Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 2 by Camila Xu and Version 1 by Bahaa Yamany.
In the Machine Learning approach, machine learning algorithms analyze and categorize ransomware behavior. Trained on datasets of both known ransomware and benign samples, these algorithms identify new ransomware based on learned characteristics. Machine learning techniques, such as Decision Trees, Support Vector Machines, and Artificial Neural Networks, are applied. Advantages include adaptability to new ransomware variations and scalability for handling large datasets.
- dynamic analysis
- encryption
- honeypot
- Jaccard index
- malware
- machine learning
1. Introduction
Malware analysis is the act of finding, comprehending, and minimizing the potential damage caused by malicious software, such as ransomware in ref. [1]. It is a crucial component of cybersecurity since it enables organizations and individuals to defend themselves against the numerous types of malware that might infect their systems and data. Malware analysis employs a variety of tools and methodologies, including static analysis, dynamic analysis, sandbox analysis, and reverse engineering. These methods can be used to analyze the code and behavior of malware and to identify indicators of compromise (IOCs) that can be used to detect and categorize malware. Malware analysis is an important part of defending against ransomware as it allows organizations and individuals to identify and mitigate the potential harm caused by ransomware before it can cause significant damage or disruption. It can also help to identify and track the activities of ransomware operators, which can provide valuable intelligence for law enforcement and other cybersecurity professionals. In addition to traditional malware analysis techniques, there are also automated malware analysis tools and platforms that can be used to automate and streamline the analysis process. These tools can help to reduce the time and resources required for manual analysis, as well as increase the speed and accuracy of the analysis process in ref. [2]. However, it is important to carefully consider the benefits and limitations of automated malware analysis as it may not always provide the same level of depth and detail as manual analysis. Static analysis and dynamic analysis are two approaches that can be used to analyze and classify ransomware in ref. [3]. Both approaches have their own benefits and limitations, and they can be used in combination or separately depending on the specific needs of the analysis.
Ransomware represents a form of malicious software that encrypts a victim’s files and subsequently demands a ransom in exchange for the decryption key. This perilous threat is marked by its rapid proliferation and constant evolution, resulting in significant harm and disruption to individuals and entities worldwide [4]. Ransomware deployment encompasses various techniques, including exploit kits, drive-by downloads, and social engineering strategies. Common vectors for its transmission include email attachments, compromised websites, and software vulnerabilities. Upon infiltration, ransomware typically encrypts a wide array of files, ranging from documents to images, holding them hostage. Subsequently, victims are confronted with ransom demands, often presented through on-screen messages, or concealed notes within their systems. These demands typically include a stipulated payment deadline and a menacing ultimatum to delete the victim’s data should the ransom go unpaid. The repercussions of a ransomware attack can be profound, resulting in operational disruption, critical data loss, and substantial financial setbacks. Victims facing such attacks may find themselves at a crossroads, compelled to either pay the ransom for data recovery or explore alternative avenues, such as data restoration from backups or decryption techniques. Importantly, even when a ransom is paid, there is no guarantee that the ransomware operators will honor their promise to provide the decryption key [5]. The escalating prevalence and sophistication of ransomware assaults pose a global threat to both individuals and businesses. Being prepared to respond to and recover from such attacks, as well as proactively recognizing the threat and implementing precautionary measures, assumes paramount importance for safeguarding against this formidable adversary [6]. Figure 1 offers a comprehensive overview of the various phases involved in a ransomware attack, spanning from its inception to the extortion phase.
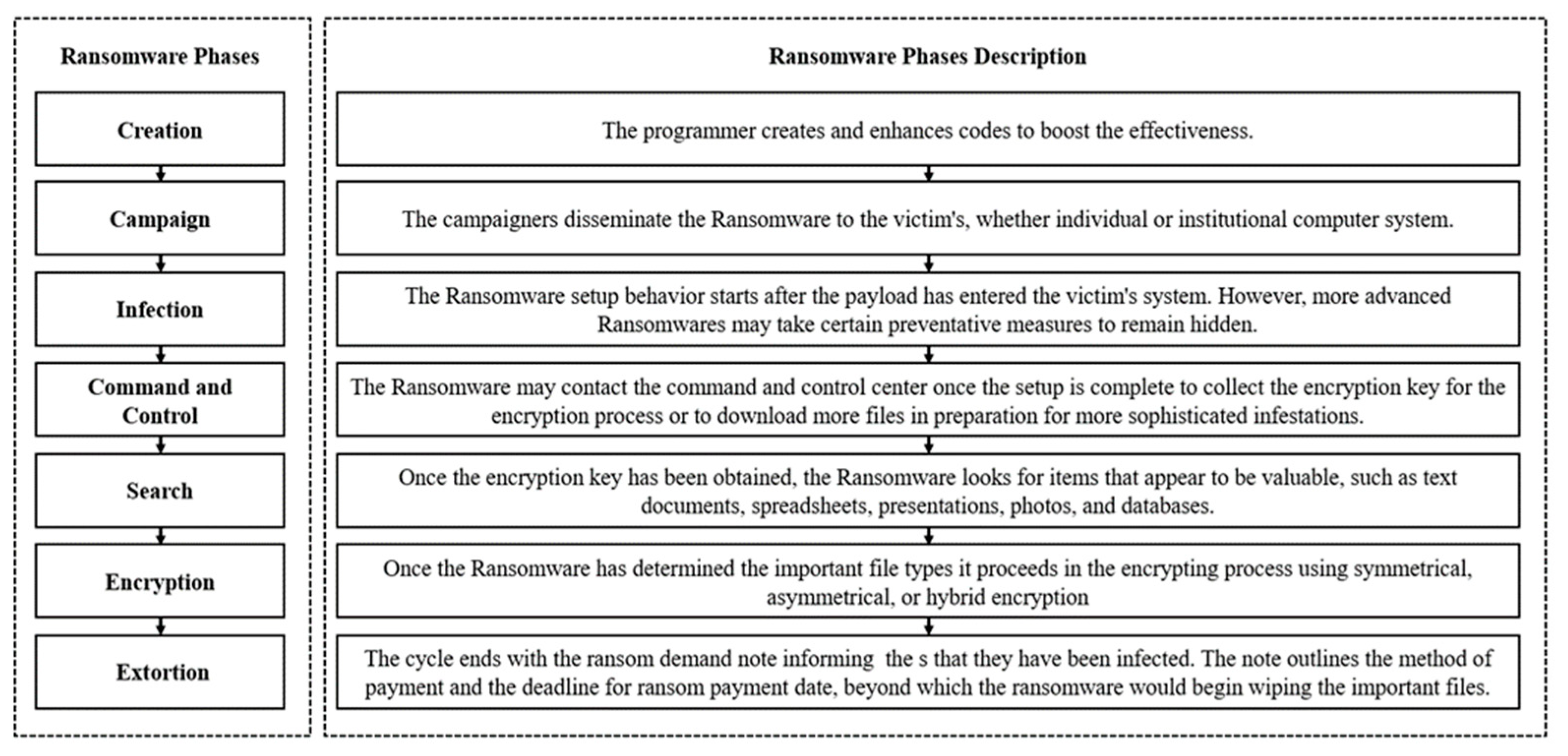
Figure 1.
Ransomware lifecycle from creation to extortion.
2. Ransomware Detection Approaches and Techniques
In the Machine Learning approach, machine learning algorithms analyze and categorize ransomware behavior. Trained on datasets of both known ransomware and benign samples, these algorithms identify new ransomware based on learned characteristics. Machine learning techniques, such as Decision Trees, Support Vector Machines, and Artificial Neural Networks, are applied. Advantages include adaptability to new ransomware variations and scalability for handling large datasets. However, accuracy hinges on dataset quality, diversity, and algorithm complexity. The Honeypot approach entails establishing networks or systems designed to attract and ensnare ransomware. These systems simulate vulnerability to lure ransomware attackers and monitor their activities. Benefits encompass real-time collection and analysis of new ransomware samples and the ability to discern attacker behavior trends and patterns. Nonetheless, Honeypots require substantial resources and maintenance and may not detect all ransomware types. The Statistical Analysis approach scrutinizes the statistical attributes of ransomware samples to uncover common patterns and features. Techniques like frequency analysis, entropy analysis, and n-gram analysis are employed. Advantages include rapid analysis of large datasets and the identification of shared patterns across diverse ransomware types. However, it may struggle with sophisticated or novel ransomware and could yield false positives if benign samples exhibit similar statistical characteristics. Each approach possesses its own merits and drawbacks, making them suitable for specific ransomware detection scenarios. The choice of approach should align with the requirements and constraints of the detection system. Careful consideration is vital when selecting the appropriate methodology.
2.1. Machine Learning
Machine Learning leverages algorithms grouped into categories like Bayesian, decision tree, dimension reduction, instance-based, clustering, deep learning, ensemble, neural network, regularization, rule system, and regression. These algorithms are utilized for ransomware detection by analyzing and classifying behaviors. Bayesian algorithms, rooted in Bayesian statistics, employ probabilistic models for event likelihood predictions, commonly applied in spam filters and malware detection systems. Decision tree algorithms employ tree-like structures to make decisions based on predefined conditions or rules, often used for classifying malware. Dimension reduction reduces dataset features for easier analysis, aiding in identifying malware patterns and characteristics. Instance-based algorithms make predictions based on stored instances or examples, useful in recognizing malware patterns. Clustering algorithms group similar data points, employed to identify malware features. Deep learning utilizes artificial neural networks for pattern recognition. Ensemble algorithms combine multiple models to enhance accuracy, while neural network algorithms employ artificial neural networks for pattern detection. Regularization algorithms prevent overfitting in complex models. In ref. [12][7], a machine learning-based model distinguished ransomware from normal files and other malware, with an automatic detection model enabling the identification of new ransomware samples. Ref. [13][8] explored research projects employing machine learning and deep learning for ransomware detection. Ref. [14][9] utilized a digital DNA sequencing engine and AI machine learning network to classify ransomware into distinct families based on their “digital genomes”. Researchers in [15][10] employed hybrid multi-level profiling for a comprehensive forensic investigation of crypto ransomware. They introduce the concept of “behavioral chaining” and employ tools for mining associative rules and AI. Profiling ransomware behavior based on its chain ratio introduces a novel approach to creating unique ransomware signatures.
2.2. Honeypots
Honeypots are valuable tools for gathering information about attacks, including the identification of users and the extent of their activities, aiding in informed decision-making for defense strategies. The primary objective of deploying honeypots is to acquire insights into ongoing attacks and utilize that intelligence to bolster security measures. To enhance user awareness, email notifications are sent, occasionally advising users to disconnect network cables as a precautionary measure. This user training aspect adds an extra layer of security awareness, making honeypots an effective means to detect ransomware attacks. In ref. [16][11], the authors employed a combination of methods, including machine learning for grouping cases and Honeypots to capture potentially malicious packages. Classification tasks utilize Decision Trees and Support Vector Machine (SVM). The study suggests the potential of architectural solutions for malware detection. Ref. [17][12] introduced an Intrusion Detection Honeypot (IDH), comprising Honeyfolder, Audit Watch, and Complex Event Processing (CEP). IDH is designed to mimic vulnerability while also functioning as an early warning system, notifying users of suspicious file activity. Ref. [18][13] presented a deception method involving Honeyfiles and Honeytokens, designed to access compromised private files and detect hacking or ransomware attempts. The hypothesis explores the use of honeypots combined with machine learning for malware detection. In ref. [19][14], data from an Internet of Things (IoT) honeypot were effectively employed to train a dynamic machine learning model. This highlights the dynamic nature of honeypot-driven machine-learning techniques. Ref. [20][15] suggested a framework utilizing an Intrusion Prevention System (IPS) gateway, an analytical system, and honeypots to detect and identify ransomware. The framework encompasses six elements: IPS, gateway, static detector, dynamic detector, honeynet, and a notification component, collectively contributing to effective ransomware detection and user notification. These studies underscore the versatility and potential of honeypot-driven approaches, often combined with machine learning techniques, for enhancing ransomware detection and overall cybersecurity.
2.3. Statistics
To better understand the characteristics of ransomware, it may be possible to employ statistical analysis. One prominent method of detecting ransomware is using statistical analyses, which can identify unpredictable behavior and be used to flag the presence of encryption. Based on the frequency of opcodes in the portable executable file, the authors in ref. [21][16] proposed an approach for detecting malware. The study used a machine learning system to detect false positives, false negatives, true positives, and true negatives in malware. While the authors in ref. [22][17] proposed a method for finding malware. This research employed a machine learning algorithm to identify malware with varying degrees of accuracy. The method of malware detection was developed by the authors using a similarity measurement algorithm. The proposed method was meant to boost malware detection times and throughput. This methodology has various advantages over others, including increased speed by using opcodes directly and improved detection outcomes from being immune to obfuscation and disassembly methods in ref. [23][18]. Another approach for malware was classification presented in ref. [24][19] inspired by the aesthetic similarities across viruses in the same family, this work proposes binary texture analysis over greyscale photos generated directly from malware executables. This technique provides statistical texture features of the second order over the graphical representation of malware. This strategy cannot be fooled by common methods of concealment (e.g., packing, code relocation, and encryption). Five malware detection metrics were assessed in the absence of ground truth, a real-world scenario that poses various technical challenges, the end goal was to develop fully automated, principled methods to assess these indications with the highest possible precision. Estimators of statistical significance were provided for the five measures used to identify malware. These statistical estimators were shown to be accurate by comparison to the known truth and fictional data. This large dataset was obtained from VirusTotal, and the estimators were then utilized to measure and quantify five metrics in ref. [25][20]. Several methods proposed in the literature make use of multiple strategies. The benefits and drawbacks of various ransomware detection strategies are summarized in Table 1.
Table 1.
Comparison between ransomware detection approaches.
| Ransomware Detection Approach | Ref. | Description | Advantages | Disadvantages |
|---|---|---|---|---|
| Machine Learning | [12,13,14,15][7][8][9][10] | The most used machine learning techniques in ransomware detection include supervised learning, unsupervised learning, and semi-supervised learning. Supervised learning involves training a model on labeled data, where the input and output are both known. This allows the model to make predictions based on the relationships learned from the training data. Unsupervised learning involves training a model on data where the output is not known, and the model must find patterns and relationships within the data on its own. Semi-supervised learning is a combination of supervised and unsupervised learning, where the model is trained on a mix of labeled and unlabeled data. | One of the main advantages of using machine learning for ransomware detection is that it allows for the automatic identification of patterns and relationships within large datasets. This can be particularly useful for identifying new and emerging threats, as the model can learn from past data to identify patterns and make predictions about future threats. Machine learning algorithms can also be trained on a wide variety of data types, including text, images, and audio, which makes them useful for detecting ransomware in different formats. | Machine learning algorithms can be vulnerable to bias and can produce inaccurate results if the training data are not representative of the real-world data. They also require frequent retraining to ensure that they continue to perform well as the data distribution changes. |
| Honeypot | [16,17,18,19,20][11][12][13][14][15] | Honeypots are a type of decoy system that is designed to attract and detect malware or cyber-attacks. They are used to lure attackers into a controlled and isolated environment, where their actions can be observed and studied. By setting up a honeypot, it is possible to monitor and track ransomware activity and identify new strains or variants of the malware. | One advantage of using a honeypot is that it allows researchers to gather valuable data and intelligence about the tactics, techniques, and procedures (TTPs) used by attackers. This information can be used to improve the effectiveness of ransomware detection and prevention measures. Additionally, honeypots can help mitigate the impact of ransomware attacks by preventing the malware from reaching the target system or data. | There are also some disadvantages to using honeypots. One potential issue is the risk of false positives, where legitimate activity is mistaken for malicious activity. Another issue is the cost and resources required to maintain and operate a honeypot, as well as the potential legal and ethical considerations. Additionally, honeypots may not be suitable for all types of environments or organizations and may not provide comprehensive protection against all types of ransomware attacks. |
| Statistical | [21,22,][16][23,17][24,18][19]25[20] | The statistical analysis approach involves collecting and analyzing data about ransomware behavior to identify patterns and trends. This can be done through various methods, such as collecting data about the frequency and types of ransom demands, the types of files targeted, and the tactics used by ransomware operators. | The advantage of using statistical analysis is that it allows researchers to gain a deeper understanding of ransomware behavior and identify key trends that can inform prevention and detection efforts. | The disadvantage of this approach is that it relies on the availability of accurate and comprehensive data, which may be difficult to obtain in some cases. Additionally, statistical analysis may not be able to identify specific instances of ransomware in real time, making it less effective for immediate detection and response. |
References
- Gopinath, M.; Sethuraman, S.C. A comprehensive survey on deep learning based malware detection techniques. Comput. Sci. Rev. 2023, 47, 100529.
- Brown, A.; Gupta, M.; Abdelsalam, M. Automated machine learning for deep learning based malware detection. Comput. Secur. 2024, 137, 103582.
- Kok, S.; Abdullah, A.; Jhanjhi, N.; Supramaniam, M. Ransomware, threat and detection techniques: A review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 136.
- Yadav, C.S.; Singh, J.; Yadav, A.; Pattanayak, H.S.; Kumar, R.; Khan, A.A.; Haq, M.A.; Alhussen, A.; Alharby, S. Malware analysis in iot & android systems with defensive mechanism. Electronics 2022, 11, 2354.
- Rey, V.; Sánchez, M.S.; Celdrán, A.H.; Bovet, G. Federated learning for malware detection in IoT devices. Comput. Netw. 2022, 204, 108693.
- Johnson, S.; Gowtham, R.; Nair, A.R. Ensemble Model Ransomware Classification: A Static Analysis-based Approach. In Inventive Computation and Information Technologies: Proceedings of ICICIT 2021; Springer Nature: Singapore, 2022; pp. 153–167.
- Fernando, D.W.; Komninos, N.; Chen, T. A study on the evolution of ransomware detection using machine learning and deep learning techniques. IoT 2020, 1, 551–604.
- Khan, F.; Ncube, C.; Ramasamy, L.K.; Kadry, S.; Nam, Y. A digital DNA sequencing engine for ransomware detection using machine learning. IEEE Access 2020, 8, 119710–119719.
- Liu, K.; Xu, S.; Xu, G.; Zhang, M.; Sun, D.; Liu, H. A review of android malware detection approaches based on machine learning. IEEE Access 2020, 8, 124579–124607.
- Bae, S.I.; Lee, G.B.; Im, E.G. Ransomware detection using machine learning algorithms. Concurr. Comput. Pract. Exp. 2020, 32, e5422.
- Chakkaravarthy, S.S.; Sangeetha, D.; Cruz, M.V.; Vaidehi, V.; Raman, B. Design of intrusion detection honeypot using social leopard algorithm to detect IoT ransomware attacks. IEEE Access 2020, 8, 169944–169956.
- El-Kosairy, A.; Azer, M.A. Intrusion and ransomware detection system. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–7.
- Vishwakarma, R.; Jain, A.K. A honeypot with machine learning based detection framework for defending IoT based botnet DDoS attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 1019–1024.
- Keong Ng, C.; Rajasegarar, S.; Pan, L.; Jiang, F.; Zhang, L.Y. VoterChoice: A ransomware detection honeypot with multiple voting framework. Concurr. Comput. Pract. Exp. 2020, 32, e5726.
- Pont, J.; Arief, B.; Hernandez-Castro, J. Why current statistical approaches to ransomware detection fail. In Proceedings of the International Conference on Information Security, Bali, Indonesia, 16–18 December 2020; Springer International Publishing: Cham, Switzerland, 2020; pp. 199–216.
- Yewale, A.; Singh, M. Malware detection based on opcode frequency. In Proceedings of the 2016 International Conference on Advanced Communication Control and Computing Technologies (ICACCCT), Ramanathapuram, India, 25–27 May 2016; pp. 646–649.
- Rezaei, S.; Afraz, A.; Rezaei, F.; Shamani, M.R. Malware detection using opcodes statistical features. In Proceedings of the 2016 8th International Symposium On Telecommunications (IST), Tehran, Iran, 27–28 September 2016; pp. 151–155.
- Verma, V.; Muttoo, S.K.; Singh, V.B. Multiclass malware classification via first-and second-order texture statistics. Comput. Secur. 2020, 97, 101895.
- Du, P.; Sun, Z.; Chen, H.; Cho, J.H.; Xu, S. Statistical estimation of malware detection metrics in the absence of ground truth. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2965–2980.
- Bijitha, C.V.; Sukumaran, R.; Nath, H.V. A survey on ransomware detection techniques. In Secure Knowledge Management in Artificial Intelligence Era: 8th International Conference, SKM 2019, Goa, India, 21–22 December 2019; Proceedings 8; Springer: Singapore, 2020; pp. 55–68.
More
