Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 3 by Catherine Yang and Version 2 by Catherine Yang.
With the advent of the Internet-of-Things (IoT) technologies, millions of low-resource devices are constantly used at the network’s edge. As a result, the large amount of private and sensitive data generated by these devices must be securely transported, stored, and processed, posing a challenge because these resource-constrained IoT devices cannot meet the criteria of conventional encryption ciphers. Feistel networks are further divided into two types: classical Feistel networks and generalized Feistel networks (GFN). While classical Feistel ciphers divide a message into two sub-blocks, GFN divides a message into k sub-blocks for some k > 2 called the partition number.
- lightweight block cipher
- modified Feistel
- randomness test
- advand effect test
1. Introduction
The Internet of Things (IoT) is a re-evolution and improvement of the currently Internet-connected computer components [1]. In recent years, there has been a rise in the use of low-powered IoT devices. According to IoT Analytics, the Internet-of-Things market is expected to grow by 18% to 14.4 billion active connections in 2022 [2]. By 2025, more than 30 billion connected Internet-of-Things devices will be connected. These devices are not only ubiquitous, but they also form the backbone of a network that provides users with stealthy benefits. Connected devices, such as automobiles and household appliances, comprise electronic circuitry, software, actuators, and networks. IoT devices can collect vast amounts of data, analyze the data, make intelligent decisions, and distribute the results back to the devices so they can act intelligently.
With the widespread adoption of high-speed wireless technology and the proliferation of “smart” devices, the Internet of Things (IoT) has grown exponentially, with IoT devices producing vast quantities of data. According to a recent report by DataProt, the amount of data generated by IoT devices will reach 73.1 zettabytes (ZB) by 2025 [3]. However, the increased connectivity of these devices has made it easier for cybercriminals to gain unauthorized access to private information on the networks, as certain devices may be susceptible to attacks. Therefore, cryptography, a branch of mathematics related to creating secure communication protocols for data transmission, is used as a crucial component of information security to protect communication systems.
In today’s digital age, cryptography plays a critical role, particularly in the Internet of Things (IoT), where connected devices are vulnerable to numerous security threats, such as hacking and eavesdropping. As the number of connected devices in the IoT continues to increase, the need for secure communication protocols has become more pressing, making cryptography an indispensable tool for ensuring the confidentiality, integrity, and authenticity of data transmitted over IoT networks. However, conventional cryptography algorithms are unsuitable for use in resource-constrained IoT devices due to their high resource demands. Consequently, lightweight cryptography is employed for smart objects in the IoT environment as a replacement for traditional cryptography techniques. For IoT security, a number of lightweight cryptography techniques are available, including lightweight block ciphers, lightweight hash functions, lightweight message authentication codes, and lightweight stream ciphers, with lightweight block ciphers being the most frequently used.
Over the years, several lightweight block ciphers, such as PRESENT [4], LED [5], RECTANGLE [6], SKINNY [7], and SPECK [8], have been developed with simple structures and a high throughput for efficient implementation. While several new lightweight block ciphers have recently been proposed, they have yet to undergo extensive cryptanalysis to be considered as state-of-the-art. Additionally, in low-power and lossy networks, security remains a significant concern, necessitating the need for more innovation in developing lightweight algorithms.
A lightweight block cipher must possess confusion and diffusion properties in its design components to provide sufficient security to the algorithm [9]. Confusion uses a substitution function to obscure the relationship between plaintext and ciphertext, whereas diffusion uses a permutation function to distribute the plaintext statistics throughout the ciphertext. To achieve these objectives, there are two main fundamental structures of lightweight block ciphers: the Feistel network and the substitution–permutation network (SPN). While different techniques can be used to develop algorithms, they are based on either one of these foundational structures. The encryption and decryption operations in the SPN lightweight block cipher are non-identical, requiring additional cycles and codes for execution. In contrast, the encryption and decryption processes in the Feistel lightweight block cipher are similar [10]. Feistel ciphers do not require additional cycles and codes for execution, resulting in a low memory usage and the ability to be implemented in hardware with a low average power consumption.
Feistel networks are a popular choice for implementing lightweight block ciphers, with classical Feistel networks and generalized Feistel networks (GFN) being the two main types. While classical Feistel networks divide messages into two sub-blocks, the GFN divides them into k sub-blocks, where k is greater than 2. The GFN of Type-II, in particular, is a popular form where the Feistel transformation is applied to two consecutive sub-blocks, followed by a cyclic shift of sub-blocks. This type of Feistel structure is easy to implement and has been used in ciphers such as RC6 [11], HIGHT [12], and CLEFIA [13]. However, it is important to note that the Type-II GFS has low diffusion properties and requires a larger number of rounds to achieve full diffusion [14][15], meaning all output sub-blocks are affected by all input sub-blocks.
2. The Modified GFN Lightweight Block Cipher
This section outlines the fundamental design principles of the modified GFN lightweight block cipher (MGFN) by introducing a unique set of operations and transformations that deviate from the conventional Feistel cipher. The MGFN utilizes a Type-II Feistel structure that has been modified for its architecture. Unlike conventional Type-II GFN ciphers, as shown in Figure 1a,b, the MGFN’s round and block permutation functions have unique designs and operations. To further illustrate the MGFN lightweight block cipher, please refer to Figure 2.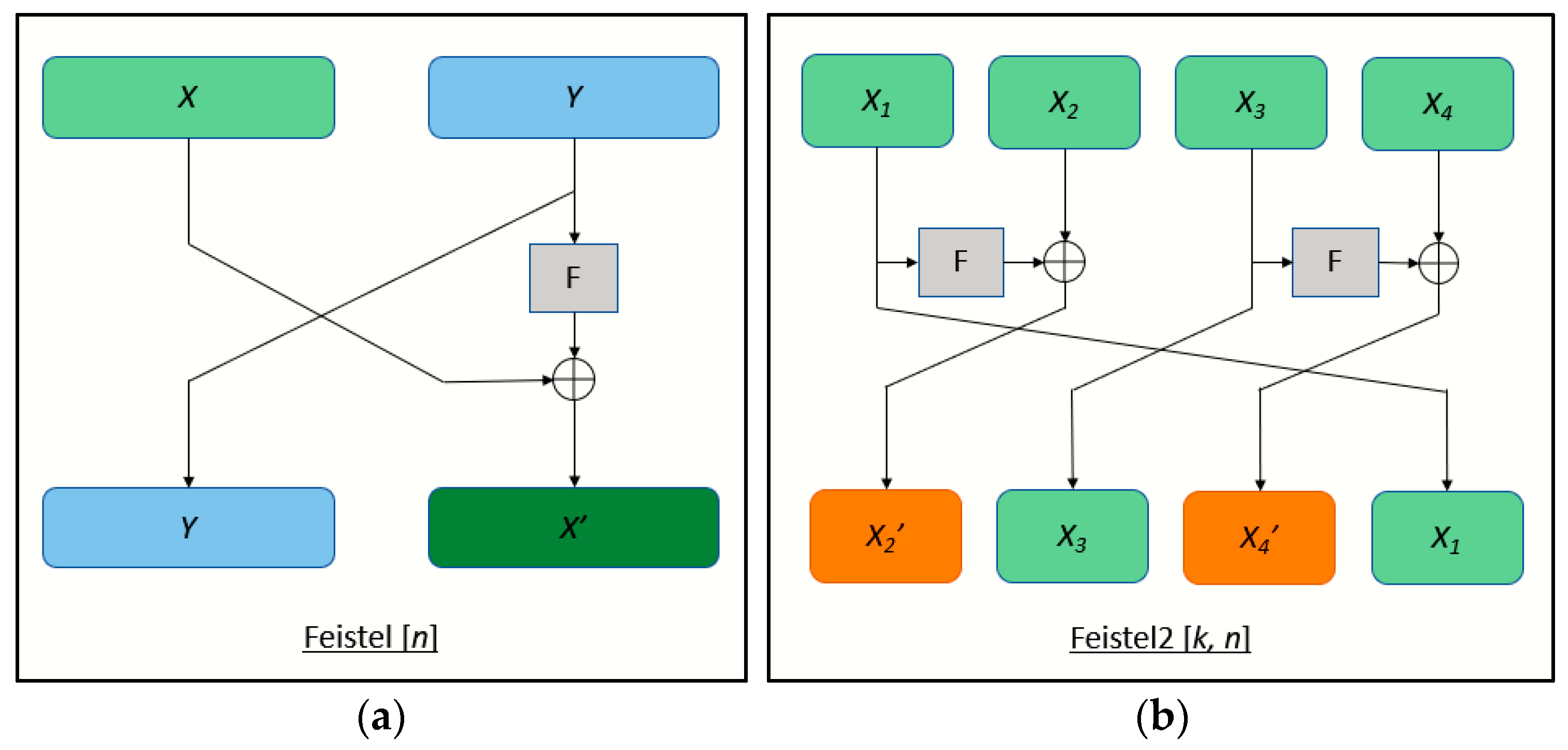
Figure 1. (a) Classical Feistel; and (b) Type-II Feistel.
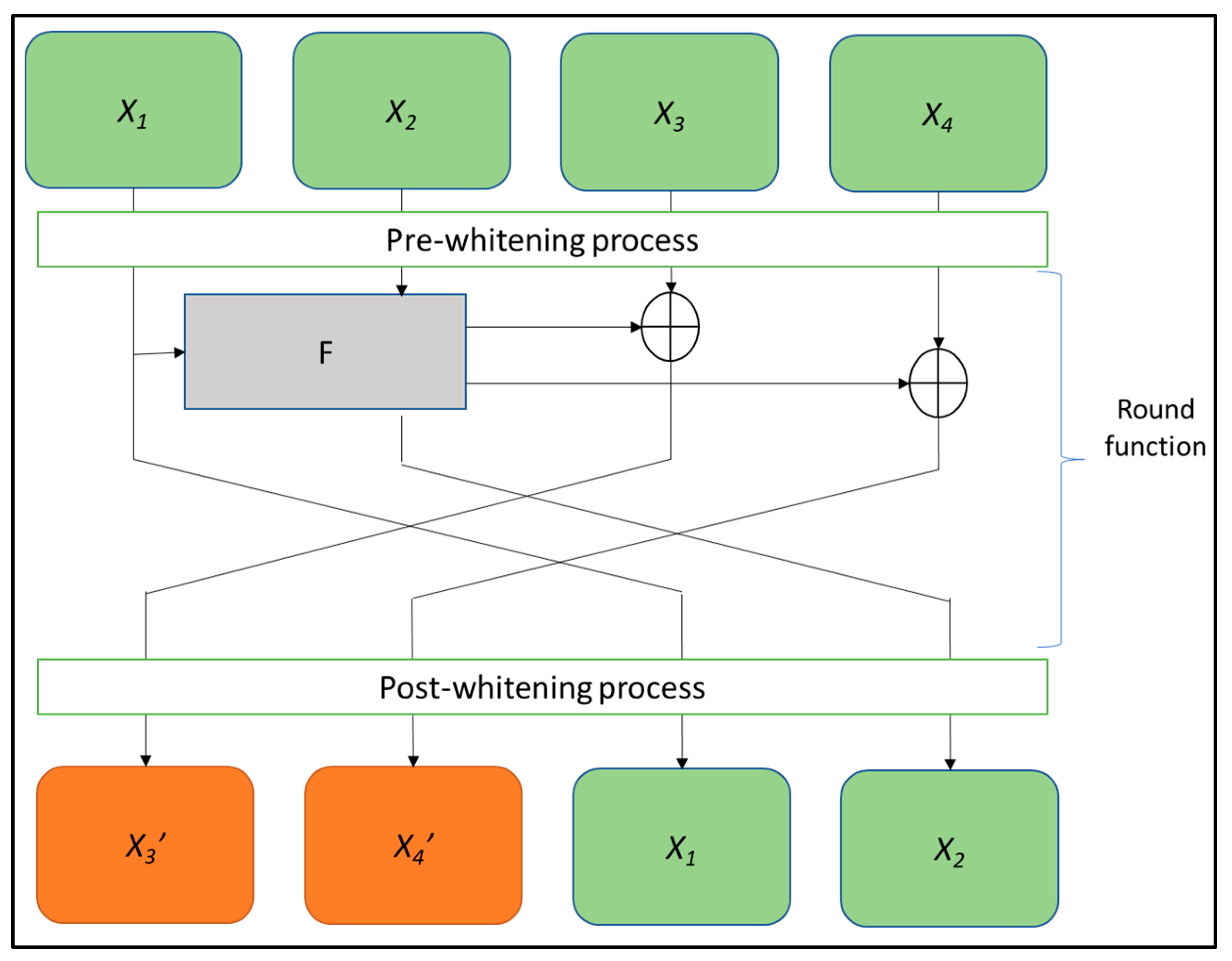
Figure 2. The description of MGFN lightweight block cipher.
2.1. Encryption Process
Initially, the 64-bit plaintext P is segmented into 16-bit word sequences. The cipher state comprises 24 rounds for processing 64-bit input and output data, with encryption operations leveraging the 128-bit key. This 128-bit key serves as a master key that generates 56 subkeys with a length of 64 bits each, which are employed in the encryption pre-whitening, round function, and post-whitening process. To encrypt a 64-bit plaintext, the MGFN algorithm first divides it into four 16-bit blocks, 𝑃0, 𝑃1, 𝑃2, and 𝑃3, where 𝑃 is the least significant 16 bits. The algorithm then applies pre-whitening on 𝑃0, 𝑃1, 𝑃2, and 𝑃3 before entering the round function. Next, in the round function, the F-Function is applied to 𝑃0 and 𝑃1, which comprises four layers: the AddKey layer, the RShift layer, the SBox layer, and the PBox layer. Each layer’s procedure is described as follows:-
addKey layer: In this layer, the two input words are XORed with subkeys.
| 𝒙 | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | A | B | C | D | E | F |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 14 | 15 | |||||||||||||||
| 𝑷[𝒊] | 4 | 11 | 18 | 7 | 23 | 19 | 2 | 25 | 14 | 26 | 1 | 28 | 20 | 8 | 29 | 0 |
- RShift layer: This layer allows the two input words to undergo rotation shifts of 3 and 8 bits, respectively.
| 𝑺[ |
Table 2. The permutation bit in MGFN.
| i | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | ||
| i | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
| 𝑷[𝒊] | 31 | 5 | 15 | 21 | 9 | 13 | 24 | 6 | 17 | 12 | 22 | 3 | 16 | 30 | 10 | 27 |
| 𝒙] | 7 | E | F | 0 | D | B | 8 | 1 | 9 | 3 | 4 | C | 2 | 5 | A | 6 |
- SBox layer: In this layer, a 4-bit input, denoted by
- x, is transformed into a 4-bit output, denoted by S[x]. It should be noted that S[x] may not necessarily be equal to s. The values of x and S[x] used in this layer are provided in Table 1. The resulting outputs from this layer are then combined to form a 32-bit word.
-
PBox layer: In this layer, each of the 32 bits in the input word is mapped to its corresponding output position, with the specific mapping specified in Table 2. It is worth noting that the values in Table 2 are sourced from the ultra-lightweight PICO [16] algorithm, which is known for its exceptional performance in customized hardware.
Table 1. The S-box used in MGFN.
2.2. Key Schedule Process
The key schedule of the MGFN lightweight block cipher was developed by modifying the PRESENT [4] algorithm. The key provided by the user consists of 128 bits and is represented as 𝑘127𝑘126…𝑘0, and is stored in the K key register. In round i, the 64-bit-register round key 𝐾𝑖 are rotated 61 bits to the right, and the 64 leftmost bits of the resulting value are used as the new round key. After extracting 𝐾𝑖, the key register 𝐾=𝑘127𝑘126…𝑘0 is updated and mathematically defined as follows:- (1)
-
𝑘127𝑘126…𝑘1𝑘0←𝑘66𝑘65…𝑘68𝑘67
- (2)
-
𝑘127𝑘126𝑘125𝑘124←𝑆[𝑘127𝑘126𝑘125𝑘124]
- (3)
-
𝑘123𝑘122𝑘121𝑘120←𝑆[𝑘123𝑘122𝑘121𝑘120]
- (4)
-
𝑘66𝑘65𝑘64𝑘63𝑘62←𝑘66𝑘65𝑘64𝑘63𝑘62⊕𝑟𝑐
References
- Zhou, S.; Xie, Z. On Cryptographic Approaches to Internet-Of-Things Security. Available online: http://www.lix.polytechnique.fr/hipercom/SmartObjectSecurity/papers/ZhouSujing.pdf (accessed on 11 March 2023).
- IoT Connections Market Update—May 2022. Available online: https://iot-analytics.com/number-connected-iot-devices/ (accessed on 11 March 2023).
- Internet of Things statistics for 2023—Taking Things Apart. Available online: https://dataprot.net/statistics/iot-statistics/ (accessed on 11 March 2023).
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.; Seurin, Y.; Vikkelsoe, C. PRESENT: An ultra-lightweight block cipher. In Cryptographic Hardware and Embedded Systems-CHES 2007, Proceedings of the 9th International Workshop, Vienna, Austria, 10–13 September 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466.
- Jian, G.; Peyrin, T.; Poschmann, A.; Robshaw, M. The LED Block Cipher. In Proceedings of the Cryptographic Hardware and Embedded Systems–CHES 2011, 13th International Workshop, Nara, Japan, 28 September–1 October 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 326–341.
- Zhang, W.; Bao, Z.; Lin, D.; Rijmen, V.; Yang, B.; Verbauwhede, I. RECTANGLE: A bit-slice lightweight block cipher suitable for multiple platforms. Sci. China Inf. Sci. 2015, 58, 1–15.
- Christof, B.; Jean, J.; Kölbl, S.; Leander, G.; Moradi, A.; Peyrin, T.; Sasaki, Y.; Sasdrich, P.; Sim, S.M. The SKINNY family of block ciphers and its low-latency variant MANTIS. In Advances in Cryptology–CRYPTO 2016, Proceedings of the 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 123–153.
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L. The SIMON and SPECK families of lightweight block ciphers. In Cryptology Eprint Archive; IEEE: San Francisco, CA, USA, 2013.
- Deepti, S.; Gill, N.S.; Devi, M. Comparative analysis of lightweight block ciphers in IoT-enabled smart environment. In Proceedings of the 2019 6th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 7–8 March 2019; IEEE: New York, NY, USA; pp. 915–920.
- Pulkit, S.; Acharya, B.; Chaurasiya, R.K. A comparative survey on lightweight block ciphers for resource constrained applications. Int. J. High Perform. Syst. Archit. 2019, 8, 250–270.
- Rivest, R.L.; Robshaw, M.J.; Sidney, R.; Yin, Y.L. The RC6TM block cipher. In Proceedings of the First Advanced Encryption Standard (AES) Conference, Ventura, CA, USA, 20–22 August 1998; p. 16.
- Deukjo, H.; Sung, J.; Hong, S.; Lim, J.; Lee, S.; Koo, B.-S.; Lee, C.; Chang, D.; Lee, J.; Jeong, K.; et al. HIGHT: A new block cipher suitable for low-resource device. In Cryptographic Hardware and Embedded Systems-CHES 2006, Proceedings of the 8th International Workshop, Yokohama, Japan, 10–13 October 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 46–59.
- Shirai, T.; Shibutani, K.; Akishita, T.; Moriai, S.; Iwata, T. The 128-Bit Blockcipher CLEFIA (Extended Abstract). In Fast Software Encryption; Biryukov, A., Ed.; FSE 2007. Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4593.
- Suzaki, T.; Minematsu, K. Improving the Generalized Feistel. In Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6147, pp. 19–39.
- Tsonka, B.; Topalova, S. On the diffusion property of the Improved Generalized Feistel with different permutations for each round. In Algebraic Informatics, Proceedings of the 8th International Conference, CAI 2019, Niš, Serbia, 30 June–4 July 2019; Springer International Publishing: Cham, Switzerland, 2019; pp. 38–49.
- Bansod, G.; Pisharoty, N.; Patil, A. PICO: An Ultra Lightweight and Low Power Encryption Design for Ubiquitous Computing. Def. Sci. J. 2016, 66, 259.
More
