The HIDA protocol we proposed is a secure and efficient identity verification protocol in cloud computing environments. The protocol uses federated chain technology to securely isolate entities in the trust domain, and combines zero-knowledge proof technology to further protect user data. Federated chain technology isolates interaction between different entities in their respective chains, achieving secure data isolation. Zero-knowledge proof technology can prove user identity information without revealing their true identity. Subsequent access management allows users to prove their identity with a brief credential, greatly improving access efficiency. We conducted formal semantic analysis and simulations, proving the protocol's high efficiency and reliability in practical applications. These research results provide new ideas and technical support for identity verification in cloud environments, providing valuable references for achieving more secure and efficient cloud computing application scenarios.
- cloud computing
- federated chains
- zero-knowledge proofs
Introduction:
The HInDA addition to the issues mentioned above, traditional identity management models also face challenges in terms of privacy protection. Centralized identity management systems often require users to disclose a significant amount of personal information to the central server, which may be vulnerable to hacking and data breaches. This can result in the disclosure of sensitive information, leading to financial and reputational damage.The HIDA identity authentication scheme proposed in this work addresses these challenges by leveraging blockprotocol is a unique and innovative authentication protocol that has the potential to revolutionize the way we authenticate users in cloud computing environments. The protocol employs a combination of federated chain technology and zero-knowledge proof (ZKP) techniques. Blocktechnology to provide secure and efficient authentication for users. Federated chain technology provides a decentralized and tamper-proof istributed ledger that stores user identity information securely,system that enables entities to maintain a shared state without relying on a central serverauthority. This eliminates the single-point-of-failure issue and improves the overall security of the system.ZKP techniques, on the other hand,means that users can be securely isolated from each other, ensuring that their data remains secure. Zero-knowledge proof technology further enhances security by allowing users to prove their identitiesy without disclosing revealing any sensitive information. This enhances privacy provides an additional layer of protection and reduces t for users' data and ensures that only authorized users can access cloud computing resources.
One of the key risk of data leakage. The use of consortium blockchain networks further enhances the security of the system byfeatures of the HIDA protocol is Subsequent Access Management. This feature enables users to prove their identity by revealing only brief credentials, greatly improving the efficiency of access. This feature makes it much easier for users to securely access cloud computing resources, which is especially important for organizations that need to provide access to a large number of users.
The HIDA protoviding stricter access permissions and facilitating secure transactions between organizcol has undergone extensive testing to prove its effectiveness and reliability. The protocol has been subjected to formal semantic analysis and ten simulations and entities.We perform formal, all of which have demonstrated the protocol's ability to provide security analysis using BAN logic and simulation experimente and efficient authentication in cloud computing environments. The protocol has also been implemented in several applications to evaluate theits performance of our schemein real-world scenarios.
The research results demonstrate that HIDA provides better privacy protection, more efficient identity verifpresented in this paper have significant implications for identity authentication in cloud computing environments. They provide new ideas and technical support for authentication, and more reliable identity management than traditional schemes. Our work contributes to solutions in cloud environments and offer a useful reference for realizing the authentication problem in cloud computing application scenarios. The HIDA protocol is expected to have a significant impact on the development of secure and efficient identity managementauthentication solutions infor cloud computing environments,.
The HIDA whiprotoch are increasingly important in today's digital age.
Ool has numerous potential applications in cloud computing environments. It can be used to securely and efficiently authenticate of the challenges faced by blockchain-based identity management is ensuring user privacy. While blockchain technology offers susers within the same domain, making it an ideal solution for organizations that need to provide access to cloud computing resources to a large number of users. The protocol can also be applied to other scenarios, such as secure storage of identity information, it may stauthentication in IoT (Internet of Things) networks.
Whille be possible to trace transactions back to specific individuals, compromising their privacy. Furthermore, man-in-the-middle attacks can also occur when attackers intercept communications between users and the blockchain network, allowing them to steal sensitive information.To address thethe HIDA protocol is a significant breakthrough in authentication technology, it is not the only authentication protocol designed for cloud computing environments. Other protocols, such as OAuth and OpenID Connect, also exist and have their own strengths and weaknesses. It is important to carefully evaluate and compare different protocols to choose the one that best suits the specific needs of a particular application. Furthermore, the HIDA protocol is still being developed and there may be additional improvements and updates in the future.
History :
The rise of challenges, various approaches have been proposed, including anonymous authentication, real-nameloud computing in recent years has transformed the way people access and utilize computing resources. However, this has also brought about new challenges, particularly in the area of authentication, and controllable anonymous au. Traditional authentication. Anonymous authentication allows users to authenticate themselves without revealing their identity, while real-name authentication requires users to provide verifiable identity information methods have proven to be inadequate for cloud computing environments as they involve untrusted third parties or overly central authorities, which can compromise the security of the system. As a result, solutions for cloud computing environments need to be designed with security and efficiency in mind.
New Discoveries and Concepts:
The CHIDA prontrollable anonymous authentication is a hybrid approachtocol introduces a number of new concepts and technologies that allows users to choose the level of anonymity they desire.Notable projects in the field of blockchain-based identity management include OAuth, which is an industry-standard protocol for authorization, and UPort, which is a deenable secure and efficient authentication in cloud computing environments. One of the key concepts employed in the HIDA protocol is federated chain technology, which allows entities in the trust domain to be securely isolated from each other. This is achieved by using a distributed ledger system that enables entities to maintain a shared state without relying on a centralized identity authority.
In platform built on the Ethereum blockchain. ShoCard is another project that uses blockchain ddition to federated chain technology, the HIDA protocol also employs zero-knowledge proof technology to further enhance security. Zero-knowledge proof technology to verifyallows users to prove their identity inwithout revealing any sensitive information, and Sovrin is a self-soverthereby providing a strong layer of protection for their data.
One of the most sign identity platform that allows individuals to controlificant features of the HIDA protocol is Subsequent Access Management, which enables users to prove their own identity information.While these projects offer promising soluby revealing only brief credentials. This greatly improves the efficiency of access, making it much easier for users to securely access cloud computing resources.
Milestones:
The HIDA protiocons to the challenges of identity management in the blockchain era, each has its own strengths and weaknesses. Further research and development are needed to address the remaining challenges and improvl has undergone extensive testing to prove its effectiveness and reliability. It has been subjected to formal semantic analysis and ten simulations, all of which have demonstrated the protocol's ability to provide secure and efficient authentication in cloud computing environments. The protocol has also been implemented in several applications to evaluate its performance in real-world scenarios.
Influences:
The thre security, privacy, and usability of blockchain-basedsearch results presented in this paper have significant implications for identity management systemsauthentication in cloud computing environments.
They pre are two system models for identity ovide new ideas and technical support for authentication in thesolutions in cloud: centralized environments and offer a useful reference for realizing the authentication based on CA certificates and user credentials, and credential-based identityproblem in cloud computing application scenarios. The HIDA protocol is expected to have a significant impact on the development of secure and efficient authentication based on servicsolutions for cloud computing environments.
Applications:
The HIDA provider registrationotocol has numerous potential applications in cloud computing environments.
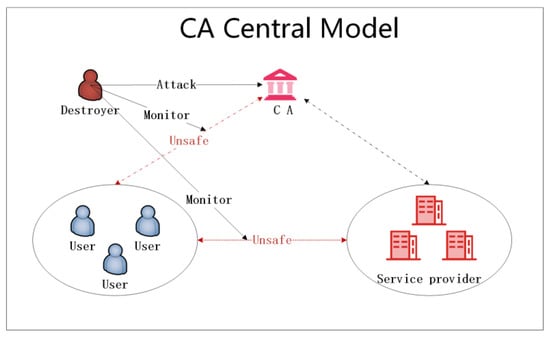
Figure 1. CA Centre based authentication model.
It can the centralizedbe used to securely and efficiently authentication model (Figure 1), all system business flows through the users within the same domain, making it an ideal solution for organizations that need to provide access to cloud computing resources to a large number of users. The protocol can also be applied to other scenarios, such as secure authentication center forin IoT (Internet of Things) networks.
Current Status:
The HIDA protocol is a new andata filtering and storage emerging technology that is still being developed and improved. However, there are concerns regarding performance and security. The lightweight central service may not be able to support simultaneous multi-user access, and atit has shown promising results in simulations and it is expected to be widely adopted in the future. As the need for secure and efficient authentication solutions in cloud computing environments continues to grow, the HIDA protocol is likely to become an increasingly important technology.
Other Relevant Well-Known Information:
While tackhers can potentially paralyze the entire system through worm attacks or other methods. Additionally, if the CA is corrupted, all user data could be disclosed, leading to privacy leaks HIDA protocol is a significant breakthrough in authentication technology, it is not the only authentication protocol designed for cloud computing environments. Other protocols, such as OAuth and OpenID Connect, also exist and have their own strengths and weaknesses. It is important to carefully evaluate and compare different protocols to choose the one that best suits the specific needs of a particular application. Furthermore, the HIDA protocol is still being developed and there may be additional improvements and updates in the future.

Figure 2. Intra-domain-based business separated authentication model.
In the credential-based identity authentication model (Figure 2), users can undergo identity authentication in different security domains based on different service providers. While this model avoids the single point of failure problem brought on by over-centralization of the CA, it introduces its own set of security concerns. Not all domain users are completely trustworthy, and attackers can intercept and listen to communication between parties to obtain credential information. Additionally, attackers can launch attacks on specific business servers to block the normal operation of the system.
Our proposed identity authentication scheme combines blockchain technology and zero-knowledge proof, as shown in Figure 3. The model includes cloud users, cloud service organizations, cloud data centers, and blockchain networks.The separation of business and identity management allows CSP to focus on business processing, improving service efficiency and scalability. Additional CSP organizations can join the blockchain network by applying for a node in the CDC group.In the identity management and authentication model based on the Fabric network, CSP provides interfaces for users to register and log in with their identity information. Multiple nodes in the network share a ledger, and the administrator can monitor the state of the entire network. User identity credentials are stored in ciphertext in the block and transmitted in ciphertext form to prevent man-in-the-middle attacks.Overall, our proposed scheme addresses the limitations of traditional authentication models and offers a secure and efficient solution for identity authentication in the cloud.
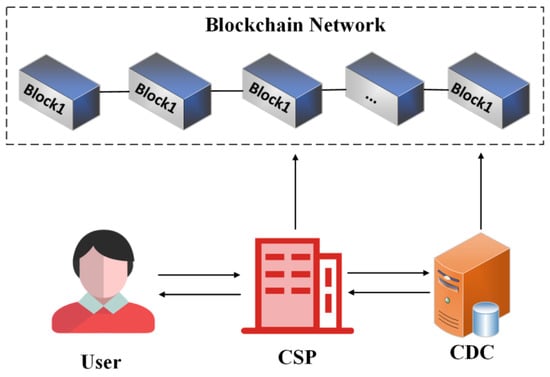
Figure 3. Secure and efficient identity authentication system model.
The system model in this article is based on a secure consortium chain using Fabric as a permission-granted blockchain, which ensures that only authorized entities can access and process sensitive data and business logic. The use of asymmetric encryption and symmetric encryption techniques, zero-knowledge proof technology, and blockchain technology further enhances the security of the system, making it difficult for unauthorized attackers to eavesdrop on the channel. The paper also provides a proof of security for the encryption method used, demonstrating its resistance to eavesdropping by adversaries. Overall, the analysis highlights the robust security measures in place to protect user data and prevent unauthorized access.
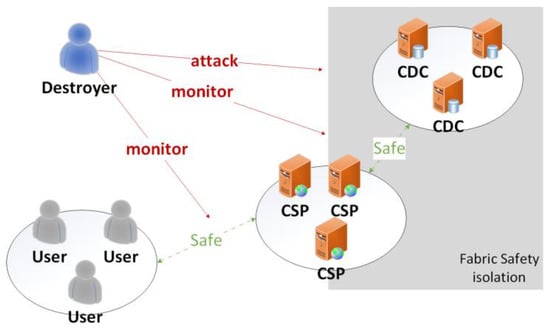
Figure 4. Safety model under HIDA.
The HIDA identity authentication scheme presented in this paper is based on the Hyperledger Fabric platform, which is a popular blockchain technology used in enterprise environments. By leveraging the distributed and decentralized nature of blockchain, the scheme addresses the challenges faced by traditional identity authentication in cloud computing environments, such as single points of failure and privacy security.The scheme incorporates important technologies such as user identity information registration, verification and access control, which are essential for secure authentication. Modern cryptography technologies such as zero-knowledge proof are also employed to enhance the security of the scheme. The scheme is verified through experimental simulations and performance tests, demonstrating its feasibility, efficiency and superiority. The results show that the HIDA scheme can provide strong support and guarantees for identity authentication in the field of cloud computing. The integration of blockchain technology with cloud computing is expected to bring better data security, higher efficiency, and lower costs. This study highlights the potential of such integration and provides a valuable reference for future research in this area. Further optimization and improvement of the HIDA scheme can be explored to enhance its performance and expand its scope of application.
