Wireless sensor networks (WSNs) have been applied in networking devices, and a new problem has emerged called source-location privacy (SLP) in critical security systems. In wireless sensor networks, hiding the location of the source node from the hackers is known as SLP. The WSNs have limited battery capacity and low computational ability. Many state-of-the-art protocols have been proposed to address the SLP problems and other problems such as limited battery capacity and low computational power. One of the popular protocols is random path routing (RPR), and in random path routing, the system keeps sending the message randomly along all the possible paths from a source node to a sink node irrespective of the path’s distance. The problem arises when the system keeps sending a message via the longest route, resulting because of high battery usage and computational costs.
- wireless sensor network
- source-location privacy
- calculated random path routing
- modeling
- Petri nets
1. Introduction
2. The CRPR model
Figure 1 shows the proposed methodology of the model. The CPN tool is used to formally model in the model. The token from a source node to the destination node is sent by using calculated random path routing. First, the model has to find all the possible available paths to send the packet from source to destination. The model has traversed all the possible nodes of that path and gets the calculated path distance. Before sending the packet to the network, the model has all the routes from the source node to the sink node. Now the model has the choice to send the packet from either the shortest path or longest path. It depends upon the token to be sent. The model can send the message from the shortest path again and again if the message does not contain critical information.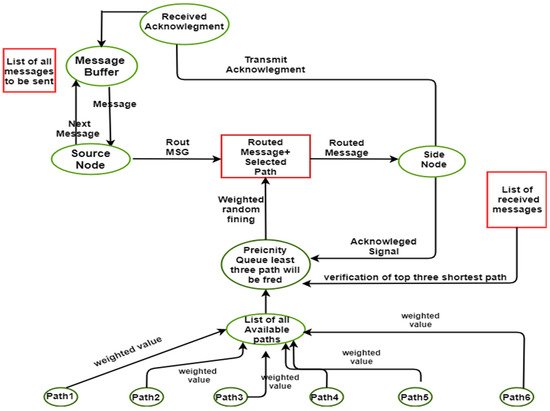
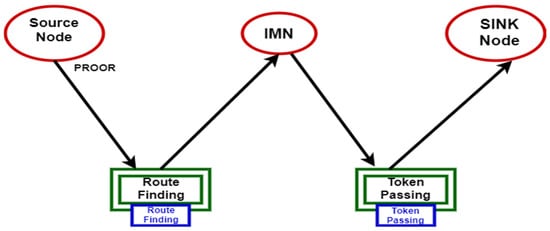
3. Hieratical Colored Petri Nets
-
Route finding
-
Token passing
3.1. Route Finding
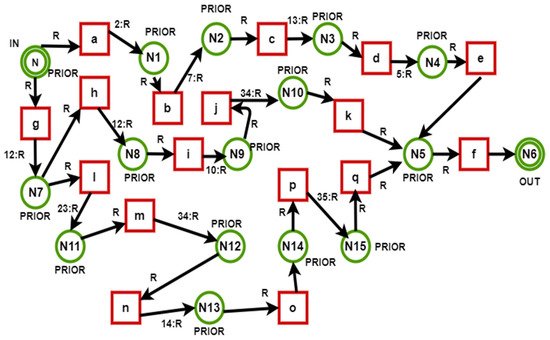
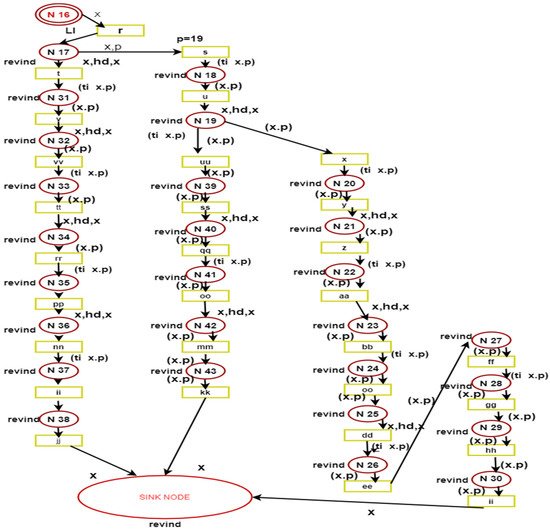
3.2. Token Passing
-
Pin (path routing) = [] (Pin input for the module, and [] is the empty list)
-
Pout (calculated distance) = [list of all paths distance] (Pout is the module’s output that contains paths distance)
4. Comparison of CRPR with Other Similar Routing Techniques
| Protocol | Formally Modeled | Guard Checking | Multi-Path Routing | Reachability | Liveness |
|---|---|---|---|---|---|
| Phantom routing-based Techniques | NO | NO | NO | YES | YES |
| Fake sources-based Techniques | NO | NO | YES | YES | YES |
| Dynamic Source routing | NO | YES | YES | NO | YES |
| Associativity- based routing | NO | NO | YES | YES | NO |
| Dynamic backup routes routing protocol | YES | NO | YES | NO | YES |
| Hint-based probabilistic protocol | NO | NO | YES | NO | NO |
| Shortest selective random path routing | YES | YES | YES | YES | YES |
5. Conclusions
Source-location privacy is an essential issue in routing protocols. With the invention of new and critical information transmission methods, the safe transmission of data is a critical issue. Routing protocols have managed to solve this problem, but there is always a margin for improvement. The model presented is ourthe best attempt to give positive input to solve this problem by improving the already existing random path routing protocol and naming it Calculated Random Path Routing (CRPR). The model considers the tradeoff between privacy and computational cost to improve the existing routing protocol.References
- Chakraborty, S.; Choi, H.; Srivastava, M. Demystifying privacy in sensory data: A QoI based approach. In Proceedings of the 2011 IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Seattle, WA, USA, 21–25 March 2011; pp. 38–43.
- Narayanan, A.; Thiagarajan, N.; Lakhani, M.; Hamburg, M.; Boneh, D. Location Privacy via Private Proximity Testing. In Proceedings of the NDSS Symposium 2011, San Diego, CA, USA, 6–9 February 2011.
- Manjula, R.; Computing, R.D.-P. A novel source location privacy preservation technique to achieve enhanced privacy and network lifetime in WSNs. Pervasive Mob. Comput. 2018, 44, 58–73.
- Bradbury, M.; Jhumka, A. A Near-Optimal Source Location Privacy Scheme for Wireless Sensor Networks. In Proceedings of the 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, NSW, Australia, 1–4 August 2017; pp. 409–416.
- Brauer, F.; Castillo-Chavez, C.; Feng, Z. Mathematical Models in Epidemiology; Springer: New York, NY, USA, 2019.
- Fong, D.Y. Wireless sensor networks. Internet Things Data Anal. Handb. 2017, 197–213.
