The Internet of Things (IoT) is a network of billions of interconnected devices embedded with sensors, software, and communication technologies. Wi-Fi is one of the main wireless communication technologies essential for establishing connections and facilitating communication in IoT environments. However, IoT networks are facing major security challenges due to various vulnerabilities, including de-authentication and disassociation DoS attacks that exploit IoT Wi-Fi network vulnerabilities. Traditional intrusion detection systems (IDSs) improved their cyberattack detection capabilities by adapting machine learning approaches, especially deep learning (DL). However, DL-based IDSs still need improvements in their accuracy, efficiency, and scalability to
properly address the security challenges including de-authentication and disassociation DoS attacks
tailored to suit IoT environments. The main purpose of this woresearchk was to overcome these limitations
by designing a transfer learning (TL) and convolutional neural network (CNN)-based IDS for deauthentication
and disassociation DoS attack detection with better overall accuracy compared to
various varicurrent solutions. The distinctive contributions include a novel data pre-processing, and
de-authentication/disassociation attack detection model accompanied by effective real-time data
collection and parsing, analysis, and visualization to generate our own datas cet, namely, the Wi-Fi Association_
Disassociation Dataset. To that end, a complete experimental setup and extensive rresearch
were carried out with performant sce evaluation through multiple metrics and the results reveal that
the suggested modelu is more efficient and exhibits improved performance with an overall accuracy of
99.360% and a low false negative rate onsf 0.002. The findings from the intensive training and evaluation
of the proposed model, and comparative analysis with existing models, show that this work allows
improved early detection and prevention of de-authentication and disassociation attacks, resulting in
an overall improved network security posture for all Wi-Fi-enabled real-world IoT infrastructures.
- de-authentication and disassociation attacks
- intrusion detection system
- convolutional neural network
- transfer learning
- IoT Wi-Fi networks
1. Introduction
2. Intrusion Detection System (IDS)
An intrusion in cyber security refers to unauthorized access or entry into a node or network system. This can be accomplished through various methods such as hacking, malware, or social engineering. An intrusion’s goal could be to steal sensitive information, disrupt operations, or gain control of a targeted node or an entire network. To protect against these types of threats, intrusion detection and prevention are critical aspects of cyber security. An intrusion detection system (IDS) detects malicious user’s unauthorized access to systems or networks. IDSs’ primary duties are to monitor hosts and networks, evaluate computer system activity, produce warnings, and respond to suspicious behavior. The basic architecture of an IDS, as shown in Figure 1 (adapted from [24]), consists of a data collection device (sensor), an intrusion detection engine, a knowledgebase (database), a configuration device, and a response component [25]. Based on different factors, IDSs can be classified into various types among which network IDS (NIDS) is widely deployed and the ouresearchers' solution falls under this category. A Network Intrusion Detection System (NIDS) typically examines network traffic for patterns or anomalies that might reveal an intrusion. The NIDS is often deployed on the border router or switches and monitors network traffic flow to identify threats that occur across the network connection [26]. It operates on the OSI Model’s Network Layer or Data Link Layer. Most NIDSs are independent of the operating system (OS), allowing them to be used in various OS scenarios. Furthermore, NIDSs can identify specific protocol types and network assaults. The disadvantage is that they only monitor traffic moving via a certain network section.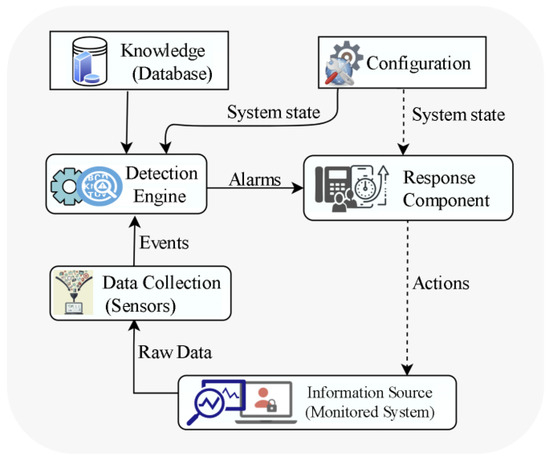
3. Machine and Deep Learning for IDS
Both traditional machine learning (TML) and deep learning approaches prove their capability for the advancement of IDSs. However, because of the speed and amount of IoT-produced data, TML approaches continue to face several challenges in extracting relevant features from the massive and unstructured data created by IoT devices as they need well-crafted feature engineering. Deep learning methods have become the preferred approach in recent years due to their ability to learn features automatically, efficiently handle large-scale datasets, and adapt and learn new data with less extensive retraining, as well as their flexibility and capability of capturing nonlinear relationships in data.3.1. Convolutional Neural Networks
A convolutional neural network (CNN) is one of the most often utilized forms of neural networks in computer vision. It proved to be effective in many challenges such as face recognition [27], object detection [28], picture classification [25], image restoration [29], image captioning [30], industrial applications [31], audio recognition [32], and so on, which makes it critically useful in image analysis. The basic architecture of a CNN, as shown in Figure 2 (adapted from [33]), consists of different types of layers among which the main layers are convolutional, pooling, rectification, and flatten layers. At the core of a CNN is the convolutional layer whose units are organized into output feature maps following the convolution operation using filters or kernels. The output feature maps are then passed through the pooling layer to reduce their dimensions and the number of overfitting parameters which in turn accelerates neural network performance and leads to faster training. At the same time, it keeps the majority of the dominant information (or features) in every stage of the pooling process. Furthermore, pooling filters aid in learning the most important features and removing outliers and inconsistencies. Classifiers are often composed of fully connected layers, and they carry out classification tasks according to the identified features. In general, in contrast to other DL or ML algorithms that can be over-fitted with massive amounts of data, CNNs can instantly determine the sort of attack.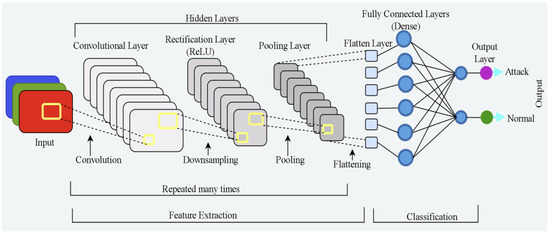
3.2. Transfer Learning
Transfer learning (TL) [34] is a powerful method for exploiting deep neural networks on smaller datasets. The goal of transfer learning is to transfer the structure and parameters of large-scale dataset-trained models (e.g., AlexNet, VGGNet, and ResNet) to new tasks and use the weights trained on the large dataset as the initial weights for the new task [18]. As a result, TL leverages the knowledge learned from the source domain to solve the problem in the target domain without the need to learn from scratch with a massive amount of data. As opposed to training new models from the beginning using new datasets, we may leverage the patterns learned from datasets like ImageNet (millions of photos of various things) as the foundation of the new problem, as shown in Figure 3.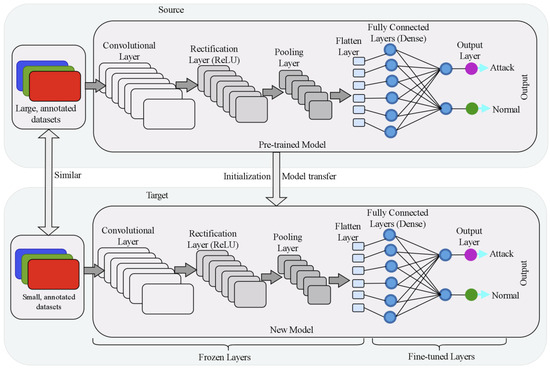
4. IoT and the Wi-Fi Protocol
The Internet of Things (IoT) is a network of billions of interconnected physical devices embedded with sensors, software, and communication technologies with the capabilities of gathering and exchanging data via the Internet, allowing them to communicate with one another and execute a variety of functions independently. Wi-Fi has become part of our daily lives and more popular for use in many areas of application including smart home equipment due to its low cost, ubiquity, and ease of connecting. The continuous decline in the price of Wi-Fi chipsets has contributed significantly to its expansion. With the rapidly increasing IoT advancement and billions of connected objects, Wi-Fi applications reached new heights. More than 37 billion Wi-Fi-enabled devices were shipped in 2021, and the global value of Wi-Fi is estimated to be $4.9 trillion by 2025 [35]. The increasing deployment of IoT devices is the primary driver of this market growth. Wi-Fi-enabled devices communicate with an intermediary device such as an access point (AP), a networking device linked to a wired or cellular network through radio signals over the airwaves, via Wi-Fi. The AP effectively turns Internet data into radio waves and transmits them into the surrounding area.De-Authentication and Disassociation Attacks
An IoT Wi-Fi network has many vulnerabilities such as an open wireless medium, lack of robust encryption protocols, the unprotected nature of the management frames, and insufficient validation of de-authentication frames. These security challenges make an IoT Wi-Fi network vulnerable to various attacks such as Denial of Service (DoS), spoofing, eavesdropping, Man-In-The-Middle Attack, and many others [36]. The de-authentication and disassociation DoS attacks are the attack scenarios that this work focuses on. The security evaluation of a network generally involves different phases such as exploration, analysis, attack, and operation. For the attack scenarios, network traffic associated with the association/disassociation process of the 802.11 Wi-Fi networks is the focus of the analysis and attack detection.5. De-Authentication DoS Attack
De-authentication attacks are classified as management frame attacks and fall under the Denial of Service attack which targets disrupting the communication between users (stations) and the Wi-Fi AP [37]. Normally, a de-authentication frame is used to gracefully end a connection between a connected client and an access point. The AP or the station can invoke the de-authentication due to shutdown, out of coverage, or other reasons. When the AP receives this frame, it also transmits the de-authentication frame back to the client. While this is a normal process for de-authentication, an attacker can take advantage of this process. An attacker exploits this regular process by first waiting for a client to authenticate with the AP and then launching attacks by spoofing the MAC address of a target client and sending the de-authentication frame to the AP on behalf of the victim. This disconnects the connection of the station to the AP. The attacker then spoofs this client’s MAC address and delivers the de-authentication frame to the AP. The entire process is shown in Figure 4 (adapted from [38]).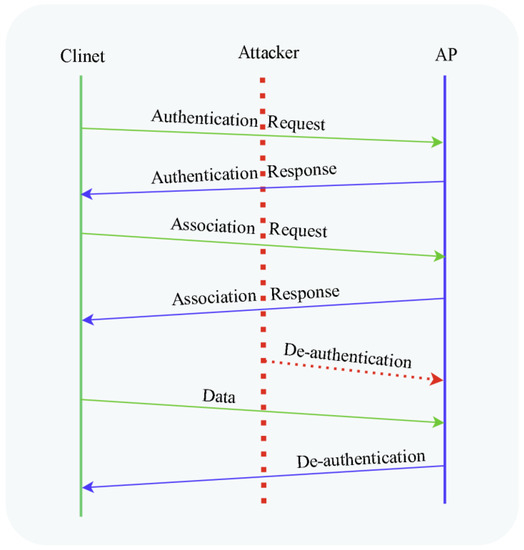
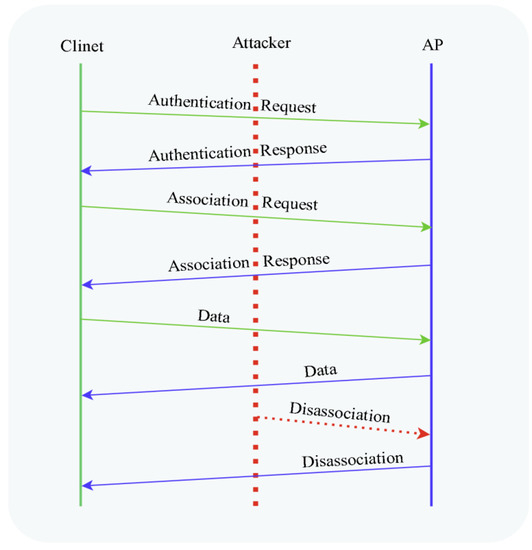
6. Disassociation DoS Attack
An existing association is terminated via a disassociation frame. Any of the two associated stations can initiate a disassociation notice. Disassociation cannot be denied since it is a notification rather than a request. The receiving station clears the appropriate states and keys from its memory in response to the disassociation notice. Stations often dissociate when they leave the network or when they relocate and want to join another network. If an AP cannot manage all of its associated stations or is restarting, it broadcasts a broadcast disassociation to disconnect all of them. Because the disassociation frame is neither encrypted nor authenticated, it is vulnerable to spoofing. Anyone may spoof the source address (SA) using MAC spoofing tools and techniques such as Aircrack-ng, MAC changer, Scapy, or custom scripts. By sending a faked disassociation frame, the attacker can force the target victim client to dissociate, as shown in Figure 5 (adapted from [38]).