AThis entry refers to a reliable and lightweight trusted access authentication solution for systems with large-scale heterogeneous terminals was introduced. By cloud, edge, and local servers cooperating to execute authentication tasks, the cloud-edge-end collaborative architecture effectively alleviates the authentication delay caused by high concurrent requests. Each server in the architecture deploys a well-designed unified trusted access authentication (UATT) model based on device fingerprints. With ingenious data construction and powerful swin-transformer network, UATT model can provide robust and low-overhead authentication services for heterogeneous terminals. To minimize authentication latency, an A2C-based authentication task scheduling scheme is used to decide which server executes the current task.
- trusted access
- device fingerprint
- end-edge-cloud collaboration
1. Introduction
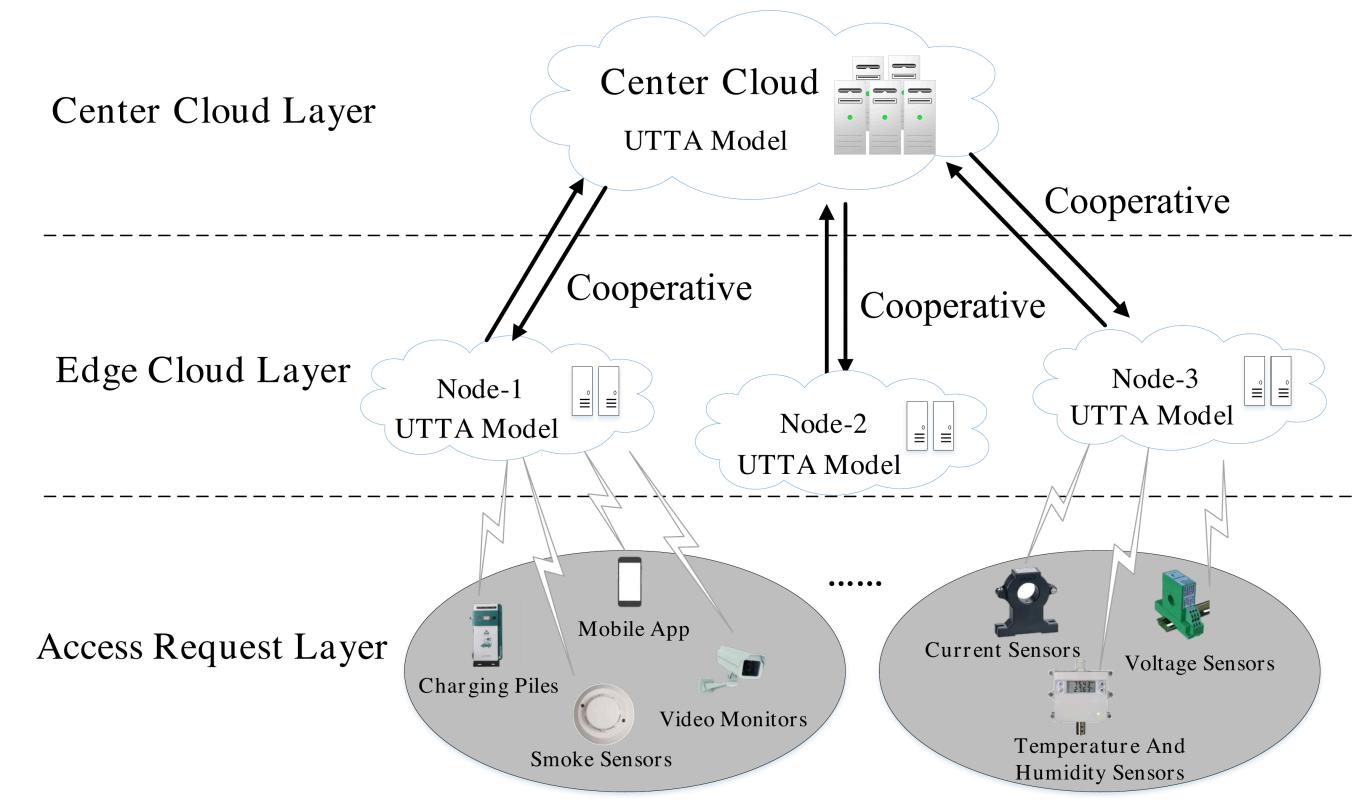
2. End-Edge-Cloud Cooperation framework
3. Unified Trusted Access Authentication (UTAA) Model
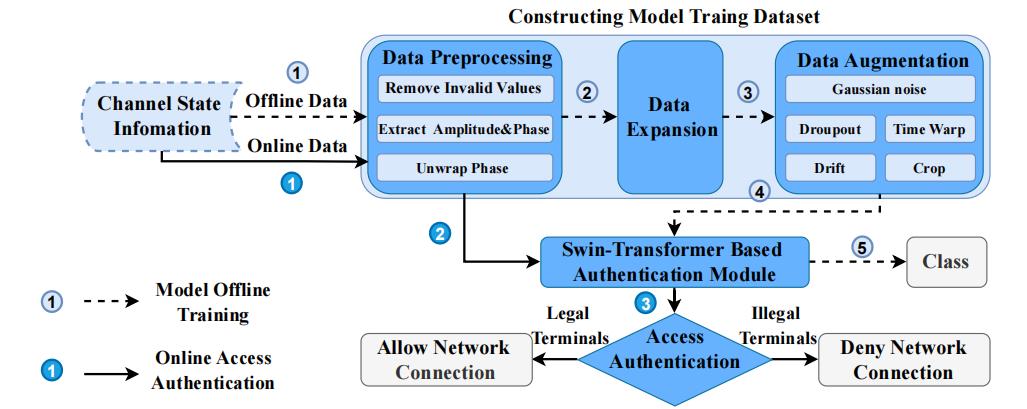
To address the limitations of the current device fingerprint-based authentication, a unified trusted access authentication (UTAA) model is proposed. As shown in Fig.2, UTAA model contains two key stages i.e., model offline training and online access authentication. Before being deployed in practical vehicle networking charged system to process online access authentication tasks, researchers need to train a robust Swin-Transformer based authentication module at the model offline training stage. As shown in Fig.2, the different steps of model offline training stage are connected by the dotted arrows. researchers first collect the channel state information (CSI) from different terminals. Then after the process of data preprocessing, data expansion and data augmentation in the step of constructing model training dataset, researchers will obtain diverse and sufficient input samples to train a robust and lightweight Swin-Transformer based authentication module.
The arrows with solid line represent the steps of online access authentication stage in Figure 2Fig.2. The well-trained Swin-Transformer based authentication module will be deployed in all the edge cloud nodes and the center cloud layer of the practical vehicle networking charged system. Once an access authentication request generates from a terminal, UTAA model collects its channel state information (CSI) from the wireless signal between the terminal and the authentication nodes. After the step of data preprocessing, the valid phase and amplitude information are extracted from CSI and will be input to the Swin-Transformer based authentication module for correct access authentication.
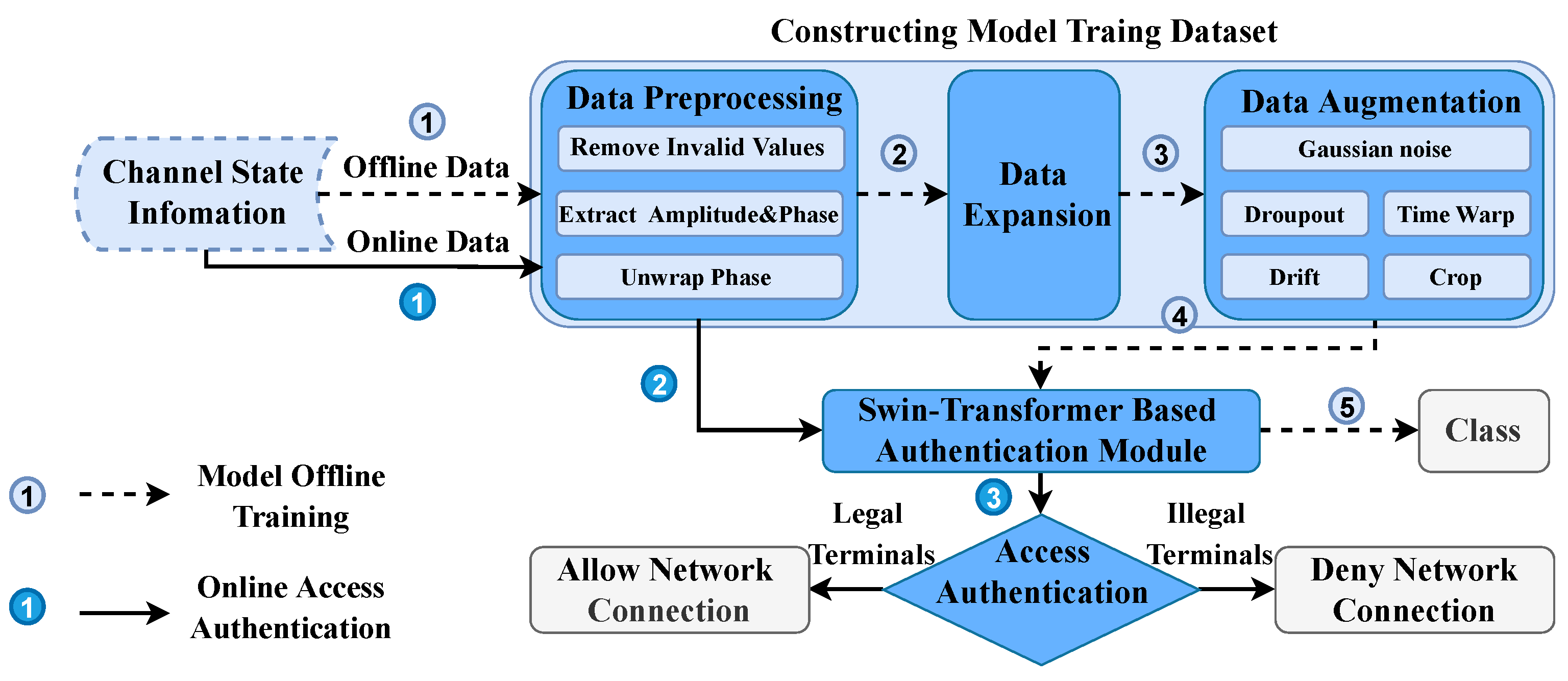
Figure 2. The Unified Trusted Access Authentication (UTAA) Model.
Unlike previous studies [12][13][14] [12]that only manually extracted a single feature from the amplitude or phase information of CSI, researchers aim to extract unforgeable and robust hardware features from the amplitude and phase of the CSI as device fingerprints. By integrating with the vehicle networking charged system, the Swin-Transformer based terminal authentication scheme can provide bi-directional authentication between the charging system heterogeneous sensor terminals and edge nodes. It effectively reduces the security risks of existing authentication mechanisms. Moreover, the solution requires only a small number of packets to authenticate the access of a single terminal. This greatly eases the computational overhead of access authentication and reduces the network burden.
4. End-Edge-Cloud Cooperative Authentication Task Scheduling
Though UTAA model optimizes the authentication delay of a single terminal, the authentication response time overhead for vehicle networking charged system with massive terminal access is still extremely heavy. In order to alleviate the authentication pressure, the authentication task can be delivered to the center cloud nodes with sufficient computing and storage resources for processing. But it is difficult for the center cloud node, which is small in number and far away from the terminal, to process dynamic numerous authentication requests in real time. Besides, the number of edge nodes is large and close to the terminal, but it is difficult to handle high concurrent authentication tasks due to their less computing and storage resources. To provide efficient authentication services for vehicle networking charged system, researchers therefore consider a distributed end-edge-cloud collaborative solution that combines the advantages of cloud nodes and edge nodes. By dynamically offloading the authentication task to appropriate nodes, the solution is able to minimize the global authentication response time overhead.
To dynamically solve the optimal authentication task scheduling scheme, researchers model the end-edge-cloud collaborative solution in advance. As illustrated in Fig.1, researchers consider a trusted access authentication architecture consisting of a set of terminals that initiate authentication requests, a series of edge nodes with certain computing resources, one remote cloud node with sufficient computing resources, and local computing node in vehicle networking charged system. Each edge node, cloud node, and local node is deployed with UTTA model for authenticating whether the terminal is trusted. And only trusted terminals are allowed to access. Accordingly, researchers mathematically formulate the problem of minimizing the authentication response latency and solve it based on the A2C algorithm.[5]
References
- Saeed, Mamoon M; Hasan, Mohammad Kamrul; Obaid, Ahmed J; Saeed, Rashid A; et al. A comprehensive review on the users’ identity privacy for 5G networks. IET Communications 2022, 16, 384--399.
- Cai, Ting; Yang, Zetao; Chen, Wuhui; Zheng, Zibin; Yu, Yang A blockchain-assisted trust access authentication system for solid. IEEE Access 2020, 8, 71605--71616.
- Yao, Su; Guan, Jianfeng; Wu, Yinan; Xu, Ke; Xu, Mingwei Toward secure and lightweight access authentication in SAGINs. IEEE Wireless Communications 2020, 27, 75--81.
- Gupta, Rajesh; Reebadiya, Dakshita; Tanwar, Sudeep; Kumar, Neeraj; Guizani, Mohsen When blockchain meets edge intelligence: Trusted and security solutions for consumers. IEEE Network 2021, 35, 272--278.
- Chen, Yuxiang; Dong, Guishan; Bai, Jian; Hao, Yao; Li, Feng; Peng, Haiyang, Trust enhancement scheme for cross domain authentication of PKI system, in Proceedings 2019 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC)
- Aghabagherloo, Alireza; Delavar, Mahshid; Mohajeri, Javad; Salmasizadeh, Mahmoud; Preneel, Bart An efficient and physically secure privacy-preserving authentication scheme for Vehicular Ad-hoc NETworks (VANETs). IEEE Access 2022, 10, 93831--93844.
- Tan, Haowen; Zheng, Wenying; Guan, Yunguo; Lu, Rongxing A Privacy-Preserving Attribute-Based Authenticated Key Management Scheme for Accountable Vehicular Communications. IEEE Transactions on Vehicular Technology 2022, xx, xx.
- Qiu, Han; Qiu, Meikang; Lu, Ruqian Secure V2X communication network based on intelligent PKI and edge computing. IEEE Network 2019, 34, 172--178.
- Li, Fengyin; Liu, Zhongxing; Li, Tao; Ju, Hongwei; Wang, Hua; Zhou, Huiyu Privacy-aware PKI model with strong forward security. International Journal of Intelligent Systems 2022, 37, 10049--10065.
- Hua, Jingyu; Sun, Hongyi; Shen, Zhenyu; Qian, Zhiyun; Zhong, Sheng, in Proceedings IEEE INFOCOM 2018-IEEE Conference on Computer Communications, 2018.
- Liu, Pengfei; Yang, Panlong; Song, Wen-Zhan; Yan, Yubo; Li, Xiang-Yang, Real-time identification of rogue WiFi connections using environment-independent physical features, in Proceedings IEEE INFOCOM 2019-IEEE Conference on Computer Communications, 2019.
- Lin, Yuxiang; Gao, Yi; Li, Bingji; Dong, Wei, Accurate and robust rogue access point detection with client-agnostic wireless fingerprinting, in Proceedings 2020 IEEE International Conference on Pervasive Computing and Communications (PerCom), 2020.
- Hua, Jingyu; Sun, Hongyi; Shen, Zhenyu; Qian, Zhiyun; Zhong, Sheng, Accurate and efficient wireless device fingerprinting using channel state information, in Proceedings IEEE INFOCOM 2018-IEEE Conference on Computer Communications, 2018.
- Liu, Pengfei; Yang, Panlong; Song, Wenzhan; Yan, Yubo; Li, Xiangyang, Real-time identification of rogue WiFi connections using environment-independent physical features, in Proceedings IEEE INFOCOM 2019-IEEE Conference on Computer Communications, 2019.
