware was spreading slowly. After 168 h, there were still 45 sensors (corresponding to 7 persons) that were not infected. In the second simulation the number of devices was considerably increased. It considered 15 individuals with 34 sensors each one, i.e., a total amount of 510 sensors distributed in the corresponding regions of interest. The malware spreads rapidly. In 21.6 h, the number of susceptible are equal to the number of exposed sensors, so, these sensors will not spread the malware. Moreover, from the 11th hour, infected and exposed increase together until the 18th, where infected decrease and exposed and recovered increase. As dead sensors do not increase, devices will recovered from the malware attack. The recovery begins when infected decrease under recovered and exposed. The third simulation considered a secure network. In this case, the risk of malware attack and devices infected is medium and low, respectively. An equilibrium is reached in this simulation after 160 h. Moreover, the malware spreading is slow, with a maximum of infected nodes at 76 h.
Most medical devices do not have sufficient resources to provide complex cryptography. Limitations in their computational capacity, energy consumption, capacity of transmission and reception of information, etc., make traditional cryptographic algorithms not suitable for them. A cryptographic protocol for constrained resources is considered an acceptable solution to secure health devices. The primary choice for the NIST protocol that could be used with all security considerations is the Ascon-80pq from the Ascon cipher suite. No weakness was found for this protocol of excellent implementation characteristics. Ascon is highly appropriate for wearable health-monitoring lightweight systems where several communications protocols are involved, it can be efficiently used for these systems where side-channel resistance is essential. Moreover, Ascon is a simple algorithm, as it only uses bitwise Boolean functions.
The security provided by all Ascon family members protects the plaintext confidentiality and the plaintext, the associated data and the public message number integrity. The use of the same underlying permutation for authenticated encryption and hashing reduces the area requirements for hardware implementations and restrict the code base and thus, the workload is reduced.
References
- Sacală, I.Ş.; Moisescu, M.A. The Development of Enterprise Systems based on Cyber-Physical Systems Principles. Rom. Stat. Rev. 2014, 4, 29–39.
- Robson, K.; Pitt, L.; Kietzmann, J.; Halvorson, W.; Wallstrom, A. Wearable Technology: Trends and Opportunities for Organizations. In Celebrating America’s Pastimes: Baseball, Hot Dogs, Apple Pie and Marketing? Springer: Berlin/Heidelberg, Germany, 2016; p. 801.
- Islam, S.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.S. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708.
- European Union. Regulation (EU) 2017/745 of the European Parliament and of the Council of 5 April 2017 on medical devices, amending Directive 2001/83/EC, Regulation (EC) No 178/2002 and Regulation (EC) No 1223/2009 and repealing Council Directives 90/385/EEC and 93/42/EEC. Off. J. Eur. Union 2017, 117, 1–175.
- Anliker, U.; Ward, J.A.; Lukowicz, P.; Troster, G.; Dolveck, F.; Baer, M.; Keita, F.; Schenker, E.B.; Catarsi, F.; Coluccini, L.; et al. AMON: A wearable multiparameter medical monitoring and alert system. IEEE Trans. Inf. Technol. Biomed. 2004, 8, 415–427.
- Mundt, C.W.; Montgomery, K.N.; Udoh, U.E.; Barker, V.N.; Thonier, G.C.; Tellier, A.M.; Ricks, R.D.; Darling, R.B.; Cagle, Y.D.; Cabrol, N.A.; et al. A multiparameter wearable physiologic monitoring system for space and terrestrial applications. IEEE Trans. Inf. Technol. Biomed. 2005, 9, 382–391.
- Gopalsamy, C.; Park, S.; Rajamanickam, R.; Jayaraman, S. The wearable motherboardTM: The first generation of adaptive and responsive textile structures (arts) for medical applications. Virtual Real. 1999, 4, 152–168.
- Park, S.; Jayaraman, S. Enhancing the quality of life through wearable technology. IEEE Eng. Med. Biol. Mag. 2003, 22, 41–48.
- Di Rienzo, M.; Rizzo, F.; Parati, G.; Brambilla, G.; Ferratini, M.; Castiglioni, P. MagIC system: A new textile-based wearable device for biological signal monitoring. Applicability in daily life and clinical setting. In Proceedings of the 2005 IEEE Engineering in Medicine and Biology 27th Annual Conference, Shanghai, China, 17–18 January 2005; pp. 7167–7169.
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of wireless sensor networks: An up-to-date survey. Appl. Syst. Innov. 2020, 3, 14.
- Qiao, L.; Benzigar, M.R.; Subramony, J.A.; Lovell, N.H.; Liu, G. Advances in sweat wearables: Sample extraction, real-time biosensing, and flexible platforms. ACS Appl. Mater. Interfaces 2020, 12, 34337–34361.
- Wang, B.; Facchetti, A. Mechanically flexible conductors for stretchable and wearable e-skin and e-textile devices. Adv. Mater. 2019, 31, 1901408.
- Lou, Z.; Wang, L.; Jiang, K.; Wei, Z.; Shen, G. Reviews of wearable healthcare systems: Materials, devices and system integration. Mater. Sci. Eng. R Rep. 2020, 140, 100523.
- Kang, S.K.; Murphy, R.K.; Hwang, S.W.; Lee, S.M.; Harburg, D.V.; Krueger, N.A.; Shin, J.; Gamble, P.; Cheng, H.; Yu, S.; et al. Bioresorbable silicon electronic sensors for the brain. Nature 2016, 530, 71–76.
- Baig, M.M.; Gholamhosseini, H. Smart health monitoring systems: An overview of design and modeling. J. Med. Syst. 2013, 37, 1–14.
- DeFronzo, R.A.; Ferrannini, E.; Zimmet, P.; Alberti, G. International Textbook of Diabetes Mellitus; John Wiley & Sons: Hoboken, NJ, USA, 2015.
- Macdonald, A.; Petrova, N.; Ainarkar, S.; Allen, J.; Plassmann, P.; Whittam, A.; Bevans, J.; Ring, F.; Kluwe, B.; Simpson, R.; et al. Thermal symmetry of healthy feet: A precursor to a thermal study of diabetic feet prior to skin breakdown. Physiol. Meas. 2016, 38, 33.
- Torreblanca González, J.; Gómez-Martín, B.; Hernández Encinas, A.; Martín-Vaquero, J.; Queiruga-Dios, A.; Martínez-Nova, A. The Use of Infrared Thermography to Develop and Assess a Wearable Sock and Monitor Foot Temperature in Diabetic Subjects. Sensors 2021, 21, 1821.
- Venkatasubramanian, K.K.; Banerjee, A.; Gupta, S.K.S. PSKA: Usable and secure key agreement scheme for body area networks. IEEE Trans. Inf. Technol. Biomed. 2010, 14, 60–68.
- Jamil, F.; Iqbal, M.A.; Amin, R.; Kim, D. Adaptive thermal-aware routing protocol for wireless body area network. Electronics 2019, 8, 47.
- Bhangwar, A.R.; Ahmed, A.; Khan, U.A.; Saba, T.; Almustafa, K.; Haseeb, K.; Islam, N. WETRP: Weight based energy & temperature aware routing protocol for wireless body sensor networks. IEEE Access 2019, 7, 87987–87995.
- Bhanumathi, V.; Sangeetha, C. A guide for the selection of routing protocols in WBAN for healthcare applications. Hum.-Centric Comput. Inf. Sci. 2017, 7, 1–19.
- José Bulllón Pérez, J. Smart System to Monitor Temperature in Diabetic Foot. Ph.D. Thesis, Universidad de Salamanca, Salamanca, Spain, 2015.
- Al Ameen, M.; Liu, J.; Kwak, K. Security and Privacy Issues in Wireless Sensor Networks for Healthcare Applications. J. Med. Syst. 2012, 36, 93–101.
- Siponen, M.T.; Oinas-Kukkonen, H. A review of information security issues and respective research contributions. ACM Sigmis Database 2007, 38, 60–80.
- Dhanda, S.S.; Singh, B.; Jindal, P. Lightweight cryptography: A solution to secure IoT. Wirel. Pers. Commun. 2020, 112, 1947–1980.
- Fotovvat, A.; Rahman, G.M.; Vedaei, S.S.; Wahid, K.A. Comparative Performance Analysis of Lightweight Cryptography Algorithms for IoT Sensor Nodes. IEEE Internet Things J. 2020, 8, 8279–8290.
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Park, J.H. Advanced lightweight encryption algorithms for IoT devices: Survey, challenges and solutions. J. Ambient. Intell. Humaniz. Comput. 2017, 1–18.
More
