Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Amandeep kaur and Version 2 by Camila Xu.
Zero Trust Architecture research is now in its early stages, with a primary focus on the framework itself, access control, algorithms of trust evaluation, and identity authentication. These are the primary study domains within the Zero Trust field.
- authentication
- zero trust (ZT)
- cloud computing
- network security
- blockchain
1. Introduction
The issue of information security has become increasingly difficult as information technology has continued to advance and find practical applications since the inception of the digital age. The prevalence and intensity of attacks related to cyber-security on networks has risen significantly in recent years. Even medium-sized business data centres can experience more than 100,000 security attacks each day. These attacks can be carried out by a variety of opponents, from solitary hackers to organized cyber-gangs. Their goals may include compromising essential network resources that include software-defined networks or Domain Name Servers, potentially jeopardizing their integrity and functionality [1]. As telecommuting and digital transformation gain traction, traditional company boundaries have diminished, removing digital boundaries entirely. As a result, the growing need for remote access has outpaced the capabilities offered by conventional perimeter safety measures. As a result of this trend, various businesses have been forced to reconsider their approach to network security. As a result, a concept known as Zero Trust Architecture has arisen, concentrating on resource security rather than just on perimeters of network. The security posture of a resource is no longer primarily governed by its network location under this approach [2].
Zero Trust Architecture research is now in its early stages, with a primary focus on the framework itself, access control, algorithms of trust evaluation, and identity authentication. These are the primary study domains within the Zero Trust field. Hence, the goal of this research is to provide a complete overview of the current research state in Zero Trust Architecture development, with a focus on four major topics. It covers the primary obstacles encountered in each discipline and investigates potential pathways for future study to successfully address these issues. Figure 1 depicts the work flow of the research article emphasising the interconnections and relationships among different aspects of the conducted analysis.
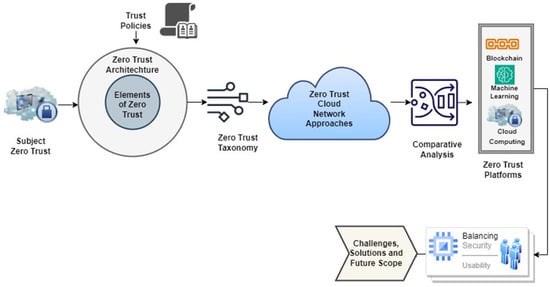
Figure 1.
Workflow of study conducted.
2. Relevant Approaches of Zero Trust Network Model
Sultana et al. [3][15] presented a safe medical image allocation platform based on ZT concepts and technology of blockchain. This technology provides the complete security of sensitive medical data. The technology improves information security by utilizing blockchain. However, it is critical to examine the possible complexity and efficiency consequences of combining these technologies, and additional research is needed in this field. Ian and Song [4][16] suggested a ZT strategy based on the BIBA and BLP models. This method does thorough trust assessments for numerous system components. It emphasizes the importance of confidentiality and integrity and assigns different weights to achieve greater security. It does not, however, address the initial trust value assignment for entities such as users, terminals, environments, and objects, which could lead to human errors. Furthermore, the completeness and logic of the weight assignment list need to be investigated further. Dayna et al. suggested a ZT model specifically intended for cloud data centre networks in a separate study [5][17] for the creation of trust; their model blends identity management, packet-based authentication, and automated threat response. It controls the model’s eight different network trust levels dynamically.
Traditional network security measures that focus on basics a border between trustworthy and local networks are no longer viable, as cloud apps and IoT networks have become more commonly used. ZT architecture has emerged to meet the need for secure and intelligent access management in the absence of trusted networks or devices. To fulfil the particular security requirements of respective networks, researchers devised and implemented numerous variants of ZTA. Pedro Assuncao proposed a ZT architecture in [6][18] that eliminates unchanged credentials, uses multifaceted verification, and keeps a proper record of devices and network congestion. In the meantime, ref. [7][19] proposed a context-based ZT architecture access control system to address security issues in a heterogeneous Moodle application. This framework employs the Zero Trust concept to offer access control for the e-Learning platform Moodle, demonstrating positive webserver performance gains. However, additional tests are required to evaluate the Zero Trust model’s non-functional performance.
The ZT security framework that featured by continual verification of identity and minimal power distribution, is capable of meeting the safety control needs of various contemporary networked devices. A proposed system for access control and permission relies on the ZT security architecture. Individual identities and confidence from users are derived based on behaviour of users. The system utilizes real-time hierarchy oversight across many settings to effectively accomplish flexible and precise control of access and authentication.
Taxonomy of Zero Trust Network Features
Figure 23 depicts the way significant features in ZT networks are classified. These features are elaborated as follows:
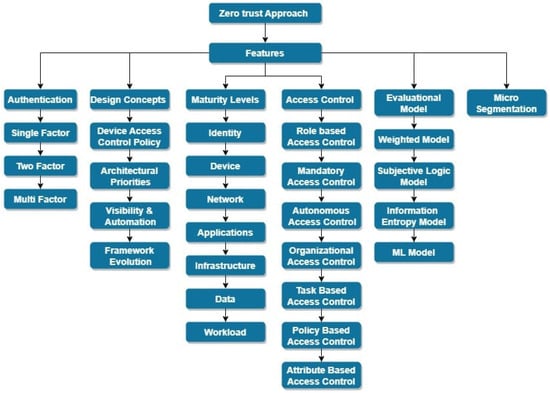
Figure 23.
Taxonomy of Zero Trust features.
Authentication: This feature is concerned with validating user credentials in order to distinguish legitimate users from bad actors attempting to obtain unauthorized access. To secure the identification of valid users and to protect devices and data from unauthorized access, robust authentication procedures are required [8][20].
A ZT network’s design policies include features, such as device access policies, architectural policies, frameworks, and automation. These policies guide the ZT networks’ implementation and operation.
Maturity levels: A ZT network’s maturity is classified into different levels as shown in Figure 32. The conventional level denotes the lack of a ZT implementation, whereas the advanced level denotes the partial implementation of a ZT model. The optimal level denotes complete automation and implementation of the ZT approach.

A continuous evaluation framework is a critical component of a ZT system. The module of trust evaluation analyses and assesses access requests using security data collected by the auxiliary platform, generating trust values. These trust values form the foundation of the authorization mechanism, allowing for dynamic and refined trust assessment.
Micro-segmentation: This method splits the system into small segments having their own security and access control policies set [10][21]. Micro-segmentation can prevent unapproved usage of crucial information or assets and limit the potential implications of a breach.
Access control: This is an essential prerequisite for ZTA, as it involves the capability to determine the privileges of a subject and subsequently limit access based on those privileges. The primary objective of logical access control is to safeguard resources, including information, components, and programmes by regulating the activities that a subject is permitted to perform on them [11][22].
In order to successfully execute a designated action on a specified entity, the individual must adhere to the established access control protocols. Specifically, if the prescribed policy requirements are met, permission to interact with the entity is granted.
Overall, these important elements contribute to a ZT network’s efficacy and security by guaranteeing robust authentication, well-defined design principles, incremental maturity levels, fine-grained access control evaluation, and the implementation of micro-segmentation for increased security.
