Smart grids involves multiple stakeholders that includes consumers, electric utilities, grid operators, and third-party service providers. Due to involvement of multiple stakeholders, the management of the smart grid data specially from the smart meters becomes a daunting task. For enhanced security and privacy protection of smart meter,proposed framework that provide guidelines for integrating security and privacy across different domain.
- smart grid
- cyber attacks
- DDoS attack
- authentication
- authorisation
- packet flooding
- denial of service
1. Introduction
The conventional electricity system has been enhanced with modern technology, transforming it into a smart grid. A smart grid incorporates several operational and energy management techniques. The operational and energy measures may include smart meters and smart appliances installed at the customer’s location, a production meter, renewable energy generators, smart inverters, and energy efficiency resources deployed at the grid’s location [1]. Renewable energy generators contribute to energy cost reductions since the cost of producing electricity from renewable sources is zero, although renewable energy is intermittent in nature and is highly influenced by a variety of conditions such as ambient temperature, humidity, wind speed and direction, and geographical area. Solar energy, for example, is affected by irradiance, cloud cover, and ambient temperature [2]. Wind energy fluctuates greatly with wind speed and direction. Numerous techniques exist for forecasting wind energy, solar energy, and battery state of charge in order to incorporate renewable energy in a robust and timely way. The smart grid enables bidirectional communication between the grid and the sensors installed in various locations. These sensors continuously transmit production data to the grid in the form of data packets. This information covers the creation, consumption, voltage, and frequency of energy, as well as other energy-related data. Currently, battery-integrated grids send the state of charge over charge through a communication channel that exposes the battery management system (BMS) to cyber threats. These cyber threats can lead battery to overcharge or undercharge, which may lead to catastrophic events.
There are numerous benefits of the smart grid over traditional grids such as improved power quality, self-healing, cost effectiveness with the integration of renewable energy, adaptive energy generation, more environmentally friendly operation, aggregation of distributed energy resources (DERs), real-time energy consumption monitoring at customer’s end, integration of AI models to automate tasks, remote energy motoring, rapid response to faults, remote fault location identification, and automated maintenance. These benefits make the smart grid more attractive than the traditional grid. The two main challenges that arise are cybersecurity and complexity. These issues become more challenging when the smart grid data is hosted on the cloud [3][4][3,4]. Apart from physical security, cybersecurity becomes a key element of the smart grid to keep it secure and stable all the time. Cyber protection is not only required for the smart grid but [5] shows even traditional and nonsmart grids are also exposed to cyberattacks. This study performed in [5] presents the impact on the grid when a malicious software(botnet) controls the overall power consumption including CPU, GPU, hard disks, screen brightness, and laser printers of computers. The simulation performed showed that 2.5 to 9.8 million infections can destabilize the grid. In another research [6], high wattage IoT devices can cause frequency instability, line failure, and increase in operating cost when the attacker the access to the IoT botnet of the high wattage smart appliances. These types of attacks have potential to cause major blackout by manipulating the energy demand.
As the complexity of the grid increases, the chances of faults also increase. For example, there are thousands of sensors installed and one of the sensors starts transmitting faulty data despite being no fault in the production devices; this can destabilize the whole functionality of the grid system. The second challenge is security—specifically, the communication between devices and the grid. The complexity of the communication channels of the smart may lead to problems in securing the smart grid data and cyberattack can lead to physical damage to the smart grid. The key contribution of this paper are (1) analysis of the communication network of the smart grid. The communication network is the backbone of smart grid, and it is the communication network that makes the grid a smart grid. (2) We performed an in-depth review of current vulnerabilities in the present smart grid and their mitigation techniques. (3) Any cyberattack targets either the communication network or employees working to manage the communication network or the customers using the network. We present techniques that can minimize the the chances of any cyberattack at any level.
The rest of the paper is organized as follows. In Section 2 , we discuss the communication architecture of the smart grid followed by Section 3 , which shows the various vulnerabilities in smart grid. In Section 4 , the primary goals of cybersecurity in smart grid are discussed. In Section 5 , we present a brief history of cyberattacks and blackouts around the world. In Section 6 , we discuss the existing solutions to the cybersecurity problem of smart grid. In Section 7 , open issues, challenges, and solutions are discussed, followed by the conclusion in Section 8 .
2. Communication Architecture of Smart Grid
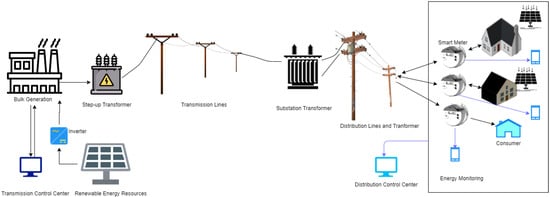
The components of the smart grid are depicted in Figure 1 . A communication network connects the three domains: service provider, grid, and customer. This communication occurs across a variety of different protocols and channels. The grid domain encompasses large-scale energy generation, distribution, and transmission. The smart meter connects concurrently with the consumer domain and the communication network and this combined network is known as Advanced Metering Infrastructure(AMI) network. Smart meters are assigned to send data of consumption of use, outages, and electricity prices [7]. It communicates with the consumer domain using a short-range protocol such as Zigbee, and with the customer domain via GSM, Wi-Fi, and so on. While the smart grid enables more efficient energy distribution than the traditional centralized system, it is subject to security attacks at many tiers [8][9][10][11][12][13][8,9,10,11,12,13].
3. Vulnerabilities in the Smart Grid
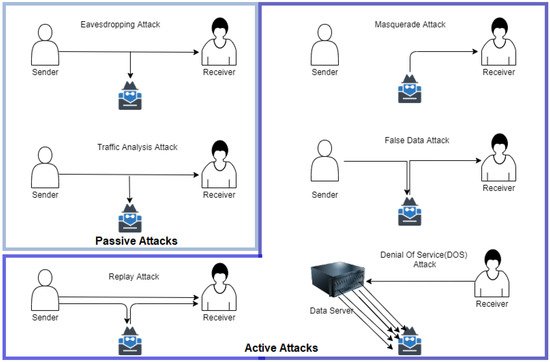
The vulnerability of a smart grid network is the weak spot at which an attacker may enter the network and attack the system as shown in Figure 2 . The smart grid connects with multiple domains using different protocols, making it vulnerable to numerous cyberattacks. In this section, we explore the conditions that might increase the vulnerability of the grid to cyber intrusion. However, first, we discuss the types of cyberattacks. There are mainly two kinds of attacks: (1) passive attacks and (2) active attacks. Passive attacks are those in which no harm to the data is done, but the attacker only monitors the data, whereas the active attacks are more dangerous compared to active attacks, as the attacker modifies the data or stops the receiver from receiving the data.
The passive attacks are classified into two categories: (1) eavesdropping attack and (2) traffic analysis attacks. The types of active attacks includes masquerade attacks, replay attack, false data attack, and denial of service attacks.
Figure 23 shows different types of cyberattacks. The eavesdropping attacks is when the attacker can see the data packets shared between sender and the receiver. However, the attacker does not modifies the data. Traffic analysis attack is another kind of passive attack in which the attacks continuously monitors and analyzes the traffic between the sender and the receiver. Active attacks are more harmful than the passive attacks, as the attacker has full control over the data. The replay attack is when the attacker and sender both send the data to the receiver; this confuses the receiver in differentiating between real data by sender and the data routed through the attacker. In the masquerade attack, the sender is idle, but the receiver keeps receiving data from the attacker. The false data injection attack in when the data do not come to the receiver directly from the sender instead the receiver receives the modified data from the attacker. However, both the sender and the receiver are unaware about the modification done by the attacker. Denial of service attack is a kind of attack in which attacker does not target the sender or receiver but the data server. The attacker generates a bulk amount of irrelevant requests from the server and the server starts serving those irrelevant requests until all of its resources are exhausted. The receiver/sender requests information from the server, and due to unavailability of resources, the request from the sender/receiver is denied. The major causes that make the smart grid vulnerable to cyberattacks are as follows: Increased installation of intelligent electronic devices (IEDs): As the number of devices in the network rises, the number of attack sites for attackers increases as well. Even if the security of a single point is compromised, the entire network system would be impacted. Installation of third-party components: Third-party components that are not advised by experts increase the network’s vulnerability to cyberattack. These devices may be infected with trojans, which can then infect other devices on the network. Inadequate personnel training: Proper training is necessary to operate any technology. When staff are not sufficiently taught, they might easily fall victim to phishing attempts. Using Internet protocols: Not all protocols are secure when it comes to data transmission. Certain protocols transfer data in an unencrypted format. As a result, they are easy candidates for data extraction via man in the middle attacks. Maintenance: While the primary goal of maintenance is to keep things functioning properly, it can become a vector for cyberattacks at times. While doing maintenance, operators often disable the security system to conduct testing. In 2015, electric power companies in eastern Europe reported one similar occurrence [14].
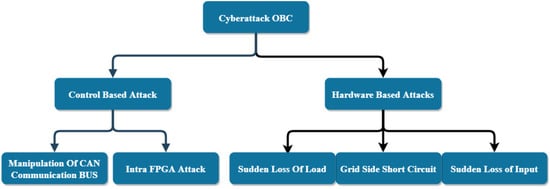
The integration of electric vehicle charging system (EVCS) makes the power system/grid more complex. Over the past several years, the sales of electric vehicles have increased exponentially, mainly due to economic and environmental factors. With incorporation of newer technologies, the cost of EVs and EV batteries has seen a drastic decrease in addition to government incentives. Moreover, EVs do not rely on fossil fuel consumption so they are contributing in minimizing carbon footprints [15]. However, EVCSs are not cyberattack-resistant as they depend on the wired and wireless communication systems to share information with the smart grid. The study in [16] categorized EVCS vulnerabilities into two broad categories, i.e., internal vulnerability and external vulnerability. Internal vulnerability such as EVCS processor with weak password and hashing algorithm, weak access control, unsigned firmware update, and easy extraction of firmware can lead to attacker to get full control of EVCS. External vulnerabilities such as on-site human machine interface (HMI) that allow users to connect universal serial bus (USB) drives can be easily used by attackers to expose the EVCS configuration. Since there is no worldwide standard for communication systems between EVCSs and EVCS server, the open charge point protocol (OCPP) has been adopted by many vendors. However, OCPP is vulnerable to man-in-the-middle attack (MIMA) [16]. In addition to this, many smartphone and web-based applications that assist users in finding EVCSs nearby, authenticating EVs at EVCS, and remotely controlling the charging and payment for the charge have been developed. Due to this, any malicious application or cloned application can potentially damage the EVCS. In [17], the authors performed a study on cybersecurity challenges in the onboard charging (OBS) system of an EV. The electric component units (ECUs) are connected in a controller area network (CAN) to communicate between them. Cyberattacks on OBC system are classified into two categories: (1) control-based attacks and (2) hardware-based attacks. Figure 34 shows attacks included in both categories. The sales of EV are highly correlated with installation of EVCSs such that the EV penetration will go up, there will be a spike in EV charging stations, and there will be a significant impact on energy demand [18]. In this study, the communication requirement and standards for the Internet of electric vehicles are presented. In another research study, authors developed a framework for analysis, comparison, and test of standards (FACTS), proposed in [19], to identify cyberthreats in a battery management system (BMS).
4. Primary Goals of the Cybersecurity in the Smart Grid
The National Institute of Standards and Technology (NIST) developed a framework for enhancing smart grid cybersecurity. They categorized logical interface categories in 22 different categories. Table 1 summarizes their definition along with example and their impact on confidentiality, integrity, and availability. Furthermore, the NIST suggests 19 smart grid requirements, which are as follows: Awareness Training (SG.AT) Access Control (SG.AC) Audit and Accountability (SG.AU) Security Assessment and Authorization (SG.CA) Configuration Management (SG.CM) Continuity of Operations (SG.CP) Identification and Authentication (SG.IA) Information and Document Management (SG.ID) Incident Response (SG.IR) Smart Grid Information System Development and Maintenance (SG.MA) Media Protection (SG.MP) Physical and Environmental Security (SG.PE) Planning (SG.PL) Security Program Management (SG.PM) Personnel Security (SG.PS) Risk Management and Assessment (SG.RA) Smart Grid Information System and Services Acquisition (SG.SA) Smart Grid Information System and Communication Protection (SG.SC) Smart Grid Information System and Information Integrity (SG.SI)
| Risks | |||||
|---|---|---|---|---|---|
| Logical Interface Category | Definition | Example | Confidentiality | Integrity | Availability |
| 1 | Interface between control systems and equipment with high availability, and with compute and/or bandwidth constraints, | Between transmission SCADA and substation equipment | Low | High | High |
| 2 | Interface between control systems and equipment without high availability but with compute and/or bandwidth constraints | Between distribution SCADA and lower priority pole-top equipment | Low | High | Medium |
| 3 | interface between control systems and equipment with high availability, without compute or bandwidth constraints, | Between transmission SCADA and substation automation systems | Low | High | High |
| 4 | Interface between control systems and equipment without high availability, without compute or bandwidth constraints, | Between distribution SCADA and backbone network-connected collector nodes for distribution pole-top IEDs | Low | High | Medium |
| 5 | Interface between control systems within the same organization, | Multiple DMS systems belonging to the same utility | Low | High | High |
| 6 | Interface between control systems in different organizations | Between an RTO/ISO EMS and a utility energy management system | Low | High | Medium |
| 7 | Interface between back office systems under common management authority | Between a customer information system and a meter data management system | High | Medium | Low |
| 8 | Interface between back office systems not under common management authority, | Between a third-party billing system and a utility meter data management system | High | Medium | Low |
| 9 | Interface with B2B connections between systems usually involving financial or market transactions, | Between a retail aggregator and an energy clearinghouse | Low | Medium | Medium |
| 10 | Interface between control systems and noncontrol/corporate systems, | Between a work management system and a geographic information system | Low | High | Medium |
| 11 | Interface between sensors and sensor networks for measuring environmental parameters, usually simple sensor devices with possibly analog measurements, | Between a temperature sensor on a transformer and its receiver | Low | Medium | Medium |
| 12 | interface between sensor networks and control systems | Between a sensor receiver and the substation master | Low | Medium | Medium |
| 13 | Interface between systems that use the AMI network, | Between MDMS and meters Between LMS/DRMS and Customer EMS | High | High | Low |
| 14 | Interface between systems that use the AMI network with high availability, | Between MDMS and meters Between LMS/DRMS and customer EMS Between DMS applications and customer DER | High | High | High |
| 15 | Interface between systems that use customer (residential, commercial, and industrial) site networks such as HANS and BANs | Between customer EMS and customer appliances Between customer EMS and customer DER | Low | Medium | Medium |
| 16 | Interface between external systems and the customer site | Between third-party and HAN gateway Between customer and CIS Web site | Low | Medium | Low |
| 17 | Interface between systems and mobile field crew laptops/equipment | Between field crews and GIS Between field crews and substation equipment | Low | High | Medium |
| 18 | Interface between metering equipment, | Between submeter to meter Between PEV meter and energy service provider | Low | High | Low |
| 19 | Interface between operations decision support systems | Between WAMS and ISO/RTO | Low | High | Medium |
| 20 | Interface between engineering/maintenance systems and control equipment | Between engineering and substation relaying equipment for relay settings | Low | High | Medium |
| 21 | Interface between control systems and their vendors for standard maintenance and service | Between SCADA system and its vendor | Low | High | Low |
| 22 | Interface between security/network/system management consoles and all networks and systems | Between a security console and network routers, firewalls, computer systems, and network nodes | High | High | High |
Security requirement identifier, category, requirement, supplemental guidance, requirement enhancement, additional consideration, and impact level allocation should be added with each security requirement. Security requirement in depth can be presented in [20].
There are five [20]main goals of cybersecurity in smart grids that are described below. Table 2 provides the summary of attack category and security goal they compromise.
Security goals compromised under attack category.
