The development of a dynamic consent medical blockchain system called DynamiChain, based on a ruleset management algorithm for handling health examination data.
- blockchain
- security management
- dynamic consent
1. Introduction
As part of the fourth industrial revolution in recent years, the advancement in blockchain technology has brought back the original theorem regarding smart contracts. Such algorithms based on computer protocols were designed to automatically facilitate, verify, and enforce the negotiation and implementation of digital contracts within an authority distributed architecture [1,2,3][1][2][3]. Smart contracts are being applied to a wide range of fields, mainly from the digital economy to healthcare, and the Internet of Things (IoT) [4]. To date, there is still a trend to use mainstream blockchain platforms, such as Bitcoin and Ethereum, when developing such platforms [5,6][5][6].
However, smart contract-related core technology is still in its infancy, and major technical challenges regarding security breach and privacy issues still exist. For example, blockchain cannot guarantee transactional privacy, since the values of all transactions and balances for each public key are publicly visible [7,8][7][8]. Moreover, a user’s Bitcoin transactions can be linked to reveal user’s information [9]. Similarly, each client can be uniquely identified by a set of nodes it connects [10]. “DAO Attack” that occurred in June 2016 [11,12,13][11][12][13] might be one of the most well-known blockchain targeted attacks. It was a severe incident that resulted in a loss amounting to more than $50 million Ether (approximately worth more than 8.5 billion dollars at that time) being transferred to an unauthorized account. This type of security breach is particularly sensitive in the medical industry, where personal health or medical information is being transferred within the network. In addition, contemporary blockchain-converged solutions do not consider restricted medical data regulations that are still obstacles in many countries worldwide.
In addition, current medical systems lack evidence-based data sharing policy, making it difficult for data providers to control their data based on their desired settings or policies. Some of the core values that blockchain technology aims to achieve, which are distributed authority, and consensus-based security, could play a vital role in providing these data providers with the rights they have over their own health data. This implies a crucial need for a system or solution that is suitable for the healthcare sector.
2. Proposed System
2.1. Overall System Architecture
The overall system architecture of DynamiChain is shown in
. As mentioned previously, the proposed medical blockchain network was specialized to handle health examination big data, which consists of Inbody [14] tested, blood test, and functional test datasets.
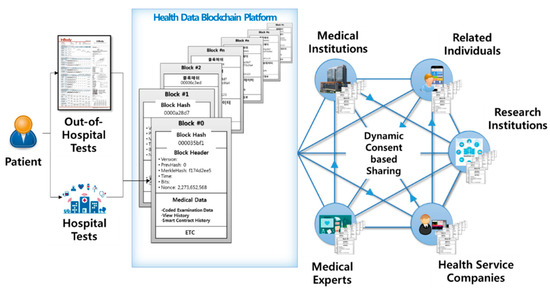
Participants include various parties, such as data providers (e.g., patents, holders of health examination data) and data utilizers (e.g., medical professionals, medical institutions, insurance companies, research institutions, and health service companies). Data providers, which are the main party of this network, have established a dynamic consent rule in three main parts: Consent level, approval duration, and approval target. Data utilizers can only participate under dynamic conditions set by the data providers in charge of their own medical data. Data utilizers use this hyperledger-based network under a dynamically set consent.
2.2. Specific System Functions
The functions that comprise the overall system mentioned in the previous section are explained in this Section. The list of the function contents is shown in
.
| Function Classification | Function Contents |
|---|
| Data Provider’s App | Basic account functions (log in, create account, etc.) My examination history ledger My examination data (raw data and statistical data) Dynamic consent rule settings |
| Data Utilizer’s App | Basic account functions Input health examination results data function Data provider list management Data providers’ examination history management ledger Data providers’ examination data sharing usage history management ledger Request for data provider data function Data provider data request management function (applicable and non-applicable) |
| Blockchain System | Health examination data hash storage function Sync smart contract with real-time dynamic consent function settings Smart contract and blockchain ledger |
| Blockchain Admin Web | Channel management Peer node management User account management Blockchain data sharing history ledger management |
Through the data provider’s app, data providers may not only view their own health data, but also change dynamic consent rule settings. They have full access to the ledger, which includes the history of which data utilizer viewed or used their data.
By using the data utilizer’s app, any data utilizers may access data providers’ health examination data based on set rules. They may also act as a “mining node” (mining, in terms of blockchain), to be rewarded for checking if the transmitted data are real. Since hospitals are the main provider for the hospital examination data provider data, numerous data management functions can be enforced with this app. Even if the requested data meet the settings set by the data provider, the hospital finally confirms whether or not the transaction should be made. This function may be disabled in countries that do not have restricted medical data policies.
The hash function of the blockchain system is created and matched to each health data. In addition, this function is automatically synced with real-time changing consent settings by each data provider. Most importantly, all transaction history is stored for data integrity and security in each blockchain. Finally, the blockchain admin web functions enable the super administrator to monitor the status of the entire channel, participating peer nodes, and participating users (i.e., data provider and data utilizer) within the blockchain network.
2.3. Dynamic Consent Algorithm
Medical data is an intangible asset that requires time and effort from a medical institution or individual. It is intertwined with users, service providers, data carriers, etc., requiring a consent system algorithm that all participants can intuitively understand and agree on. To meet these needs, this paper applied the dynamic consent concept on a new customized consent system, called “dynamic consent algorithm”. The system is tailored to the individual user’s taste, minimizing the user’s resistance to data disclosure. Furthermore, by implementing this dynamic consent algorithm in the chaincode, this entry developed a consent system algorithm that is transparent and integrated to all participants in the consensus operation of the blockchain. Our proposed dynamic consent algorithm includes data type, approval duration, and objectives (
).
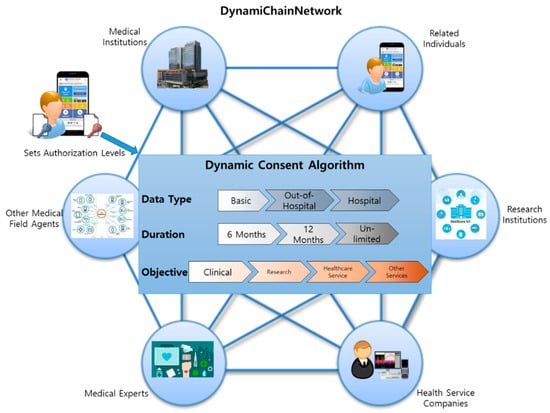
The term data type refers to data providers setting the type of data they wish to provide to other data utilizers. Data providers can choose from three data types: Data derived basically, out-of-hospital-level tests, and data derived from hospital-level tests. For example, basic data refer to social demographic data, such as age, sex, and address. Out-of-hospital tests refer to basic health tests that data providers can easily achieve through home healthcare devices, such as thermometers, InBody tests, or other healthcare-related devices. On the other hand, data obtained from hospital-level tests are more in-depth because data providers can only achieve such data when they visit the hospital. The specific contents of these three classifications are shown in
.
| Classification | Contents |
|---|
| Basic | Serial number, Sex, Age, Smoking Status, Drinking Status, Height, Weight, Waist |
| Out-of-hospital-level tests | Body Water, Protein, Minerals, Body Fat Amount, Weight, Bones and Muscle Amount, BMI, Body Fat Ratio, InBody Score, Abdomen Fat Ratio, Internal Organ Fat Level, Fat-free Mass, Basal Metabolism, Obesity Index, Recommended Calorie Amount, Body Parts’ Muscle Analysis (Right Arm, Left Arm, Body, Right Leg, Left Leg), Body Parts’ Fat Analysis (Right Arm, Left Arm, Body, Right Leg, Left Leg), Body Parts’ Body Water Analysis (Right Arm, Left Arm, Body, Right Leg, Left Leg), Body Parts’ Cell Water Analysis (Right Arm, Left Arm, Body, Right Leg, Left Leg), Body Parts’ Cell-free Water Analysis (Right Arm, Left Arm, Body, Right Leg, Left Leg), Cell-free Water Ratio, Phase Angle |
| Hospital-level tests | Cholesterol, Triglycerides, HDL Cholesterol, LDL Cholesterol, Diastatic Hemoglobin, Diastatic Hemoglobin Before Meal, Protein in Urine, Serum Creatinine, AST, ALT, Gamma GTP, Serial Number, Examination Date, Examined Institution, Sight (Left, Right), Blood Pressure (Systolic, Diastolic) |
Approval duration refers to data providers setting the exposure duration of their personal medical data to other data utilizers. By default, data providers can simply select 6 months, 12 months, or unlimited duration. This can always be changed by accessing the system settings.
The third objective refers to data providers selecting which data utilizer they desire to provide their personal medical data according to the usage objective. With this function, data providers can, by default, select any group based on these four classifications: Clinical, research, healthcare service, and other services. Any data utilizers (mainly hospitals) that registered into our proposed system with the objective of using physical examination data for clinical matters are classified as “Clinical.” Similarly, all groups (mainly universities or research institutions) whose data usage objective is for research are classified as “Research.” Most health insurance companies are classified as “Healthcare services,” and other data utilizers with other needs are classified as “Other services.”
2.4. Restricted Medical Data Policy Applied Work Flow Specifications
Some countries worldwide, including South Korea, still prohibit healthcare data to be stored outside certified medical institutions. Considering this, the proposed system only saves hash values of the health examination data and stores actual medical data separately in another database. Medical data’s multiple hash values are stored in the blockchain ledger so that data utilizers could read the data providers’ data based on set rules. Encoding–decoding access key to the actual medical data is, by default, managed by the data provider, unless the data provider delegates his or her authority to medical institutions where the actual database is stored. Using this mechanism, we balanced the data co-ownership ecosystem while preserving data integrity in a practical situation. This service process is shown in Figure 3. The hospital generates health an examination data of a data provider than the hash management system encrypts the data with the data provider’s public key and stores them with the hash value of the data. The data provider then confirms the data itself and dynamic consent rule in real-time and modifies the setting of the rules if necessary. The data utilizer requests for the data of the data provider, and the hospital confirms the request. The hospital allows access to actual data transmission after the endorsement process. Finally, data utilizer read the requested data through hash value comparison.
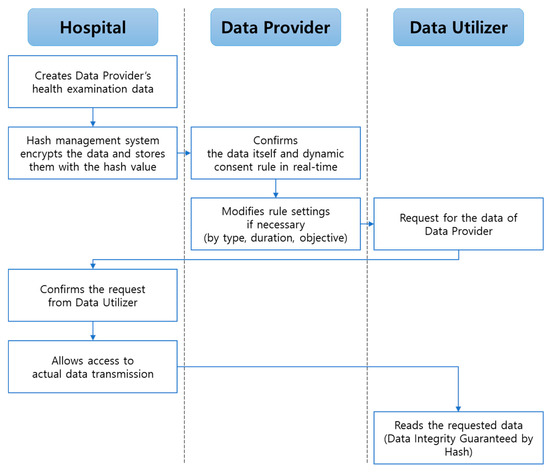
Proposed specific blockchain service process.
Hospital type data are created when data providers visit the hospital for a health examination. For each data, our proposed system stores encoded data, and accordingly, it has the data provider public key. Data providers have access to their own physical data and can set or change their dynamic consent rule in real-time. When other data utilizers (e.g., companies and research institutions) request for the allowed data providers’ medical data, the data source hospital confirms this request before transmitting the actual medical data to the requested data utilizer. Thereafter, the data utilizers could read the requested data. This is the key process that not only overcomes the issue of restricted health data sharing policies for some countries, but also guarantees data integrity. Note that out-hospital-data types are free from this scenario.
References
- Wu, S.; Chen, Y.; Wang, Q.; Li, M.; Wang, C.; Luo, X. CReam: A smart contract enabled collusion-resistant e-auction. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1687–1701.
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F.-Y. Blockchain-enabled smart contracts: Architecture, applications, and future trends. IEEE Trans. Syst. Man Cybern. 2019, 49, 2266–2277.
- Gao, F. Data encryption algorithm for e-commerce platform based on blockchain technology. Discret. Contin. Dyn. Syst. S 2019, 12, 1457–1470.
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303.
- Zheng, X.; Sun, S.; Mukkamala, R.R.; Vatrapu, R.; Ordieres-Mere, J. Accelerating health data sharing: A solution based on the Internet of Things and distributed ledger technologies. J. Med. Internet Res. 2019, 21, e13583.
- Khan, F.A.; Asif, M.; Ahmad, A.; Alharbi, M.; Aljuaid, H. Blockchain technology, improvement suggestions, security challenges on smart grid and its application in healthcare for sustainable development. Sustain. Cities Soc. 2020, 55, 102018.
- Meiklejohn, S.; Pomarole, M.; Jordan, G.; Levchenko, K.; McCoy, D.; Voelker, G.M.; Savage, S. A fistful of bitcoins: Characterizing payments among men with no names. In Proceedings of the 2013 Conference on Internet Measurement Conference, Barcelona, Spain, 23–25 October 2013; pp. 127–140.
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858.
- Biryukov, A.; Khovratovich, D.; Pustogarov, I. Deanonymisation of clients in Bitcoin P2P network. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 15–29.
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564.
- Mehar, M.I.; Shier, C.L.; Giambattista, A.; Gong, E.; Fletcher, G.; Sanayhie, R.; Kim, H.M.; Laskowski, M. Understanding a revolutionary and flawed grand experiment in blockchain: The DAO attack. J. Cases Inf. Technol. 2019, 21, 19–32.
- Ghaleb, B.; Al-Dubai, A.; Ekonomou, E.; Qasem, M.; Romdhani, I.; Mackenzie, L. Addressing the DAO insider attack in RPL’s Internet of Things networks. IEEE Commun. Lett. 2019, 23, 68–71.
- Wadhaj, I.; Ghaleb, B.; Thomson, C.; Al-Dubai, A.; Buchanan, W.J. Mitigation mechanisms against the DAO attack on the routing protocol for low power and lossy networks (RPL). IEEE Access 2020, 8, 43665–43675.
- Bailey, B.W.; LeCheminant, G.; Hope, T.; Bell, M.; Tucker, L.A. A comparison of the agreement, internal consistency, and 2-day test stability of the InBody 720, GE iDXA, and BOD POD (R) gold standard for assessing body composition. Meas. Phys. Educ. Exerc. Sci. 2018, 22, 231–238.
