Ransomware attacks have emerged as a major cyber-security threat wherein user data is encrypted upon system infection. Latest Ransomware strands using advanced obfuscation techniques along with offline C2 Server capabilities are hitting Individual users and big corporations alike. This problem has caused business disruption and, of course, financial loss.
1. Introduction
Increased connectivity and digitization have facilitated cyber-criminals in designing and launching large-scale cyber-attacks targeting individuals and corporations worldwide. While individual naivete and lack of awareness enable these attacks to bypass basic security mechanisms, security vulnerabilities in the IT systems of small and large corporations are increasingly being exploited to cause business disruptions. The cyber-attack canvas keeps expanding rapidly as cyber-criminals consistently circumvent security provisions designed and deployed by organizations. Increasingly, the target of the attacks is data that is critical to individuals and organizations alike. Threat actors are cashing in on opportunities that can help them seize control of valuable data to demand a ransom from the data owner. Ransomware is a form of malware that infects a computer or multiple computers over a network, encrypting files and folders, rendering them unusable. Users are then prompted for a ransom typically to be paid in cryptocurrency. Ransomware is not a new threat, but its use is surging and causing heavy financial losses all over the world
[1]. It is a major challenge for cyber-security analysts and Reverse Engineers as typical Ransomware is not detected by anti-virus software due to its polymorphic nature.
According to
[2], almost 51% of the organizations worldwide were hit by highly sophisticated Ransomware attacks in 2020. These attacks were using advanced command and control servers, making them challenging to reverse engineer. Among all the countries studied in the report, India was affected the most by the deadly Ransomware attacks, with almost eighty-two percent of organizations being hit by Ransomware. Netwalker is one of the newest and dangerous Ransomware strands
[3]. Its popularity is the method of propagation, using phishing emails related to COVID-19, thus luring the victim to download the attachments resulting in the execution of the portable binaries and system infection. In February 2021, the latest Ransomware strand, Zeoticus 2.0, successor to the infamous strand Zeoticus was released. Zeoticus 2.0 has raised the stakes since it is now proving extremely hard to control and mitigate. It can execute completely offline without requiring any command and control server. For receiving the Ransom payment, Zeoticus uses highly secure and encrypted Proton mail accounts to evade tracing.
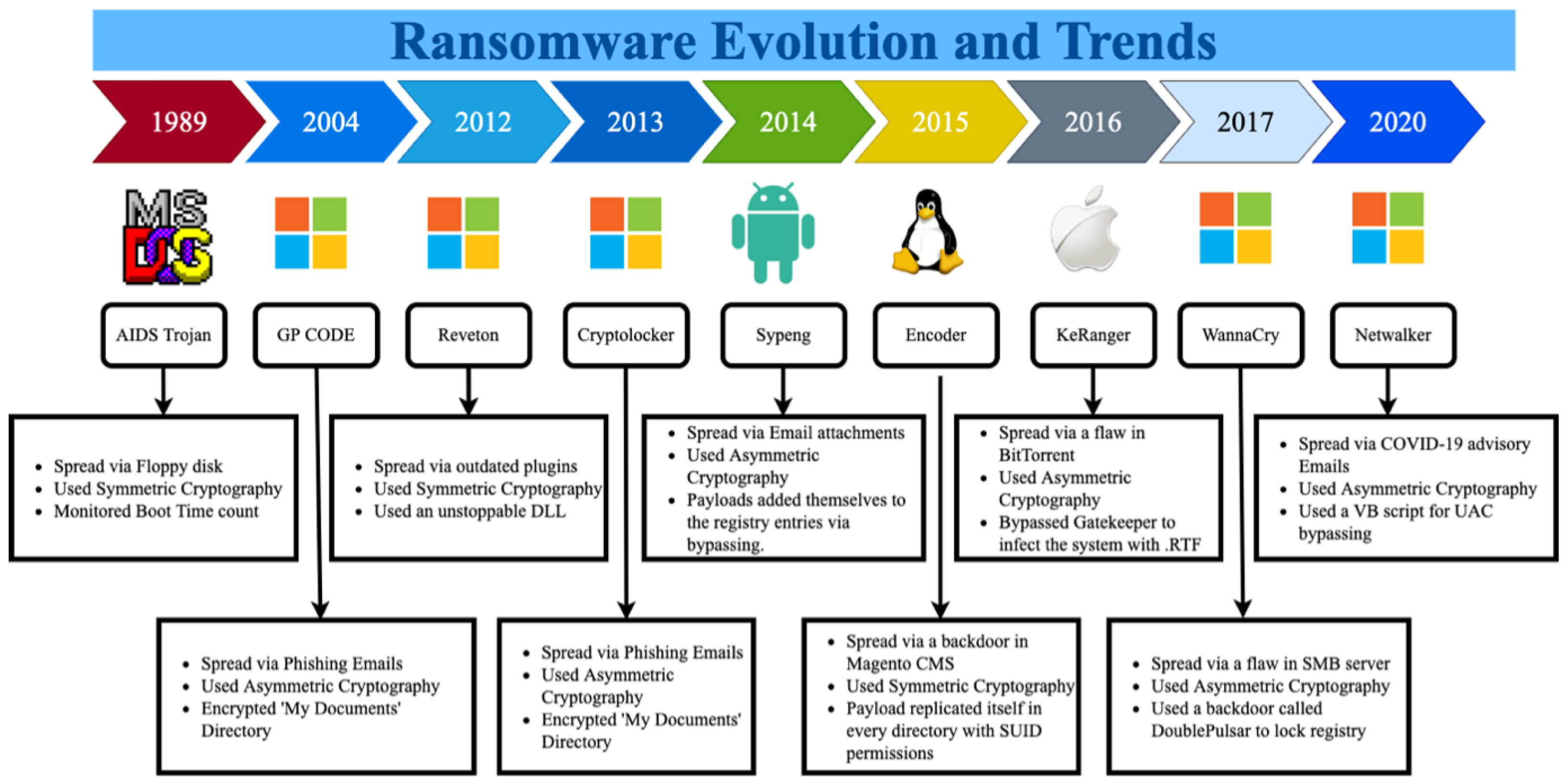
The history of Ransomware dates back to the late 1980s. The first Ransomware named Acquired Immunodeficiency Syndrome (AIDS) Trojan, was released via a floppy disk. The AIDS Trojan contained a program that would count the number of times a computer system was started, and once this count reached the number 90, all of the files would be encrypted. The only way to be able to use them again was to pay a ransom amount of $189
[4]. During the early days, Ransomware authors attacked victims to showcase their technical prowess. It was not until the early 2000s when cyber-criminals began to exploit users for financial gains as data gained primacy. In 2004, a Ransomware strand named GPCode was released. GPCode infected Windows Machines via e-mail attachments. It used a 660-Bit RSA key to encrypt files and folders
[5,6][5][6]. Since then, Ransomware families like WannaCry, Cerber, Petya, etc., have evolved and caused monetary damage worth billions of dollars.
Figure 1 depicts a timeline of the prevalence of Ransomware families.
Figure 1.
Ransomware timeline and trends.
2. State-of-the-Art
Researchers, cyber-security firms and government agencies have researched all aspects of Ransomware propagation, operation and devising effective combat techniques. Although, a few of them were adopted by organizations and governments; most of the frameworks have not proved successful in practice. This is due to the fact that security is multi-dimensional encompassing network security, data security, application security and finally individual Cyber-hygiene practices
[24][7]. It is therefore extremely challenging to design blanket security solutions. Several works have reviewed the impact of Ransomware and summarized techniques to counter its threat. Since, our work is focused on summarizing the existing detection, avoidance and mitigation techniques while providing insights to improve countermeasures, a comparative analysis with existing review papers is provided in
Table 1.
Table 1. Comparative analysis of the proposed survey with the state-of-the-art surveys on Ransomware detection, avoidance, and mitigation.
|
Researcher
|
Contribution
|
Pros
|
Cons
|
|
Aurangzeb et al. [25][8]
|
Evaluated attack methodologies for Windows Based Ransomware families.
|
The authors discussed all possible exploit vectors and kits used in creation of Windows based Ransomware
families.
|
They did not specifically propose any technical solutions required to counter Ransomware.
|
|
Tailor et al. [26][9]
|
Analyzed different encryption techniques used by modern Ransomware strands so as to develop better detection strategies.
|
The authors presented a comprehensive overview of different encryption techniques used by both Locker and Crypto Ransomware families.
|
Techniques proposed by the authors could include some implementation based details for effective detection of Ransomware.
|
|
Tandon et al. [27][10]
|
Explained the modus-operandi and architecture of typical Ransomware attacks.
|
The authors gave a detailed view of MS-017 exploit and how it eventually used Double Pulsar to cause the spread of WannaCry.
|
Discussions are presented in the context of a single Ransomware. Broad-based countermeasure strategies not provided.
|
|
Genç et al. [28][11]
|
Discussed the current Ransomware mitigation strategies and evaluated their effectiveness.
|
The authors explained the latest ransomware strands which can be generated using rootkits in addition to Ransomware of things.
|
Novel mitigation strategies for obfuscated Ransomware strands not suggested.
|
|
Oz et al. [29][12]
|
The authors summarized all the different Ransomware families based on the exploits that helped them propagate.
|
The tables and the summaries presented by the authors can be adopted by researchers to create new mitigation frameworks.
|
The authors did not discuss the solutions with respect to the latest families that use offline encryption techniques.
|
|
Kok et al. [30][13]
|
The authors’ research was focused on finding out the effectiveness of preexisting detection techniques and thus highlighted the requirement of an ML based solution to create better detection techniques.
|
The authors explained the Ransomware lifecycle in a novel manner and mapped it to the different techniques to find out their effectiveness.
|
The authors outlined an ML based solution using linear regression but did not technically explain its effectiveness over existing solutions.
|
|
The proposed survey
|
The authors discuss all possible Ransomware propagation techniques and put forth a Ransomware avoidance Continuum that can be adopted by organizations and individuals alike.
|
The authors presented a good overview of the adversary methodologies and performed a case study of one of the recent Ransomware strands, Djvu. Novel suggestions are put forth to contain the spread of Ransomware.
|
-
|
3. The DAM Framework for Ransomware Defense
3.1. Detection Techniques
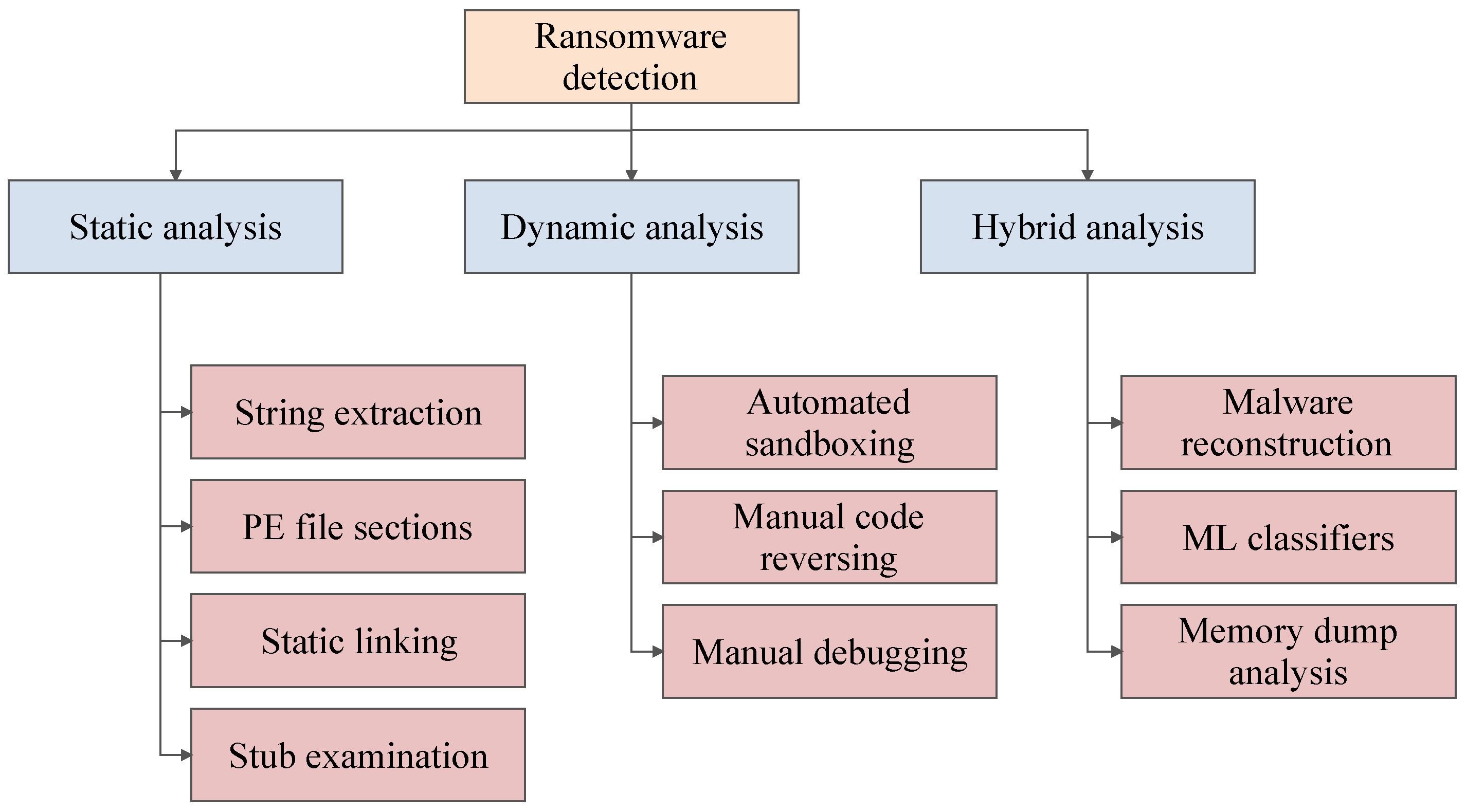
Various Ransomware detection techniques have been proposed by both academic researchers and industrial security experts. Some of them are currently in use as well. These techniques mostly work via static or dynamic analysis of the executable suspected to be Ransomware. Static analysis of an executable is performed through examination of the code without actually running the executable. Static analysis of a binary consists of static linking, locating American Source Code Information Interchange (ASCII) strings, packer detection and memory relocation. Dynamic analysis is performed after execution of the suspected Ransomware. During its execution, the actions and system calls made by the suspected file are recorded and based on this information, a final report is generated.
3.1.1. Static Analysis
Subedi et al.
[31][14] proposed a methodology that would utilize static analysis as an approach to detect Ransomware. The approach followed by the researchers contained a framework that would first reverse engineer the PE file using assembly language and then subsequently apply Dynamic Linkable Library (DLL) and function call extraction on the PE file. The Framework was developed as a tool called CRSTATIC. They analyzed forty-three Ransomware Samples with CRSTATIC using different parameters. This work was able to differentiate between Ransomware and Normal Programs via a Cosine similarity graph based on assembly instructions. Although, relatively new, CRSTATIC cannot detect the latest ransomware families which deploy signature evasion techniques. Despite its drawbacks, CRSTATIC used pre-parse, a lightweight parser that could detect malicious PE files with respect to different parameters like relocations and byte read operations. CRSTATIC was not able to detect Locker Ransomware families.
Zheng et al.
[32][15] devised a tool called GreatEatlon for detecting Android Ransomware. This tool was created by combining the features present in Heldroid
[33][16], APKTool and other open source analysis tools. GreatEatlon used four stages to identify the presence of Ransomware on an Android Device. The first stage was to follow the code flows of an executable suspected to be a Ransomware. Any Ransomware’s first line of action is to find the files it wants to encrypt. GreatEatlon was easily able to identify the path of Ransomware by utilizing an extension of FlowDroid
[34][17], a state-of-the-art technique used for analyzing code flows of Android applications. GreatEatlon then passed the Executable through the second stage in which DeviceAdmin APIs were inspected when the executable was allowed to run. If the APIs were misused by the executable to escalate its privileges, then it would be flagged as malicious. Last two stages deployed static and manual analysis techniques to finally identify the behavior of the suspected executable file.
Hsiao et al.
[35][18] conducted reverse engineering experiments on the infamous WannaCry Ransomware to understand how the malicious binary works. The mode of analysis used by the authors was Static analysis. IDA Pro
[36][19] was used for reverse engineering to understand the inner working of the Ransomware. The PE file which was initially used for the first stage of Ransomware operation converted itself into different formats in the subsequent stages. First, the PE file is delivered through the Eternal Blue exploit
[37][20] which then uses a Windows API to embed itself. In the next phase, two services, mssecsvc.exe and tasksche.exe are responsible for further propagation by altering the environment settings. The third stage is responsible for the overall encryption of the victim’s data where taskche.exe loads the encryption .dll in the device’s memory. The last stage is maintained by C2C servers for tracing the payments and the course of infection.
3.1.2. Dynamic Analysis
Sgandurra et al.
[38][21] tested 542 different samples of Ransomware families through EldeRan, a hybrid approach comprising of machine learning techniques and dynamic code analysis. EldeRan tested application samples against a set of parameters that would be able to identify if the sample is a Ransomware during the infection phase. EldeRan successfully analyzed Windows API calls, Registry Key operations, file and directory operations, dropped files and embedded strings. The next component of EldeRan involved the Machine Learning approach that comprised of feature selection that could distinguish Ransomware from a regular software via Mutual information criteria
[39][22] and classification that used Regularized logistic regression. Overall, EldeRan achieved a great success rate in detection of new Ransomware families.
Maimó et al.
[40][23] were the first authors to discuss the impact of Ransomware on Clinical environments. The first ever Ransomware to target the medical industry was WannaCry. Upon its outbreak, all the NHS operations were put to a halt and most of the appointments and surgeries were canceled. They devised a ML based technique compatible with Integrated Clinical Environment (ICE) architecture that could detect the presence of a Ransomware before it could even start propagating. Their technique was able to detect the changes in network traffic when the Ransomware was being run. These patterns were then fed to a probabilistic supervised Ransomware classifier to finally extract complex features of the sample being run. The solution proposed had four main components. The first module monitored traffic patterns resulting from a live sample. The next module required human supervision for generating a suitable dataset that would be fed to the ML algorithms for detection and classification of Ransomware. The third module identified the anomalous patterns and labeled them. The last module focused on mitigation techniques through the aid of Rule based ML models.
Kao et al.
[41][24] conducted another reverse engineering experiment on WannaCry Ransomware through Dynamic mode of analysis. In this case, WannaCry sample was run on the system and its interactions with processes, file system, registry and network activity were recorded. The authors used a tool named YARA to record the signature of the sample. To carry out behavioral analysis dynamically, SysInternals Suite and Wireshark were made use of. WannaCry being a multi-stage Ransomware uses a process to load the tasksche.exe file that in turn launches different processes.
When a ransomware attack occurs, it is really important to detect it as early as possible because in this case, every second is significant as early detection results in a lesser degree of damage. Morato et al.
[42][25] devised an algorithm called REDFISH which claimed to detect the presence of ransomware in an organizational setting way before all the frameworks till date through analysis of network traffic. The authors used around 19 ransomware families to test their algorithm. This algorithm was designed to tackle ransomware strands that were created to encrypt files and folders present in shared networking drives in Network Attached Storage. After carefully evaluating all the environments where Ransomware can persist, the authors found out that existence of SMB in a network indicated a possible habitat where Ransomware can dwell in. They used a network traffic inspection device to analyse the behaviour of incoming and outgoing traffic. They analysed the usage of SMB based commands very closely to look for anomalies in the traffic. The authors ran several tests on the algorithm and reported that REDFISH can detect ransomware within 20 s. The authors stated that although REDFISH proved to be fast but the strands were still able to lock 10 to 15 files before being detected. We believe REDFISH is a feasible algorithm for organizational settings and can be easily deployed because of its minimal impact on the server resources. Also, the network inspection device used by REDFISH stays out of the production network, so any malware which also has the ability to launch reverse shells for an attacker would not be able to deactivate the detection mechanism
[43][26]. However, in the modern scenarios where ransomware is highly stealthy in nature, this algorithm can fail. Recently, there is a surge of Ransomware strands that use Microsoft Word and Excel based documents to deliver themselves onto the victims’ machines. VBA and Excel macros can obfuscate PowerShell code within their streams so that when they are passed through antivirus scans, they are deemed to be benign. We strongly believe that in cases like these, REDFISH will not be able to detect the ransomware strands within the stipulated time frame.
Chen et al.
[44][27] created an automated early detection tool with a novel feature of pattern extraction. Their tool was able to capture new strands and samples through the sandbox and was able to prepare an automated analytic report. The report was able to present the most unique patterns and behavioural paths followed by different ransomware families. For experimentation and validation, the authors used seven ransomware families. Through the results of experimentation, the authors were able to find out the efficiency of each of the algorithms used for pattern extraction. In order to unsheathe the features of different ransomware families, they used TF-IDF, ET and LDA to automate the whole process. The tool developed by the authors can be used in medium to large enterprises as it can easily handle large log data and detect ransomware before other industry standard solutions. The approach used by the authors focused on calculating the time efficiency of different algorithms but they did not compare their tool with other frameworks and algorithms in effect. Also, the algorithms used require training before they can make intelligent decisions. The algorithms will not work well for the latest strands like Darkside
[45][28].
Imtiaz et al.
[46][29] approached the problem of Android Ransomware by using a novel methodology called DeepAMD. DeepAMD used deep ANNs for detecting ransomware before it could exploit other applications on the smartphone. DeepAMD used a dataset to extract features
[44][27] initially for feature selection. The cleansed data resulting from feature extraction was analysed both statically and dynamically to deem the nature of an application. Overall, DeepAMD proved to be a novel and effective approach for early detection of the most advanced ransomware families. This is because of a good rate of validation of DeepAMD using the latest and updated Android Malware dataset
[47][30]. In addition to detection of Ransomware, DeepAMD can also detect scareware
[48][31] and adware
[49][32] families.
Kok et al.
[50][33] developed a new algorithm called Pre-Encryption Detection Algorithm (PEDA) that was able to detect Crypto Ransomware which is the most dominant type of Ransomware. According to the authors, PEDA could detect almost all crypto Ransomware strands in their pre-encryption stage
[51][34]. PEDA is a hybrid algorithm that first examines a suspicious binary via static analysis through checksum comparison and then dynamically via the usage of an algorithm that monitor pre-encryption
[52][35] APIs. Along with this, PEDA also identified 3 APIs that could locate the presence of Ransomware. The algorithm’s success held true for most of the Crypto strands. The only limitation of PEDA is its high dependence on Windows API. So, if PEDA is deployed as the only detection mechanism, it might not be able to detect the latest families.
Al-rimy et al.
[53][36] also created a model for early detection of Crypto Ransomware but through a different approach. The model used two detection modules, one for analysing the behaviour and the second for estimation of anomalies. Fusion of both the results would then give a proper decision on whether the binary is malicious or benign. The authors claimed that this model would certainly be able to detect zero day attacks and advanced persistent threats. Through the results shown in the work, the model performed extremely well in detecting the ransomware strands from a dataset of 12,000 applications. One benefit of using this solution is that it can be used for other ecosystems too because of the extremely low false positive rate.
Figure 2 illustrates the main analysis techniques for detection along with their sub types.
Figure 2. Taxonomy of Ransomware detection techniques.
Ransomware detection techniques have matured in their combat effectiveness against major ransomware attacks. Detection techniques are now hybrid in nature and most of these deploy AI based strategies for improving detection effectiveness. Despite the advancement in the detection techniques, the latest Ransomware families continue to evade them as these techniques are not designed to contain all of the Ransomware strands at once. Solutions for Detection are created mostly to detect a single strand or a single type of Ransomware, so generic solutions do not exist as they are extremely challenging to develop. Some are even designed to just detect only one version of a particular Ransomware. So, it is evident that current state of the detection techniques is reactive in nature and developed in response to new ransomware releases.
3.2. Ransomware Avoidance Techniques
Ransomware attacks have been successful mostly because of poor Cyber-hygiene practices. The avoidance techniques available for the masses to protect their devices from the deadly Ransomware are very few in number and are generalized in nature. Researchers have proposed a few advanced techniques for Ransomware avoidance, but they are limited to specific environments and specific strands of Ransomware and hence do not qualify as one-for-all solution.
General techniques that can be followed by users to protect their devices from Ransomware are:
3.2.1. Regular Patches and Updates
When the WannaCry Ransomware hit the world in 2017, it created a chaos everywhere and rendered all the ICE computers useless, bringing the operations at most of the hospitals and clinics in UK to a halt. WannaCry caused infection of devices through the exploitation of a vulnerability in the SMB protocol. SMB is a Windows based protocol that allows the computers to share files when they are on the same domain. An exploit kit named as Eternal Blue was used to exploit the vulnerability and this is how WannaCry after entering one device, infected the whole network. Computing Platforms which are regularly patched and updated have an extremely low chance of being infected with a Ransomware as most of the attackers’ prey upon vulnerabilities that have not been patched. Updating and Patching is not just limited to Operating Systems. Browsers and other applications that are live on the network should be updated and patched regularly.
3.2.2. Avoid e-Mails from Unknown Sources and Attachments
Emails from unknown senders should not be opened as they can carry links and attachments which if opened can install Ransomware on the devices. Emails meant for delivering Ransomware are usually very compelling and entice the recipient to click on the links or download the attachments. Organizations should conduct a training for employees to help them identify phishing emails. Attackers can attack a specific department of the organization. For example, the Inventory Department can receive an email with a billing attachment from an attacker posing to be a legitimate dealer
[60][37]. Use of email filters and spam detection extensions should be deployed for all email services.
3.2.3. Disable JavaScript and Java for Browsers
Another important technique to prevent Ransomware spread is to disable JavaScript and Java on Browsers. Malvertising, as discussed in
Section 2, tricks the browsers to download executable files which can then infect the whole system. Malvertising uses JavaScript for execution of the malicious code, so disabling it would prove beneficial in preventing Ransomware attacks. The disablement restricts scripting attacks that can lead to open redirects to Ransomware distribution websites.
3.2.4. Controlled Folder Access
This technique works best for organizational environments that deploy Windows based devices for work purposes. It enables the trusted applications to access the designated folders. Designated folders are mapped to different applications when Controlled Folder Access is configured initially. This technique works with a database of trusted applications maintained from time to time. If an application or an executable is not present in the trusted application database, it is barred from modifying the contents of the designated controlled folders. Controlled Folder Access is an excellent avoidance measure as it can protect boot sectors as well which are targeted by the latest Ransomware families. Controlled Folder Access also utilizes an audit mode that can further create a honeypot for the executables that are not present in the trusted application database trying to access protected folders.
As seen above, the Ransomware avoidance techniques are fairly generic in nature and Cyber-hygiene is the best policy to be followed, especially for individual users.
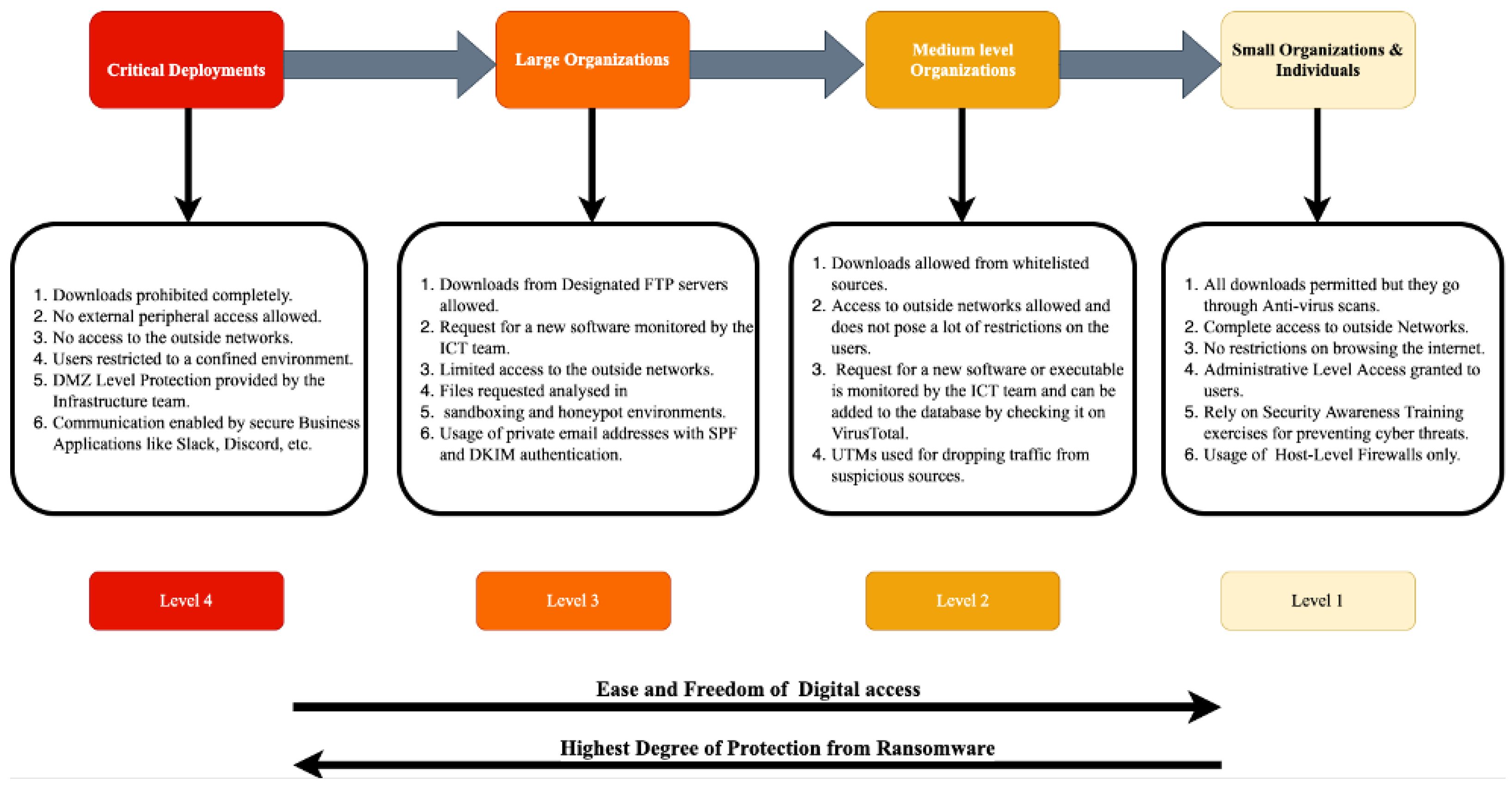
Figure 3 depicts a Ransomware avoidance continuum for different organization types.
Figure 3. The Ransomware avoidance continuum.
The Level 4 Ransomware Prevention applies to critical infrastructures and restricts their users to a confined or sand-boxed environment. This does not grant the digital freedom to the users but works extremely well in avoiding incidents of Ransomware attacks. Level 3 applies to large organizations. Here users download files (typical open-source software packages) from designated File Transfer Protocol (FTP) servers which are maintained by central Information Technology (IT) teams. All other downloads requested from the open internet first are stored in a sandbox and analyzed both statically and dynamically for detection of malware. Further, software updates can be controlled and distributed by the central IT team and individual users do not have root privileges to make system-level changes. Level 2 applies to mid-sized entities allows users to download files from the open internet but route the traffic through a Unified Threat Management (UTM) device for detecting malware and dropping traffic from suspicious sources. Level 1 applies to small organizations which do not have the necessary IT infrastructure or security policies in place
[61][38]. Here apart from having individual anti-virus software, there is not much by way of security policies. These organizations are the most susceptible to Ransomware attacks and user education and awareness are the most effective strategies for avoiding Ransomware attacks.
Thus, Ransomware avoidance is typically a trade-off between the freedom of digital access and fool-proof security. The more the desired degree of freedom to end users in downloading and installing third-part software applications, the more difficult and complex the task of Ransomware avoidance becomes.
3.3. Ransomware Mitigation Techniques
Ever since the advent of Ransomware, cyber-defenders have been trying to come up with advanced security solutions that would counteract different Ransomware strands. On the other hand, Ransomware designers have exploited new vulnerabilities, preying on lack of cyber-security awareness of a vast majority of the population to wreak havoc. Mitigation of Ransomware attacks involve recovering encrypted data most likely through reverse engineering or not allowing the Ransomware to complete the encryption process. However, in the real-world mitigation techniques have had limited success. A vast majority of individual victims of Ransomware typically end up paying the ransom demand or losing their data permanently. Still several mitigation techniques that can enable removal of Ransomware and recovery of devices in an efficient manner have been proposed.
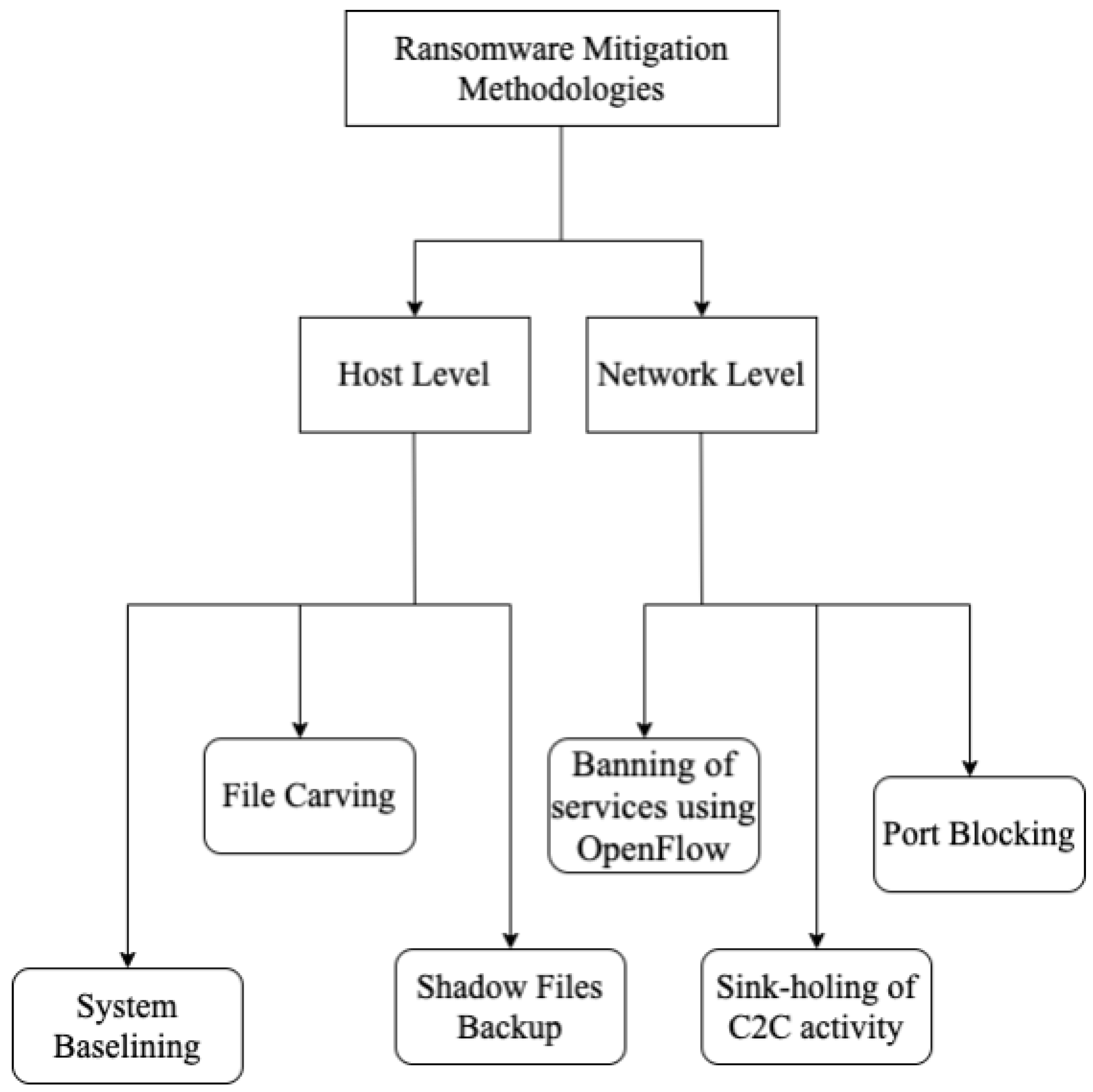
Figure 4 sums up the main mitigation methodologies based on the techniques they use.
Figure 4. Typical Ransomware mitigation methodologies.
Cabaj et al.
[62][39] devised a mitigation technique that made use of Software defined networking to counteract Ransomware. This method was applied to CryptoWall Ransomware, but was applicable to almost all types of Crypto Ransomware. The technique used dynamic blacklisting of C&C servers when the sample was being run. Without the C&C server, infected machine cannot access the public key that will be used to encrypt it. This technique however could not identify any servers that have not been used previously as C&C servers. The blacklisting technique worked with a list of available proxy servers. The implementation of such a mitigation system was made possible through two SDN based applications, SDN1 and SDN2. SDN1 evaluated DNS responses from the inbound traffic and checked if the domain was already present in the database of illicit proxies. SDN2 enhanced the functionality of SDN1 by reconfiguring the whole network infrastructure to block the Ransomware activity. SDN2 utilized OpenFlow protocol to block the traffic associated with a malicious sample.
Zimba et al.
[63][40] made use of reverse engineering to uncover the actual operation followed by different strands of Ransomware. The authors stated that option for data recovery exists inside the attack structure and the underlying code of the Ransomware, despite how complex the Ransomware looks. The approach followed by them comprised of two modules. The first module used reverse engineering to find out the functions for data deletion and recovery in the source code of the malware. Through the first module, the authors were able to identify various properties of a Ransomware by deploying various scans like Virus scans, obfuscation checks, meta-data extraction etc. The second module used sandboxing for analyzing the behavior of the Ransomware. This module comprised a server-side environment and client-side environment. In the server-side environment, Cuckoo server
[64][41] and Volatility were being run. Cuckoo was responsible for delivering the Ransomware. In the client-side environment, there were various Virtual Machines running Windows 7 Desktop Edition. Through Volatility, Ransomware was being analyzed dynamically. Various behavioral features of the sample were collected through the second module. The authors then proceeded to discuss the file hiding techniques used by the attackers. They found out that the attackers don’t use secure file deletion techniques which make file recovery impossible
[65][42]. Through their experiment, they were able to recover data because of the weak deletion methodologies used by the Ransomware. In the samples analyzed by the authors, almost all of the samples deleted the volume shadow copies; but due to timely offline backup of those copies led them to restore the victim’s device.
Sophos developed an endpoint mitigation tool called Intercept X that claims to eliminate Zero-day APT families. Intercept X uses behavioral analysis to prevent Ransomware families from modifying registries. According to Endpoint Security’s Testing Guide
[68][43], Intercept X has a success rate of 99.7% in detection and mitigation with just one false alarm in the real world test. Intercept X also deploys exploit prevention techniques that help in finding out extremely advanced adversary shell-coding patterns and blocking them before they are able to gain access into the registry. Along with these features, Intercept X brings a new feature called Crypto Guard that can recover encrypted files. Despite the extremely high efficiency, further research needs to be conducted into how and whether it can detect and mitigate the latest families that deploy anti analysis techniques.
Microsoft released two products called Defender for Endpoint and Defender for Identity for extensive protection against Ransomware attacks. They have been thoroughly tested against the largest malware database in the world, AV-TEST. Both of them scored 100% protection level in the October 2020 test. This test included new 12316 malware samples along with 339 Zero Day strands. However, the rate of introduction of new strains of Ransomware makes it virtually impossible to build fool-proof solutions. McAfee LLC
[69][44] patented a framework that was able to identify if any unauthorized executable was trying to modify the local files on the system and create a security event for the same. The framework used entropy values to distinguish between files and their modified form. Any value above the threshold would denote a security breach and thus, the framework would create a security event accordingly. The security event would then be monitored and if the entropy value was way too high, then the system would be taken back to the last snapshot in order to mitigate the Ransomware attack. System baselining, checkpointing and rollbacks require significant storage requirements.
Dell EMC
[70][45] invented a framework that replicated all the appends and writes from a server to two different copies, a local and a remote. The local copy resided in a local production site whereas the remote copy was kept in a remote disaster recovery site. A sliding time window was used to measure the deduplication ratio in an arbitrary chosen length of data. If this ratio was on the increasing end of the threshold, the framework claimed to have detected a Ransomware. In order to mitigate the attack, the framework would stop any pending appends and writes designated for the remote site. While such schemes work well for data files, retrieving licensed applications and ensuring complete system recovery has not been attempted by existing mitigation techniques and mechanisms.
While some mitigation strategies have proved effective against existing strains of Ransomware, their effectiveness has been demonstrated in a controlled lab environment. In real-world scenarios Ransomware spreads because of unpredictable human responses and actions and a divergence of security policies, devices and deployments across vendors. This is due to the lack of standardization efforts in devising security mechanisms and large-scale collaborative efforts involving governments, security organizations and researchers.