Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Annas Wasim Malik and Version 2 by Rita Xu.
Cloud computing technology is rapidly becoming ubiquitous and indispensable. Despite the multiple advantages the cloud offers, organizations remain cautious about migrating their data and applications to the cloud due to fears of data breaches and security compromises.
- cloud computing
- data loss
- cloud digital forensic
- security breaches
1. Introduction
Cloud computing is a framework that permits pervasive, user-oriented, and on-demand admittance to a shared pool of configurable computing assets over the cloud (internet) without direct active management by the user [1]. The primary benefits of cloud computing are not only limited to reduction in time and costs but also agility and scalability. The idea of cloud computing was originally linked to the concepts of distributed parallel computing, utility computing, and autonomic computing. Cloud computing has different models based on deployment and service delivery. Based on cloud deployment, there are four models: public cloud, private cloud, hybrid cloud, and community cloud while based on service delivery; models could be categorized as SaaS (Software as a service), PaaS (Platform as a Service), and IaaS (Infrastructure as a Service), as shown in Figure 1 [2]. Some leading corporations, including Amazon, Google, IBM, Microsoft, Dell Technologies, Hewlett Packard Enterprise, Cisco Systems, and Oracle, have invested in cloud computing and are offering individuals and businesses a range of cloud-based solutions. In the past few years, interest in adopting the cloud computing paradigm has increased not only in the IT industry but also in other sectors like banking, finance, education, health, utility, telecom, etc. According to a study in 2020, the presence of cloud-based applications or computing infrastructure in organizations had increased to 81% from 73% in 2018 [3]. It was forecasted that global end-user investments in public cloud services would grow in 2021 to USD 304.9 billion, up from USD 257.5 billion in 2020 [4]. The ability to use on-demand, adaptable cloud models for achieving cost-effectiveness and business continuity is motivating organizations to rapidly accelerate their digital business transformation plans. Cloud computing is envisioned as a potential future of computing, and there is no doubt that cloud tools and solutions are here to stay. Cloud computing is arguably the most significant technological advancement of the 21st century. However, as cloud computing gains more recognition worldwide, concerns are also being raised about the data security and privacy issues introduced through the adoption of this modern computing paradigm. Data security and privacy have consistently been primary issues in Information Technology. The concerns regarding data security and privacy become particularly serious in the cloud computing environment because data are scattered across various locations on different machines and storage devices, including personal computers, servers, and various mobile devices. Handling data security and privacy in cloud computing is more complex than in conventional information systems. While cloud services are helping remote workers effectively collaborate as part of a team, they are also opening new opportunities for cyber-criminals to conduct cyber frauds. According to a recent study, 92% of the participating organizations still report a cloud security readiness gap, and they are not comfortable with the security consequences of moving their workloads to the cloud environment [5]. According to IBM’s data breach report, the global average total cost of a data breach in the year 2020 was USD 3.86 million with the healthcare sector alone incurring the highest industry cost of USD 7.13 million [6].
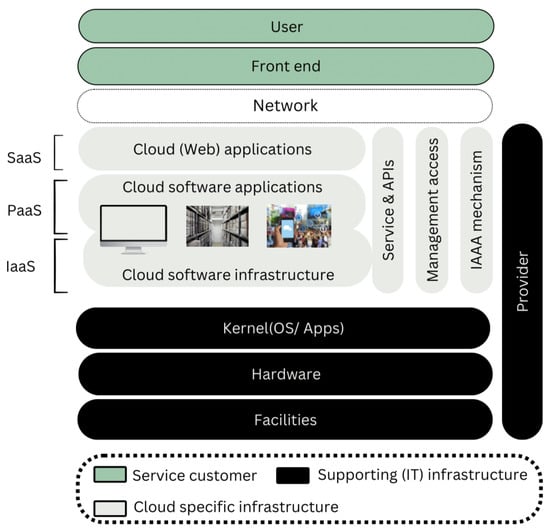
Figure 1. Models of cloud services.
In the rapidly evolving digital landscape, data breaches have become a significant concern for organizations across various industries. When a data breach occurs, highly sensitive and confidential information can be compromised, leading to severe repercussions for the affected organization [7]. The aftermath of such incidents can include financial losses, damage to the organization’s reputation, erosion of customer trust, and potential legal consequences. The increasing frequency of data breaches has raised pertinent questions about the security of data stored in cloud computing environments. While cloud computing offers numerous advantages, including flexibility, scalability, and cost-effectiveness, it also introduces inherent security risks [8]. The shared nature of cloud infrastructure and the remote storage of data necessitate a meticulous examination of cloud security practices. Addressing intricate challenges, cloud forensics emerges as a specialized subset of digital forensics, focusing on investigating and mitigating security incidents intrinsic to cloud environments [9][10][9,10]. This involves identifying vulnerabilities and attack vectors to facilitate proactive security measures, while also contributing to evidence preservation, incident response planning, regulatory compliance, and the refinement of security strategies. The iterative process sharpens security measures, reinforces employee training, and offers insights for legal remedies and third-party risk management, thus nurturing a resilient and secure digital landscape. Expertise in both digital forensics and cloud technologies is pivotal for this distinctive approach [11]. Proficient practitioners in cloud forensics meticulously gather and maintain evidence in accordance with forensic norms, preserving its integrity and authenticity for potential legal proceedings. The five key phases of digital forensics, which include identification, preservation, collection, analysis, and reporting [12].
The prevalence and impact of data breaches underscore the criticality of cloud security. While cloud security encompasses measures to protect data and systems from unauthorized access and breaches, it is essential to differentiate cloud forensics within the broader scope of digital forensics. Carrier’s work [13] on file system forensic analysis highlights the distinction between general data security practices and forensic investigations tailored for legal evidentiary standards. Cloud forensics, as a specialized domain within digital forensics, plays a pivotal role beyond data security. It involves investigating incidents, preserving evidence in a manner suitable for court admissibility, identifying vulnerabilities, and facilitating data recovery. Understanding this distinction is crucial, as expert cloud forensics practices are not solely focused on data protection but also on collecting evidence that meets legal criteria. These practices are vital for safeguarding sensitive data, upholding trust in the digital ecosystem, and mitigating the potential fallout of data breaches in cloud computing environments. Cloud forensics analyzes logs, access controls, and user activities to identify vulnerabilities in cloud infrastructure that lead to data breaches [14]. It helps organizations enhance security and recover compromised or deleted data in complex environments [15]. However, experts face technological and legal challenges in cross-border data governance, necessitating collaboration with cloud service providers. Cloud forensics is crucial in investigating incidents, preserving evidence, mitigating fallout, safeguarding sensitive data, and upholding trust in the digital ecosystem [14][15][14,15].
2. Cloud Digital Forensics
Cloud digital forensics is a specialized field that tackles cybercrime investigations in cloud environments, navigating multi-jurisdictional scenarios and evidence preservation protocols [16][88]. Its complexity is further exacerbated by the concept of multi-tenancy, and the evolving techniques and methodologies employed by cloud forensic experts [17][18][89,90].2.1. The Cloud Digital Forensic Process Model
The National Institute of Standards and Technology (NIST) defines digital forensics as a meticulous process that encompasses the recovery, preservation, and analysis of digital data with meaningful applications in criminal investigations and prosecutions [19][91]. This process is equally applicable to cloud digital forensics, which involves addressing the unique challenges posed by cloud environments. The investigation journey in cloud forensics can be distilled into four pivotal stages [20][92], each contributing to the comprehensive understanding of a digital incident, as outlined below and depicted in Figure 2. The forensic process consists of the following steps: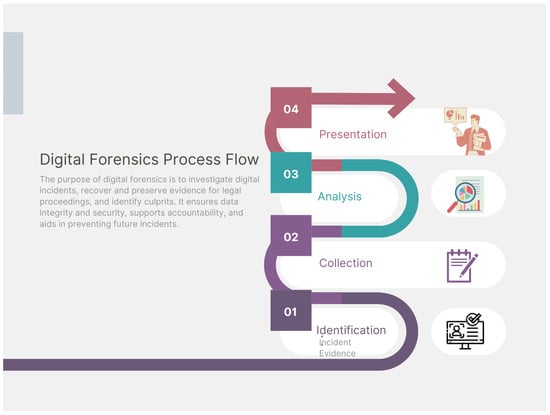
Figure 2. The cloud digital forensics process.
-
Identification: Cloud forensics involves identifying and locating relevant cloud-based systems and applications, examining the service provider, services, and data types. Detecting crimes in the cloud is more challenging than traditional forensics, often starting with unauthorized resource usage complaints. New methods are needed to efficiently use existing tools and isolate cloud evidence.
-
Preservation: The preservation stage is crucial for safeguarding digital evidence’s integrity, ensuring its legal use. It involves systematic data capture, secure storage, and documentation, acting as a digital custodian.
-
Examination and analysis: The analysis phase in cloud forensics involves using tools and methodologies to examine digital evidence, uncovering insights through log files, network activity patterns, metadata decoding, and data recovery. This phase requires technical prowess and a discerning eye.
-
Presentation: Cloud forensics aims to present investigative findings in a clear, concise manner, leveraging information as credible evidence in legal proceedings. This involves creating comprehensive reports, using visual aids, and offering expert testimony.
2.2. Cloud Digital Forensics Tools and Technologies
In the realm of cloud digital forensics, the availability of specialized tools plays a pivotal role in facilitating investigations within cloud computing environments. Table 1 delineates their key functionalities and significance in uncovering digital evidence.Table 1. Summary of digital forensic tools and their features.
| Category | Tools | Features |
|---|---|---|
| Cloud digital forensic tools | Magnet AXIOM cloud | Comprehensive cloud data collection and analysis |
| Cellebrite UFED cloud analyzer | Acquisition and analysis of data from cloud accounts | |
| Mandiant CloudLens | Visibility into cloud environments for security | |
| Volatility Framework | Memory forensics framework for virtual machines | |
| AccessData cloud extractor | Collection and preservation of digital evidence | |
| Oxygen forensic cloud extractor | Supports over 20 cloud services for forensics | |
| Autopsy | Open-source digital forensics platform | |
| BlackBag BlackLight | Analysis of data from devices and cloud services | |
| X-Ways Forensics | Examination of evidence from cloud storage, email, etc. | |
| Azure Security Center | Threat protection in Azure and hybrid environments | |
| AWS CloudTrail | API call logs in AWS accounts for forensic analysis | |
| Offline digital forensic tools | EnCase Forensic | Comprehensive forensic software for evidence |
| AccessData Forensic Toolkit (FTK) | Tool for collecting, analyzing, and examining data | |
| Forensic Falcon | Hardware-based solution for offline and live forensics | |
| Paladin Forensic Suite | Live forensic system bootable from a USB drive | |
| Digital Evidence and Forensics Toolkit (DEFT) | Linux distribution for digital forensics | |
| Bulk Extractor | Command-line tool for scanning disk images | |
| Digital forensics framework (DFF) | Open-source digital forensics platform that provides a modular and extensible framework for conducting forensic investigations. |
- Forensic Falcon: This hardware-based solution offers both offline and live forensic capabilities, allowing investigators to analyze and image digital media in the field.
-
Paladin Forensic Suite: Paladin is a live forensic system that can be booted from a USB drive. It includes a variety of open-source forensic tools and utilities for evidence collection and analysis.
-
DEFT (Digital Evidence and Forensics Toolkit): DEFT is a Linux distribution specifically designed for digital forensics and incident response. It includes a collection of pre-installed forensic tools and utilities.
-
Bulk Extractor: Bulk Extractor is a command-line tool designed to quickly and efficiently scan disk images for specific types of information, such as email addresses, credit card numbers, and URLs.
-
Digital Forensics Framework (DFF): DFF is an open-source digital forensics platform that provides a modular and extensible framework for conducting forensic investigations.
-
EnCase Forensic: EnCase is a widely used forensic software that provides comprehensive capabilities for acquiring, analyzing, and reporting digital evidence from various devices and file systems.
-
AccessData forensic toolkit (FTK): FTK is a powerful forensic tool that allows investigators to collect, analyze, and examine data from computers and mobile devices. It includes advanced searching and analysis features.
