1. Introduction
The United Nations (UN) has advocated for the Sustainable Development Goals (SDGs), which have since become an indispensable cornerstone for research frameworks within the academic and scientific communities. The Sustainable Development Goals (SDGs) are an all-encompassing collection of seventeen goals, of which SDG 11 addresses the critical challenge of promoting sustainable cities and communities worldwide. Conversely, contemporary trends underscore the increasing demand for secure systems and user privacy. This imperative did not emerge spontaneously; it is rooted in a multitude of documented cases where users suffered adverse consequences due to insecure systems and data breaches. These users encompass a wide spectrum, including corporations, governmental entities, and private citizens
[1][2][1,2].
The authors of
[2] have documented that between 2018 and 2019, the United States experienced an alarming number of data breaches exceeding 10,000 cases. Notably, among these, 430 incidents were categorized as major data breaches
[3]. In the European Union, since May 2018, over 160,000 cases have been officially reported. One particularly noteworthy instance revolves around the activities of Cambridge Analytica
[4], which exploited fifty million Facebook profiles associated with American voters. Their objective was to develop an AI system capable of influencing electoral outcomes among targeted demographic groups.
The Equifax data breach in 2017 was a significant incident that affected nearly half of the United States’ population. This breach compromised over 143 million data records
[5][6][5,6]. Similarly, Orvibo, a company specializing in Internet of Things (IoT) management platforms, exposed over 2 billion records of private information, including camera recordings of conversations, on the Internet, without any password or security measures
[7]. These incidents, among others, highlight the need for robust security solutions to protect user privacy.
Smart city applications often require access to sensitive user information, making it imperative to safeguard this data. Federated learning (FL), also known as “privacy by design”, is a promising paradigm that preserves user privacy by keeping personal data on local devices, also known as federated clients. Implementing FL can be seen as adding additional security layers to a system.
Previous studies have identified the limitations of machine learning in terms of preserving data privacy
[8]. Adversaries can potentially derive training data from the gradients of machine learning models. Deep leakage from gradients (DLG)
[9] and similar attacks
[10][11][10,11] can recover information pixel by pixel for images and token by token for text. However, these attacks still face challenges in consistently converging and uncovering true labels.
Alternative research has proposed a method for reconstructing images from the parameter gradients of models by inverting gradients
[12] using adversarial attacks. One limitation of this approach is its high computational cost—reconstructing a single image requires 24,000 iterations. Shen et al.
[13] conducted a comprehensive study of adversarial threats to distributed machine learning and federated learning. Their findings suggest that FL has several advantages over distributed machine learning. The lack of communication requirements with other clients in FL significantly reduces the risk of privacy breaches. Additionally, distributed machine learning requires more collaboration with other clients or system nodes than FL.
It is worth noting that experts in the field have hypothesized that FL systems may offer enhanced security compared to centralized systems. The insights gained from
theour previous research, as cited in reference
[14], establish the foundation for the subsequent analysis
presented in this paper. This analysis primarily focuses on identifying potential vulnerabilities and areas where data could be compromised in the event of a security breach. The scope of
theour investigation includes a comparative assessment of attack probabilities and the extent of potential losses between centralized systems and the FL paradigm.
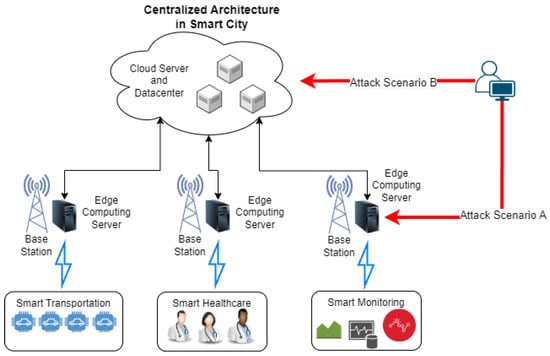
Figure 1 illustrates a generalized cloud-based architecture for smart cities, along with potential attack scenarios. This architecture typically collects data from a variety of IoT devices, such as wearable devices, smart sensors, and data loggers, which are used to support applications in areas such as intelligent monitoring, intelligent transportation, and intelligent healthcare. The collected data is then transmitted to edge computing servers, which significantly reduces data transport latency to and from centralized cloud data centers.
Figure 1. Attack scenarios in cloud-based architecture.
Edge computing plays a crucial role in facilitating real-time data processing and decision-making, a key requirement for applications demanding immediate responses, such as autonomous vehicles, robotics, and monitoring systems
[15][16][17][18][19][20][15,16,17,18,19,20]. By employing edge processing and filtering, only relevant information is transmitted to the cloud, thereby reducing network traffic
[20][21][20,21]. This optimization is particularly beneficial for applications with limited bandwidth.
Furthermore, edge computing enhances data security and privacy by limiting data exposure to external cloud services and keeping sensitive data within a local network. This approach aligns with best practices to safeguard data privacy
[16][17][21][16,17,21]. The concept of edge AI has gained prominence with the advent of edge AI devices, such as the NVIDIA Jetson Xavier AGX (NVIDIA, China), NVIDIA Jetson TX2 (NVIDIA, China), NVIDIA Jetson Xavier NX (NVIDIA, China), Google Coral Dev Board (Google Coral, Taiwan, China), and Intel NUC (Intel, Beijing, China). These devices are equipped with graphical processing units (GPUs) and substantial computational capabilities, enabling advanced AI applications at the network’s edge
[22][23][24][25][26][22,23,24,25,26].
Two potential attack scenarios that may occur in cloud architecture are illustrated in
Figure 1. Attack scenario A targets the edge server, which plays a critical role as a data storage and processor for a wide variety of IoT devices. This data often includes confidential and sensitive information
[16][17][21][16,17,21]. If an attack is successful, unauthorized actors could gain access to the confidential information of numerous clients, which could have significant financial consequences.
Attack scenario B focuses on compromising the cloud server, which stores a significantly larger amount of data than the edge server. The cloud server acts as a centralized repository for all data collected from interconnected edge servers. The Orvibo incident
[7] serves as a prime example, demonstrating how an attacker was able to access over two billion records from a cloud server with relative ease.
2. Privacy and Security in Sustainable Smart City Applications
In previous studies, diverse methods have been investigated to address security and privacy concerns within the realm of smart cities and the Internet of Things (IoT). These methods encompass the deployment of deep-learning-based intrusion detection systems, blockchain technology, and anomaly detection techniques, among others. The overarching objective of these approaches is to comprehensively fortify overall security measures. Additionally, several novel computational frameworks and architectures have been proposed to augment privacy protection. The emergence of edge GPU devices, equipped with substantial computational capabilities facilitated by GPUs, has given prominence to the concept of edge AI. Consequently, the notion of training AI models at the edge has garnered significance and viability.
In the realm of smart city applications, Singh et al.
[27][37] introduced DeepBlockScheme, a solution that combines deep learning with blockchain technology to enhance security. To illustrate its practicality, the authors conducted a case study within the domain of vehicle manufacturing. Another study by Kumar et al.
[28][38] employed blockchain and machine learning to enhance privacy and security in IoT-driven smart cities. In this context, a blockchain module ensures secure IoT data transmission. Principal component analysis (PCA) is applied to process raw IoT data into a new representation, and an intrusion detection system, the gradient boosting anomaly detector (GBAD), flags unauthorized access attempts. Despite the data integrity benefits offered by blockchain, its implementation introduces computational complexity, particularly in resource-constrained environments
[29][27]. It is noteworthy that in contemporary blockchain systems like Ethereum, data stored on blockchains is commonly publicly accessible by default, posing potential privacy concerns for individuals
[30][33].
Prior studies have introduced various frameworks and architectures aimed at supporting IoT technologies in the context of smart cities. In
[31][39], the authors leverage blockchain and software-defined networking to ensure secure data communication, privacy, and reduced computational costs. They incorporate deep learning within the cloud architecture, enhancing smart industry production with valuable analysis. Another approach is presented in
[20], where the authors utilize mobile edge computing (MEC) and the Stackelberg principle-based game theory implemented through the alternating direction method of multipliers (ADMM) within an IoT environment. This method efficiently schedules tasks for distributed devices, resulting in rapid algorithm convergence.
Addressing challenges in multimedia data management,
[16] introduces the Short Supply Circuit Internet of Things (SSCIoT). This research primarily focuses on tackling data processing challenges when cloud access is limited or unavailable. The architecture emphasizes the utilization of mobile edge computing and fog computing over cloud computing to deliver quicker responses to users.
Numerous researchers have explored the integration of federated learning (FL) within the IoT and smart city domains, deviating from conventional approaches involving data transfer to multiple points. The foundational principle of FL revolves around maintaining data on the client side, as discussed earlier, aiming to fortify system security and privacy. In
theour prior research
[32][40],
rwe
searchers introduced a federated trustworthy AI (FTAI) architecture tailored to meet seven key requirements of trustworthy AI (TAI) outlined by the European Union
[33][41]. Specifically,
in th
e is paper, the proposed method delves into TAI requirements two and three, focusing on robustness, safety, privacy, and data governance.
In a comprehensive survey
[34][42], researchers explored FL’s implementation for IoT, covering aspects such as data exchange, offloading, caching, attack detection, location services, mobile crowdsensing, privacy, and security. The study extensively discussed FL’s applications across various domains, including smart healthcare, transportation, UAVs, cities, and industries. Challenges associated with FL-IoT implementations, such as adversarial attacks, non-IID data, low convergence rates, and heterogeneous client computational resources, were thoroughly outlined. In a distinct study
[35][43], researchers integrated FL and blockchain technology to enhance privacy and scalability within smart healthcare systems. It is noteworthy that this conceptual architecture lacks empirical evidence regarding its implementation results.
Adversarial attacks on IoT systems and their ramifications have been subject to extensive investigation in prior research. In
[36][44], researchers delved into the impact of both nontargeted and targeted adversarial attacks, employing methods such as the fast gradient signs method (FGSM) and projected gradient descent (PGD) on CNN-based IoT device identification. The study revealed a degradation in identification accuracy with increasing perturbation and iteration step size. In
[37][45], the authors scrutinized adversarial attacks on deep-learning-based intrusion detection within IoT networks, comparing the effectiveness of two deep learning techniques: feedforward neural networks (FNNs) and self-normalizing neural networks (SNNs). Results indicated that SNNs exhibited greater resistance to adversarial samples in IoT datasets.
Moreover,
[38][46] introduced a partial-model adversarial attack on IoT systems using machine learning (ML). Their findings underscored the vulnerability of ML-based IoT systems to adversarial attacks, particularly when an adversary targeted only 8 out of 20 IoT devices, achieving an 83% success rate. In
[39][47], researchers assessed the efficacy of adversarial attacks on ML-based detection of denial-of-service (DoS) attacks in IoT smart home networks. The introduction of adversarial samples into the test data resulted in a 47.2% decrease in model accuracy, with subsequent improvements observed after employing adversarial training.
As previously highlighted, adversarial attacks extend their impact to both ML and deep learning (DL) models, with federated learning (FL) not immune to such vulnerabilities
[13][29][30][40][41][42][43][44][45][46][13,27,29,30,31,32,33,34,35,36]. In an endeavor to fortify defenses against poisoning attacks,
[47][48] introduced a method utilizing generative adversarial networks (GANs) to generate auditing data during the training process. This approach incorporates a mechanism to identify and eliminate adversaries by auditing the accuracy of their models and integrating a GAN into the federated learning server. The GAN’s role involves constructing an auditing dataset capable of detecting adversaries by evaluating the correctness of participant models.
In the pursuit of robust federated learning,
[40][29] introduces the robust framework for federated learning (RFFL). This framework is crafted to adeptly identify and eliminate malicious behaviors in a cautious and iterative manner before aggregating model updates. By adopting this approach, RFFL establishes a robust learning framework, effectively mitigating the risks associated with data poisoning and model update poisoning attacks. This methodology shares commonalities with the work presented in
[47][48], where a similar notion of implementing filtering on the federated server before aggregation is employed. However, both approaches raise concerns regarding the overall robustness of the global model against adversarial attacks, as they do not incorporate adversarial samples into their model training, thereby questioning the ability to create a truly robust model.
Addressing adversarial attacks in federated learning poses a significant challenge, with
[41][44][46][30,34,36] highlighting the complexities involved. Notably,
[41][30] acknowledges the inherent difficulties of implementing adversarial training in a federated setting, primarily attributed to the data-intensive requirements of such training. Previous research endeavors have been dedicated to identifying effective approaches to overcome these challenges.
The integration of FL and IoT has transitioned from a conceptual possibility to a practical reality, facilitated by the emergence of mini-computers equipped with GPUs, commonly known as “edge GPUs”. These devices enable the processing of multimedia data at the edge, giving rise to the concept of “edge AI”
[22][23][24][25][26][22,23,24,25,26]. This evolution has spurred increased research initiatives exploring the application of AI at the edge. For instance, in a study conducted by
[22], researchers utilized the NVIDIA Jetson Nano to develop a model for detecting vehicles and pedestrians on rural roads. Through extensive testing of well-established models, including MobileNetv1, MobileNetv2, Inceptionv2, Pednet, and Multiped, they demonstrated the effective functionality of these models on the NVIDIA Jetson Nano.
Another exploration by Mathur et al.
[24] delved into the feasibility of on-device FL. In this investigation, Android smartphones and the Nvidia Jetson TX2 played a pivotal role. These devices were leveraged to train a model following the federated learning methodology through the utilization of the Flower framework. The training process involved the CIFAR-10 dataset for the Nvidia Jetson TX2 and the Office-31 dataset for Android clients. The findings from this study provide compelling evidence for the viability of training AI models on edge devices, especially with lightweight models such as ResNet18. Moreover, Truong et al.
[26] harnessed the power of FL to train a lightweight anomaly detection model tailored for industrial control systems. By embracing FL, the learning process was significantly expedited, with completion times reduced to a matter of minutes. The research involved the use of four NVIDIA Jetson Nanos as federated clients, demonstrating the potential for efficient AI training on edge devices.
In order to address the aforementioned security and privacy issues associated with sustainable smart city applications, adversarial training strategies have been implemented within the framework of federated learning. These methodologies have been specifically developed to overcome the challenges that arise from clients having limited datasets, with the ultimate goal of developing a robust global model. This approach exhibits potential for improving the security and privacy aspects of smart city applications and is viable when federated clients are outfitted with GPU support.