A UAS traffic management (UTM) system requires that each UAV be able to see and be seen; therefore, the communication channel becomes crucial. In the last five years, state-of-the-art research has focused on three types of communication: ADS-B, ADS-B-like communication, and Remote ID. ADS-B is the legacy system currently used in manned flights and has been mandatory since 2020. Similarly, the ADS-B-like system works similarly to ADS-B but uses different types of wireless communication technology such as 4G, XBee, and APRS (automatic packet reporting system). However, Remote ID is a new standard established, based on Bluetooth/Wi-Fi technology that fulfills the requirement for current UTM operations. The communications in UTM can be categorized into ADS-B, Remote ID, and ADS-B-like systems. The information presented here consist of definition, data format, technology, and research application.
- UTM communication
- ADS-B
- ADS-B-like communication
- Remote ID
1. Definition of ADS-B, Remote ID, and ADS-B-like systems
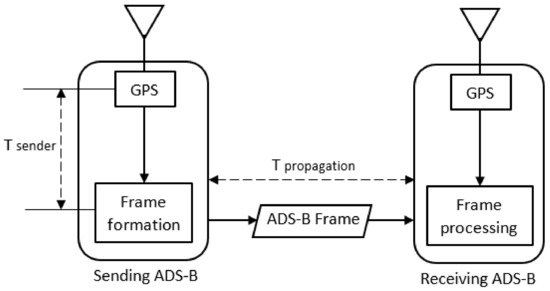
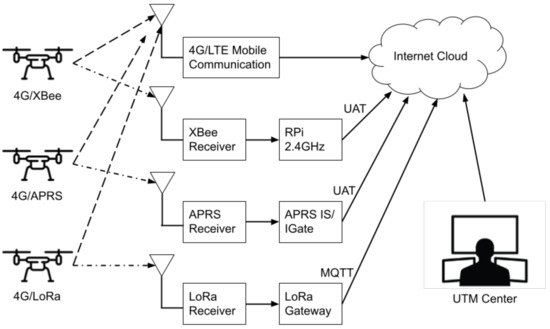
2. Data Format
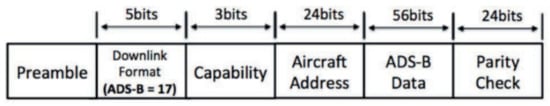
- - UAS owner identification and its contact.
- - Properties of the vehicle including aircraft type, such as fixed-wing, quadcopter, etc.
- - Current flight plan, vehicle heading, speed, and future operations.
- - UTM status of the current flight plan, such as rogue, non-conforming, etc.
3. Technology
ADS-B uses high radio frequency to transmit its message. There are two types of ADS-B broadcasting frequencies, which are a 978 MHz universal access transceiver (UAT) [17] and a 1090 MHz extended squitter (ES). The ADS-B message’s standard mean sending rate is 6.2 messages/second, and the message duration is 120 μs [4]. In comparison, the message duration for the secondary surveillance radar (SSR) messages is 35 μs, and mode S short messages are 64 μs [4]. The ADS-B message has a slightly longer required transmission duration. In manned airplanes, the power required for ADS-B ranges from 75 W to 500 W, with the maximum broadcasting range up to 500 km. While the ADS-B power on UAVs is much lower, it is between 0.01 W and 1 W [4]. Generally, ADS-B modules consist of two functions, which are ADS-B OUT (transmitter) and ADS-B IN (receiver). ADS-B IN facilitates reception and demodulation of nearby ADS-B OUT broadcasts, while ADS-B OUT periodically broadcasts information regarding its states [3]. Hence, the surveillance system consists of these broadcaster and receiver capabilities. An example of an ADS-B module for UAV are the Ping2020 ADS-B transponders produced by uAvionix. It can transmit identity, aircraft position, heading, and speed information extracted from a flight controller. This ADS-B transponder broadcasts data in every second, and its barometric altitude sensor has a reading accuracy of up to 10 cm [18]. Unlike ADS-B, Remote ID can use several communication technologies to transmit its messages, such as LoRaWAN, infra-red-light beacons, dedicated short-range communication (DSRC) radios, and Bluetooth 5 low energy (BLE5). Firstly, LoRaWAN is an affordable, long-range communication of the internet. It has a coverage range of 15 to 30 km [5]. Secondly, an infra-red light beacon is used to provide a vehicle registration and model database (VRMD), named UTM vehicle identification number (UVIN) [14]. The third, DSRC radios, can be used as V2V communication devices in a Remote ID system with a frequency band from 5.850 to 5.925 GHz and a +20 dBm power output. They assign for each UAS a globally unique flight identifier (GUFI) as the Remote ID identity [7]. Last is BLE5, which is a low-power, unlicensed Bluetooth radio frequency. According to the flight test between a small UAS and a manned helicopter using BLE5, the results indicate that the possible performance range is about 1 km [6]. Furthermore, based on the Remote ID standard published by ASTM, there are two types of Remote ID. They are network Remote ID and broadcast Remote ID. Network Remote ID employs a cellular network to transmit its message. At the same time, broadcast Remote ID employs the short-range wireless technology mentioned earlier [15]. The broadcast Remote ID is endorsed by FAA and will be effective by 2023. However, the Network Remote ID is not yet regulated due to some rejections from the public opinion. Like Remote ID, the ADS-B-like system employs several communication technologies to transmit its message. There are two groups of wireless technology used in the ADS-B-like system: cellular-based and non-cellular-based technology. The cellular-based technology includes LTE/4G networks with frequency spectrum at 979 MHz or 1104 MHz [8], and 5th generation (5G) with a frequency spectrum from 24 GHz to 86 GHz [9] [10]. The non-cellular-based technology consists of LoRaWAN [12], XBee [19], APRS [16], and Wi-Fi beacons [11]. LoRaWAN uses a technique of spread spectrum modulation. It is an unlicensed radio spectrum ranging from 920 MHz to 925 MHz, and is used in industrial, scientific, and medical applications [12]. The second is XBee, which uses the Digi Mesh protocol at 900 MHz. It uses a low power of 1W/32dBm and ranges from 9 to 65 miles [12]. The third is APRS, which is commonly used by volunteer rescue groups with a specific frequency of 144.64 MHz (assigned for public use) [16]. The last is Wi-Fi beacons, which use the 2.4 GHz band and 5 GHz band. They could achieve an output of at least two messages/second in the worst scenario using only 17 dBm, which equals about 50 mW of power transmission [11]. Unlike ADS-B and Remote ID, which have fixed standards and are regulated by the authority, the ADS-B-like system is an open system suggested by the research community that leverages the available wireless technologies. When researchers compare Remote ID and ADS-B-like systems, researchers found many similarities in terms of technologies and message protocol. Hence, researchers can say that Remote ID is a type of ADS-B-like formalized by the FAA into one specific means of communication for UAV.4. Research Applications
4.1. ADS-B Research
At the beginning of UTM development, the ADS-B was considered a top candidate for UTM communication. It was supported by a regulation that ADS-B will be mandatory for all airliners by 2020. However, some disadvantages are discovered that make it unfavorable. Researchers found that research on ADS-B for UTM focused on surveillance, detect and avoid, capacity estimation, and security. As the main function of ADS-B in manned flight, ADS-B is used as a surveillance system in UTM. In this function, knowing the trajectory of a UAV is important. One research proposed a trajectory fusion based on an active and passive feedback system. The ADS-B surveillance data from UTM were used as the active and passive feedback. The data were derived from the ground control station. Their simulation obtained accurate flight parameters and a continuous stability of UAV trajectory [20]. Other research used a more advanced method for accurate 4D trajectory prediction: a genetic algorithm. The algorithm used historical ADS-B flight data and the UAV equation of motion. Their simulation could estimate UAV trajectory and the entering time to the protection zone accurate and instantly [21]. Since ADS-B data are heavily dependent on information from the GNSS system, another research proposed a method to construct a UAV trajectory when devoid of a GNSS signal. The algorithm used a measurement of the time elapsed from the UAV connection to several ground-based stations. Then, it used the triangulation (multi-lateration) method. The flight test showed that the algorithm was capable of navigating a UAV through several waypoints of trajectory in the missing GNSS signals [22]. Hence, the trajectory research aims to provide accurate and reliable information for surveillance functions. The research in ADS-B as a surveillance system for UTM also covers mixed traffic between UAVs and manned flight. One of the concerns from the aviation community on the usage of ADS-B in UAVs is the frequency saturation when a high density of UAV flights becomes a reality. Two publications focused on using reduced transmission power of ADS-B to mitigate the saturation condition. First, research conducted a flight test to measure ADS-B performance in UAVs for several transmission power levels [23]. The second research simulated general aviation and UAV flights in a low-level and very low-level airspace of an urban area, using low-power ADS-B as a surveillance system [24]. Both types of research concluded that low-power ADS-B provided data at acceptable ranges and update intervals required for UTM operations. Additionally, the reduced transmission power also produced a sufficient range to alert manned flight. One more research in mixed traffic used ADS-B data to analyze the effects of lack in clock synchronization to the ATM. It provided solutions based on the availability of several trusted sensors in a large, uncoordinated network of UAVs [25]. In this context, the UAV functions as a relay airborne for ADS-B of manned flights. In support of ADS-B as a surveillance function in UTM, several types of research also focused on designing required components, such as an antenna, ADS-B module, UAV, and airspace structure. One research designed a UAV antenna dedicated to detecting manned flights by the demodulation of ADS-B. The antenna consisted of an array of planar inverted-F antennas, a reflector plane, and a quadrature feed network. The test shows that it can detect aircrafts up to 437 km [26]. Besides antennas, another research designed and prototyped a cards system that is lightweight and small enough to be placed on a UAV, and could create and broadcast a ADS-B message compliant with RTCA DO-282B [27]. On top of the antenna and ADS-B module, one example of UAV design dedicated for ADS-B measurement was the UAV-based flight inspection system (UFIS). This prototype UAV contained antennas, a positioning module, an airborne processing unit, a flight inspection sensor, a control unit, and an air-ground data link unit [28]. Besides vehicle components, an airspace design is also an important part of UAV surveillance using ADS-B. The SafeDrone European project designed flight procedures and an airspace related with no-fly zones to ensure safe separation of UAVs and manned flights [29]. Thus, the integration and implementation of all those designed components need to be integrated into the real UTM operation. The second category in ADS-B research is detect and avoid. It is related to safety as the top priority in UTM operation. Researchers found the largest amount of research focused on this area. For clarity, researchers categorized it into trajectory estimation, data science processing, mixed traffic detection, and system design. For the trajectory estimation research, researchers divide it into two groups: algorithm and implementation. Researchers found four publications that explained detect and avoid algorithms in UAVs using the ADS-B sensor. The first algorithm represented a method of defining a potential collision of two or more UAVs in airspace. UAV trajectories were estimated by two or three waypoints of trajectory obtained from the ADS-B system. It calculated a point of the UAVs’ collision by defining the crossing points of trajectories from two cut-off values in the critical speed range [30]. Similarly, the second publication proposed a distance-limiting scheme to verify the flight distance and trajectory in the ADS-B transmitted messages from nearby UAVs [31]. Although the third algorithm used ADS-B data from nearby UAVs, it used a fuzzy logic algorithm to make a decision to avoid the collision [32]. The fourth algorithm used grey wolf optimization (GWO) to avoid moving obstacles. The position of obstacles is provided via the ADS-B or ground-based radar. Unlike the other algorithms, it assumed that the obstacles’ future trajectories were unknown. The solution was calculated based on Bayesian formalism with a distance-weighting function [33]. The last algorithm in the detect and avoid category used information sharing protocol to predict the collision event. The predictive model controller is represented by a pair of UAVs coupled with the presence of an imminent collision [34]. The algorithms mentioned in the previous paragraph found that the first algorithm was successfully implemented in a flight simulation using up to 50 UAVs with yaw and speed maneuvers [35]. However, the second publication on detect and avoid implementation was not related to the mentioned algorithms. It used both software-in-the-loop and hardware-in-the-loop simulations. The UAVs used Pixhawk autopilots for autonomous flight and Intel NUC processor hardware for the collision avoidance algorithm implementation [19]. Hence, the trajectory algorithm and its implementation became critical for the successfulness of the detect and avoid function. Besides detect and avoid techniques based on trajectory estimation, data science technology is a newly emerging method. One publication used a data science technique for the detect and avoid categories. It used data from an ADSB aggregator on six days and within 5 miles of an airport. The data showed that some zero-foot grids were well beyond the traffic pattern with no manned aircraft below 500 ft AGL for at least a mile [36]. Another publication combined ADS-B data from manned flights with UAV traffic data measured by DJI AeroScope near Daytona Beach International Airport (KDAB). The collected data were examined to define the population of UAS flights, to measure the maximum flight altitudes, and to determine the operating locations [37]. Although these data science techniques do not directly relate to detecting and avoiding UAV traffic in real-time, the data-driven analysis could be used for future planning of drone safety operations. The detect and avoid category also considers mixed traffic between UAVs and manned flights. The most researched area in this category is the separation assessment. The NASA flight demonstration for UTM technical capability level (TCL) 3 covered a sense and avoid scenario in which it addressed the hazard posed by transponder-equipped, manned flights. The scenario demonstrated the safe lateral separation in conflicts between a UAS using ADS-B IN and a manned flight using ADS-B OUT [38]. Similarly, another publication assessed separation between UAVs and manned flights equipped with ADS-B using commercial sensor equipment, called DJI AeroScope [39]. Unlike the previous two publications using sensors to assess the separation, one publication sought to determine the mean visibility separation of UASs in visual meteorological conditions (VMC). It aimed for an alert to a pilot flying a general aviation (GA) aircraft [40]. Besides the separation assessment conducted by three previous publications, one more publication in this category proposed a ground-based sense and avoid (GBSAA) system to enable mixed traffic of low-altitude UAVs and ADS-B-enabled, manned flights. It conducted analytical and simulation studies to investigate a possible collision due to the different network parameters. It found that the GBSAA could support more UAVs than an ADS-B-only system [41]. For supporting the detect and avoid functionality, some researchers focused on designing or implementing the required components or systems. An antenna is one of the important components. One research designed a coaxial-fed compact blade antenna with a dual frequency. It combined the ADS-B and 5G cellular network. It showed that an antenna with a low profile and a simple structure was suitable for future UAV-assisted 5G networks. Additionally, it was well suited to the upcoming ADS-B-based detection avoidance functions [42]. The second component researched was the ADS-B module for UAVs called Ping2020 from uAvionix. The publication presented the collision avoidance algorithms’ implementation in a fixed-wing UAV. The simulation and flight test results showed that ADS-B’s integration into UAVs was potentially effective for the detection and avoidance function [18]. Another system to support the detect and avoid function is a detection system consisting of multi-sensors. There are three publications that described this system. The Drone Net is one of them. The system was a combined detection system using ADS-B, RADAR/LIDAR, and an electro-optical/infra-red camera [43]. Another research proposed a combination of a common video, audio sensors, a thermal infra-red camera, and ADS-B for a potential solution to a drone detection system [44]. These two detection systems are fixed on the ground. The other detection system that can fit onboard UAVs is a lightweight obstacle detection system. It integrates a thermal infra-red (TIR) camera and ADS-B receiver [1]. All those detection systems combined ADS-B with other sensors for improvement of its robustness to sensor errors, sample loss, and false detection. The last system designed for the detect and avoid function is the drone itself. One research designed and prototyped a delivery drone equipped with an ADS-B module to improve its safety. The prototype was effective in detecting and avoiding other UAVs during their mission [45]. The third category in ADS-B research is the capacity estimation. It estimates the maximum capacity and tries to minimize the effects of limiting factors. One research demonstrated the bandwidth limitations of a 978 MHz ADS-B frequency. This limitation could be used for the feasibility study of future high-density UAV traffic in ADS-B-equipped airspace [17]. One possible usage of this limitation is in UAV flight approval. A UAV management framework called uFly was proposed to control the capacity of ADS-B-equipped UAV traffic over the air [4]. This capacity limitation applied to maintain the safety and efficiency of UTM operation. The last category in ADS-B research is security. This is one of the main concerns in ADS-B technology adaptation to UAVs, since ADS-B protocol does not include any security features. In this category, it covers the tool for detecting security attacks and some possible solutions. The first proposed detecting tool was a probabilistic model checking (PMC) tool. The tool could model masquerading, direct access, and denial of service (DoS) attacks [46]. The second tool used spectrum-sensing algorithms to differentiate ADS-B and UAV signals. It used serial segmentation sensing multi-mode to combine ADS-B and UAV signals. Then, based on a zero-IF structure, it verified the UAV identity [47]. Once researchers know the type of security attack in ADS-B, researchers can explore the solutions. There are two types of research on the improvement of ADS-B protocols in including a security feature. The first research proposed the usage of the blockchain method as a secure authentication platform during flight planning approval. Then, it encoded the authentication payloads in the broadcasted message during flight [48]. The second research developed an authentication method by monitoring the signal transmission time between the senders and the receivers. The actual transmission time was calculated based on a tiny timestamp value. Hence, it is called “ADS-B with timestamp” (ADS-BT) [2]. Both types of research required slight changes in ADS-B protocol to include additional security features. However, the changes in the ADS-B protocol needs an additional process for approval by the authority.4.2. ADS-B-Like Research
The ADS-B-like communication system mimics ADS-B protocol but uses different transmission technology. So far, it is not regulated by any regulations. It comes from the research community as a suggestion to include widely available communication means to be used in UTM. Researchers found many publications on it, which can be categorized into surveillance, detect and avoid, capacity, security, communication, and controlling categories. The ADS-B-like system can provide position information on nearby UAVs as the surveillance function in UTM. The communication technologies used in ADS-B-like communications as surveillance systems include radio frequency link, telemetry, APRS, LoRaWAN, LTE/4G, and Link SAC. The first research developed tools to generate automated flight paths and analyze the coverage of radio frequency links along an intended flight path. It aimed to minimize the likelihood of radio frequency link loss during a flight. The tools intended to ensure that the UAV position is always monitored [49]. The second communication used for ADS-B-like surveillance is telemetry, which UAV hobbyists commonly use for manual flight. One research used telemetry to develop a geo-awareness system, in which the position of UAVs was captured from telemetry protocol [50]. The second research proposed software-defined radio transceivers combined with a machine learning algorithm to decode the UAV’s telemetry protocols from the unwelcome UAVs. This software, combined with the techniques of pattern recognition, could provide an integrated system for drone surveillance [51]. The third technology in communication for ADS-B-like surveillance is LoRaWAN combined with APRS. Two publications explained this system and examined the effectiveness of UAV surveillance under 400 feet of altitude. The system was able to monitor beyond visual line-of-sight (BVLOS) operation near suburban areas with flight distances up to 8 km [12][52]. Another research for leveraging the LTE/4G network was introduced for new surveillance of UAS operations. Under the name of the vigilant UAS surveillance communication concept, it could enable air-to-air communications [8]. In military contact, one publication mentioned a communication system called link-situational awareness and control (Link-SAC) for reliable UAV control and surveillance. This system required spectrum allocation and management, because Link-SAC needs a large bandwidth under the limited spectrum resource. Thus, spectrum sharing required allocation of an X-band uplink to Link-SAC [53]. All those technologies give a different area coverage and bandwidth. Based on the ADS-B-like surveillance technologies mentioned in the previous paragraph, some research conducted implementation in real UTM operation. The implementation of APRS systems was published in a report that consisted of 19 flight tests for surveillance. The recorded data included position and six degree-of-freedom flight data on the UTM cloud [16]. Another implementation used a multi-channel position broadcast solution based on Wi-Fi modules. This system aimed for a robust position transmission against a jamming signal [11]. The second research area in the ADS-B-like system is detect and avoid. In this area, safety is a major concern. There are several communication technologies used in detect and avoid functions, such as Wi-Fi, XBee, and DJI AeroScope. There are two publications that used Wi-Fi as a detect and avoid tool. The first publication presented a method to broadcast short messages within the service set identifier (SSID) of a Wi-Fi network. It found that the SSID was suitable for low-latency coordinate exchange in collision avoidance [54]. The second publication described the traffic management architecture and services for defining the separation distance between UAVs to ensure safe operation. The measurement result suggested that the scheme of Wi-Fi based messaging was a potentially useful tool for the UTM [55]. The other communication type in ADS-B-like systems for the detect and avoid category is a commercial sensor called DJI AeroScope. There are two pieces of research that used this sensor. The first one was used for UAV detection near Florida’s Orlando Melbourne International Airport (KMLB) [39], and the second one was used near Daytona Beach International Airport (KDAB) [37]. Both publications analyzed the recorded UAV data combined with ADS-B data from manned flights. They pointed out the potential benefit of using such technology for real-time detection applications. One more publication evaluated XBee communication as an ADS-B-like system for the detect and avoid function. The system was successfully implemented in a flight test using a detect, predict, and avoid algorithm [19]. In support of ADS-B-like usage as a detect and avoid function, a risk assessment was conducted to evaluate LoRaWAN, 4G, XBee, and APRS technologies. Using UAS logistic delivery case studies, the research conducted an assessment on the ground risk and air risk. The result mentioned acceptable data to support the UAS logistic delivery with adequate path planning [56]. However, the case study was only conducted in remote and suburban areas. Unlike ADS-B which needs protocol changes to include a security feature, ADS-B-like communication is open for any new protocol to improve its security. Researchers found only one publication in this area, perhaps due to the security features researched in other research fields that are not only dedicated to UAVs, such as information technology. The research proposed a stronger authentication mechanism in the 5G network for UAV communication. It was inspired from the idea of second-factor authentication, which depends on a unique drone digital identity [57]. Perhaps, other security features of the ADS-B-like system should be tested and verified. Furthermore, one of the advantages of the ADS-B-like system is its ability to transmit payload data on its protocol. The technologies that support this feature are XBee and the 4G/5G cellular network. One publication used stereoscopic vision as a tool for sensing and detecting obstacles and other aircrafts. The video data from the ZED stereo camera were sent to the ground control station via XBee radio to be analyzed, to get the depth maps of the surroundings [58]. Another publication implemented a 4G cellular network for UAVs to transmit their location data to the cloud. Then, the ground base station retrieved the aggregated information to broadcast it to the ADS-B-enabled aircrafts via ADS-B technology [41]. This data communication link made real-time information transmission from UAVs possible. The last research area in the ADS-B-like system is its usage as a control and command function. Since the controlling function is a critical component of UAVs, its availability is the top priority. One research used a radio frequency link as the control and command communication. It developed a tool to analyze link coverage within an intended flight path. It also worked as an automated path development tool, which generated mission plans to minimize the likelihood of radio frequency link disruption [49]. Another research on the military side introduced Link-SAC to transmit the control and command signal to UAVs. Since the Link-SAC required a large bandwidth to support its reliability, spectrum sharing was employed to allocate the required bandwidth [53]. Hence, the ADS-B-like system could support several UTM functionalities with one type of communication technology.4.3. Remote ID Research
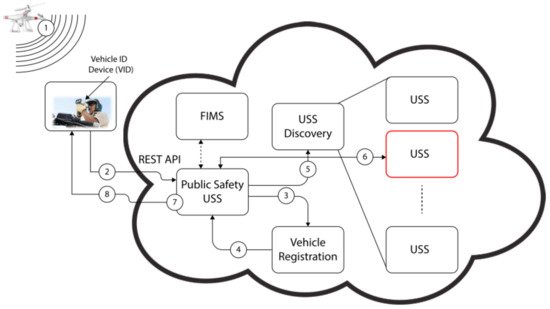
Remote ID protocol was introduced to identify the nearby UAV with verification based on its unique ID. It is relatively new compared to ADS-B and ADS-B-like systems; thus, fewer publications were found for this system. Besides security research, this system also attracts researchers to explore and use it for detect and avoid functions, capacity estimation, and communication. There are three publications using Remote ID to detect and avoid. However, the technology used in each publication was different; one was LoRaWAN [5], dedicated short-range communication (DSRC) [7], and the other was Bluetooth 5 [6]. The first publication explored Remote ID using LoRaWAN with its ground station to identify UAVs that intentionally or unintentionally fly through a restricted zone [5]. The other two publications used Remote ID as a vehicle-to-vehicle (V2V) communication. The first one used DSRC protocol to broadcast data including the position, which was used to detect and avoid UAVs [7]. The latter used Bluetooth 5 to detect and avoid between UAV and manned helicopter [6]. Although Remote ID broadcast coverage is considered smaller than ADS-B or ADS-B-like systems, it is large enough for detect and avoid functions in UTM. The second research area in which Remote ID was used is capacity estimation. This publication explained the simulation used to assess the Bluetooth and Wi-Fi performance, to broadcast the Remote ID protocol. It found that to avoid saturation, a significant number of ground antennas will be required to support high-density traffic [59]. It is related to the small coverage area of Remote ID broadcast. Although Remote ID was introduced for UAV security purposes, some researchers conducted research to improve and verify its security capability. Three publications suggested the improvement of UAV authentication. First, the blockchain and smart contact concepts were introduced to generate the ID and verify it using the Ethereum platform [60]. It is like the digital currency concept. Second, a privacy-preserving authentication framework was introduced that verifies the flying UAVs identity anonymously. This framework was based on the digital signature scheme of Boneh–Gentry–Lynn–Shacham (BGLS) [61]. The third publication used an embedded subscriber identification module (eSIM). The security analysis of this concept was verified using the ProVerif platform [62]. These last two concepts employed the digital signature concept to improve Remote ID security. Moreover, the verification test of security features for Remote ID was conducted by NASA flight demonstrations in UTM TCL 3 and 4 projects. The TCL 3 project verified a Remote ID broadcast operation in which UAVs were registered with UTM public key infrastructure (PKI) and broadcasted its messages. The messages were received properly and were identified by authorities on the ground [38]. The TCL 4 project demonstrated the capability of UTM-enabled Remote ID in several scenarios. It was used to identify and contact UAV operators in the vicinity and monitor security responses of UAV flights near an airport. Additionally, it simulated a scenario in which a low-battery UAV was forced to land quickly, affecting nearby operations to re-plan and restrain the landing vehicle [63]. Based on these flight demonstrations, the FAA decided to enforce Remote ID usage in UAVs by 2023. The last research area in the Remote ID category explored by researchers is the communication process to retrieve the verification information from the authority database. One research proposed a framework for fast retrieving UAS information based on NASA’s UTM concept. The framework consisted of vehicle registration, USS (UAS service supplier), FIMS (flight information management system), and model database. The result showed that information retrieval time was 1.2 s [14]. Another publication proposed an anonymous remote identification (ARID) framework, which used ephemeral pseudonyms. In this entry, only an authorized authority, such as the FAA, could retrieve the complete information of the UAV and its operator. The result showed a much faster processing time of 11.23 ms [64]. Although its result is much faster than the first publication, the framework is not well known and examined.References
- Carrio, A.; Lin, Y.; Saripalli, S.; Campoy, P. Obstacle Detection System for Small UAVs using ADS-B and Thermal Imaging. J. Intell. Robot. Syst. 2017, 88, 583–595.
- Kim, Y.; Jo, J.-Y.; Lee, S. ADS-B vulnerabilities and a security solution with a timestamp. IEEE Aerosp. Electron. Syst. Mag. 2017, 32, 52–61.
- Languell, Z.P.; Gu, Q. Securing ADS-B with Multi-Point Distance-Bounding for UAV Collision Avoidance. In Proceedings of the 2019 IEEE 16th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Monterey, CA, USA, 4–7 November 2019; pp. 145–153.
- Pan, Y.; Li, S.; Li, B.; Bhargav, B.; Ning, Z.; Han, Q.; Zhu, T. When UAVs coexist with manned airplanes: Large-scale aerial network management using ADS-B. Trans. Emerg. Telecommun. Technol. 2019, 30, e3714.
- Ghubaish, A.; Salman, T.; Jain, R. Experiments with a LoRaWAN-Based Remote ID System for Locating Unmanned Aerial Vehicles (UAVs). Wirel. Commun. Mob. Comput. 2019, 2019, 1–11.
- Kubo, D.; Osedo, A.; Yasui, I. Low Altitude Situational Awareness Enhancement using Remote ID Broadcasted from small UAS. In AIAA AVIATION 2020 FORUM; American Institute of Aeronautics and Astronautics: Reston, VA, USA, 2020; Volume 1, pp. 6–13.
- Murrell, E.; Walker, Z.; King, E.; Namuduri, K. Remote ID and Vehicle-to-Vehicle Communications for Unmanned Aircraft System Traffic Management. Res. Adv. Technol. Digit. Libr. 2020, 12574, 194–202.
- Orrell, G.L.; Chen, A.; Reynolds, C.J. Small unmanned aircraft system (SUAS) automatic dependent surveillance-broadcast (ADS-B) like surveillance concept of operations: A path forward for small UAS surveillance. In Proceedings of the 2017 IEEE/AIAA 36th Digital Avionics Systems Conference (DASC), St. Petersburg, FL, USA, 17–21 September 2017; Volume 2017.
- Azari, M.M.; Geraci, G.; Garcia-Rodriguez, A.; Pollin, S. Cellular UAV-to-UAV Communications. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; Volume 2019.
- Hosseini, N.; Jamal, H.; Haque, J.; Magesacher, T.; Matolak, D.W. UAV Command and Control, Navigation and Surveillance: A Review of Potential 5G and Satellite Systems. In Proceedings of the 2019 IEEE Aerospace Conference, Big Sky, MT, USA, 2–9 March 2019; Volume 2019, pp. 1–10.
- Minucci, F.; Vinogradov, E.; Pollin, S. Avoiding Collisions at Any (Low) Cost: ADS-B Like Position Broadcast for UAVs. IEEE Access 2020, 8, 121843–121857.
- An ADS-B Like Communication for UTM. In Proceedings of the 2019 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 9–11 April 2019; Volume 2019, pp. 1–12.
- International Civil Aviation Organisation. ADS-B Implementation and Operations Guidance Document; International Civil Aviation Organisation: Montreal, QC, Canada, 2020; Volume 13.
- Ishihara, A.K.; Rios, J.; Venkatesan, P. Remote UAS ID for Rapid Assessment of Flight and Vehicle Information. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019.
- ASTM F3411-19; Standard Specification for Remote ID and Tracking; ASTM International: West Conshohocken, PA, USA, 2020.
- Lin, Y.-H.; Lin, C.E.; Chen, H.-C. ADS-B Like UTM Surveillance Using APRS Infrastructure. Aerospace 2020, 7, 100.
- Duffield, M.; McLain, T.W. A Well Clear Recommendation for Small UAS in High-Density, ADS-B-Enabled Airspace. In Proceedings of the AIAA Information Systems-AIAA , Grapevine, TX, USA, 9–13 January 2017.
- Sherman, T.; Elemy, T.; Retherford, M.; Cady, T.; Bhandari, S. Collision Avoidance System for Fixed-Wing UAVs using Ping-2020 ADS-B Transreceivers. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019; American Institute of Aeronautics and Astronautics (AIAA): Reston, VA, USA, 2019; pp. 1–9.
- Bhandari, S.; Curtis-Brown, N.; Guzman, I.; Sherman, T.; Tellez, J.; Gomez, E. UAV Collision Detection and Avoidance using ADS-B Sensor and Custom ADS-B Like Solution. In Proceedings of the AIAA Information Systems-AIAA , Grapevine, TX, USA, 9–13 January 2017; pp. 1–12.
- Tang, X.-M.; Chen, J.-D.; Li, T. Unmanned aerial vehicle trajectory data fusion based on an active and passive feedback system. Proc. Inst. Mech. Eng. Part G J. Aerosp. Eng. 2019, 234, 887–895.
- Zhang, H.; Yan, Y.; Li, S.; Hu, Y.; Liu, H. UAV Behavior-Intention Estimation Method Based on 4-D Flight-Trajectory Prediction. Sustainability 2021, 13, 12528.
- Lum, C.W.; Rotta, H.; Patel, R.; Kuni, H.; Patana-Anake, T.; Longhurst, J.; Chen, K. UAS Operation and Navigation in GPS-Denied Environments Using Multilateration of Aviation Transponders. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019.
- Duffy, B.; Glaab, L. Variable-power ADS-B for UAS. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–6.
- Palenska, M.; Brazdilova, S.L.; Casek, P.; Korenciak, L. Low-Power ADS-B for GA Operating in Low Altitude Airspace. In Proceedings of the 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA, 11–15 October 2020; pp. 1–10.
- Sallouha, H.; Chiumento, A.; Pollin, S. Aerial Vehicles Tracking Using Noncoherent Crowdsourced Wireless Networks. IEEE Trans. Veh. Technol. 2021, 70, 10780–10791.
- Sidibe, A.; Loubet, G.; Takacs, A.; Ferré, G.; Ghiotto, A. Miniature drone antenna design for the detection of airliners. Int. J. Microw. Wirel. Technol. 2021, 13, 21–27.
- Goossen, J.; Kim, J.; van der Hoeven, S. Development of a versatile ADS-B communications system. In Proceedings of the 2018 Texas Symposium on Wireless and Microwave Circuits and Systems (WMCS), Waco, TX, USA, 5–6 April 2018; pp. 1–4.
- Zhu, Y.; Shi, X.; Kang, K. UAV-Based Flight Inspection System. In Proceedings of the International Flight Inspection Symposium, Monterey, CA, USA, 16–20 April 2018; pp. 16–20.
- Alarcón, V.; García, M.; Alarcón, F.; Viguria, A.; Martínez, Á.; Janisch, D.; Acevedo, J.J.; Maza, I.; Ollero, A. Procedures for the Integration of Drones into the Airspace Based on U-Space Services. Aerospace 2020, 7, 128.
- Berdonosov, V.; Zivotova, A.; Naing, Z.H.; Zhuravlev, D.O. Speed Approach for UAV Collision Avoidance. J. Phys. Conf. Ser. 2018, 1015, 052002.
- Languell, Z.P.; Gu, Q. A Multi-Point Distance-Bounding Protocol for Securing Automatic Dependent Surveillance-Broadcast in Unmanned Aerial Vehicle Applications. J. Comput. Sci. Technol. 2020, 35, 825–842.
- Lee, Z.; Kumar, R.; Radmanesh, R.; Kumar, M.; Cohen, K. Application of fuzzy logic for developing sense and avoid techniques for uav flight operations in national airspace. In Dynamic Systems and Control Conference; American Society of Mechanical Engineers: New York, NY, USA, 2020; Volume 2.
- Radmanesh, M.; Kumar, M.; Sarim, M. Grey wolf optimization based sense and avoid algorithm in a Bayesian framework for multiple UAV path planning in an uncertain environment. Aerosp. Sci. Technol. 2018, 77, 168–179.
- Pierpaoli, P.; Rahmani, A. UAV collision avoidance exploitation for noncooperative trajectory modification. Aerosp. Sci. Technol. 2018, 73, 173–183.
- Berdonosov, V.; Zivotova, A.; Zhuravlev, D.; Naing, Z.H. Implementation of the Speed Approach for UAV Collision Avoidance in Dynamic Environment. In Proceedings of the 2018 International Multi-Conference on Industrial Engineering and Modern Technologies (FarEastCon), Vladivostok, Russia, 3–4 October 2018; pp. 1–6.
- Burke, P.J. Small Unmanned Aircraft Systems (SUAS) and Manned Traffic near John Wayne Airport (KSNA) Spot Check of the SUAS Facility Map: Towards a New Paradigm for Drone Safety Near Airports. Drones 2019, 3, 84.
- Wallace, R.J.; Kiernan, K.W.; Haritos, T.; Robbins, J.; D’souza, G.V. Evaluating small UAS near midair collision risk using Aero Scope and ADS-B. Int. J. Aviat. Aeronaut. Aerosp. 2018, 5, 2.
- Aweiss, A.; Homola, J.; Rios, J.; Jung, J.; Johnson, M.; Mercer, J.; Modi, H.; Torres, E.; Ishihara, A. Flight Demonstration of Unmanned Aircraft System (UAS) Traffic Management (UTM) at Technical Capability Level 3. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–7.
- Mott, J.H.; Marshall, Z.A.; Vandehey, M.A.; May, M.; Bullock, D.M. Detection of Conflicts Between ADS-B-Equipped Aircraft and Unmanned Aerial Systems. Transp. Res. Rec. J. Transp. Res. Board 2020, 2674, 197–204.
- Jacob, J.; Mitchell, T.; Loffi, J.; Vance, M.; Wallace, R. Airborne visual detection of small unmanned aircraft systems with and without ADS-B. In Proceedings of the 2018 IEEE/ION Position, Location and Navigation Symposium (PLANS), Monterey, CA, USA, 23–26 April 2018; pp. 749–756.
- Meer, I.A.; Ozger, M.; Lundmark, M.; Sung, K.W.; Cavdar, C. Ground Based Sense and Avoid System for Air Traffic Management. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; pp. 1–6.
- Arpaio, M.J.; Paolini, G.; Fuschini, F.; Costanzo, A.; Masotti, D. An All-in-One Dual Band Blade Antenna for ADS-B and 5G Communications in UAV Assisted Wireless Networks. Sensors 2021, 21, 5734.
- Siewert, S.; Sampigethaya, K.; Buchholz, J.; Rizor, S. Fail-Safe, Fail-Secure Experiments for Small UAS and UAM Traffic in Urban Airspace. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019; pp. 1–7.
- Svanstrom, F.; Englund, C.; Alonso-Fernandez, F. Real-Time Drone Detection and Tracking with Visible, Thermal and Acoustic Sensors. In Proceedings of the 2020 25th International Conference on Pattern Recognition (ICPR), Milan, Italy, 10–15 January 2020; pp. 7265–7272.
- Grzybowski, J.; Latos, K.; Czyba, R. Low-Cost Autonomous UAV-Based Solutions to Package Delivery Logistics. In Advanced, Contemporary Control; Springer: Berlin/Heidelberg, Germany, 2020; pp. 500–507.
- Shaikh, E.; Mohammad, N.; Muhammad, S. Model Checking Based Unmanned Aerial Vehicle (UAV) Security Analysis. In Proceedings of the 2020 International Conference on Communications, Signal Processing, and their Applications (ICCSPA), Sharjah, United Arab Emirates, 16–18 March 2021; pp. 1–6.
- Wang, J.; Song, D.; Liang, R.; Han, P. ADS-B and UAV Signal Monitoring System Design Based on Spectrum Sensing. In Proceedings of the 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China, 24–26 May 2019; pp. 422–426.
- Wu, Y.; Dai, H.-N.; Wang, H.; Choo, K.-K.R. Blockchain-Based Privacy Preservation for 5G-Enabled Drone Communications. IEEE Netw. 2021, 35, 50–56.
- Bateman, A.J.; Burkholder, J.; Summers, T.; Richards, N.D. Incorporating RF Coverage Analysis in Mission Planning for Future Airspace Operations. In Proceedings of the AIAA Scitech 2019 Forum, San Diego, CA, USA, 7–11 January 2019.
- Kunze, S.; Weinberger, A. Concept for a Geo-Awareness-System for Civilian Unmanned Aerial Systems. In Proceedings of the 2021 31st International Conference Radioelektronika (RADIOELEKTRONIKA), Brno, Czech Republic, 19–21 April 2021; pp. 1–6.
- Yue, X.; Liu, Y.; Wang, J.; Song, H.; Cao, H. Software Defined Radio and Wireless Acoustic Networking for Amateur Drone Surveillance. IEEE Commun. Mag. 2018, 56, 90–97.
- Lin, C.E.; Shao, P.-C.; Lin, Y.-Y. System Operation of Regional UTM in Taiwan. Aerospace 2020, 7, 65.
- Baek, H.; Lim, J. Design of Future UAV-Relay Tactical Data Link for Reliable UAV Control and Situational Awareness. IEEE Commun. Mag. 2018, 56, 144–150.
- Minucci, F.; Vinogradov, E.; Sallouha, H.; Pollin, S. UAV Location Broadcasting with Wi-Fi SSID. In Proceedings of the 2019 Wireless Days (WD), Manchester, UK, 24–26 April 2019.
- Vinogradov, E.; Minucci, F.; Pollin, S. Wireless Communication for Safe UAVs: From Long-Range Deconfliction to Short-Range Collision Avoidance. IEEE Veh. Technol. Mag. 2020, 15, 88–95.
- Shao, P.-C. Risk Assessment for UAS Logistic Delivery under UAS Traffic Management Environment. Aerospace 2020, 7, 140.
- Abdel-Malek, M.A.; Akkaya, K.; Bhuyan, A.; Cebe, M.; Ibrahim, A.S. Enabling Second Factor Authentication for Drones in 5G using Network Slicing. In Proceedings of the 2020 IEEE Globecom Workshops (GC Wkshps), Taipei, Taiwan, 7–11 December 2020; pp. 1–6.
- Perez, E.; Winger, A.; Tran, A.; Garcia-Paredes, C.; Run, N.; Keti, N.; Bhandari, S.; Raheja, A. Autonomous Collision Avoidance System for a Multicopter using Stereoscopic Vision. In Proceedings of the 2018 International Conference on Unmanned Aircraft Systems (ICUAS), Dallas, TX, USA, 12–15 June 2018; Volume 91768, pp. 579–588.
- Kuroda, V.; Egorov, M.; Munn, S.; Evans, A. Unlicensed Technology Assessment for Uas Communications. In Proceedings of the 2020 Integrated Communications Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 8–10 September 2020; pp. 1–12.
- Alkadi, R.; Shoufan, A. Unmanned Aerial Vehicles Traffic Management Solution Using Crowd-sensing and Blockchain. IEEE Trans. Netw. Serv. Manag. 2021, 1–14.
- Alsoliman, A.; Bin Rabiah, A.; Levorato, M. Privacy-Preserving Authentication Framework for UAS Traffic Management Systems. In Proceedings of the 2020 4th Cyber Security in Networking Conference (CSNet), Lausanne, Switzerland, 21–23 October 2020.
- Shoufan, A.; Yeun, C.Y.; Taha, B. eSIM-Based Authentication Protocol for UAV Remote Identification. In Security and Privacy in the Internet of Things; Wiley: New York, NY, USA, 2021; pp. 91–122.
- Rios, J.L.; Aweiss, A.S.; Jung, J.; Homola, J.; Johnson, M.; Johnson, R. Flight Demonstration of Unmanned Aircraft System (UAS) Traffic Management (UTM) at Technical Capability Level. In Proceedings of the AIAA AVIATION 2020 Forum, Virtual, 15–19 June 2020.
- Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. ARID: Anonymous Remote IDentification of Unmanned Aerial Vehicles. In Proceedings of the Annual Computer Security Applications Conference, Association for Computing Machinery (ACM). New York, NY, USA, 6–10 December 2021; pp. 207–218.
